Here's a link in using the packet capture tool or sniffer in a FortiGate firewall.
To perform packet capture in FortiGate, select a VDOM: internet > Network > Diagnostics > select Interface: Internet (wan) > Packet Capture.
You can optionally enable/toggle Filters to narrow down Host, Port and Protocol number.
I've used the switch SVI to perform ping test from the "inside" LAN.
SW01#show ip interface brief
Interface IP-Address OK? Method Status Protocol
Vlan1 unassigned YES NVRAM up up
Vlan300 172.x.x.5 YES manual up up
FastEthernet0/1 unassigned YES unset up up
<OUTPUT TRUNCATED>
SW01#ping 8.8.8.8 source 172.x.x.5
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 8.8.8.8, timeout is 2 seconds:
Packet sent with a source address of 172.x.x.5
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/5/9 ms
Enable/toggle Filters > select Filtering syntax: Basic (default) > type Host: 172.x.x.5 > click Start Capture.
You can observe the Packet Capture in FortiGate web GUI or click Save as pcap for offline analysis.
The .pcap file will be saved under Downloads folder (in Windows).
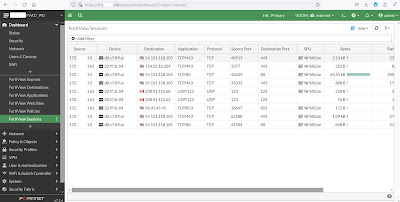
To view the current FortiGate IP sessions (5-tuple), go to Dashboard > FortiView Sessions.
To view in CLI, you can use the get system session list command. Use grep to filter the command output.
FG-FW01_PRI # config vdom
FG-FW01_PRI (vdom) # edit internet
current vf=internet:4
FG-FW01_PRI (internet) # get system session list | grep 172.x.x.5
tcp 3576 172.x.x.5:49269 202.x.x.30:49269 54.151.118.105:443 -
tcp 3599 172.x.x..5:43013 202.x.x.30:43013 104.82.75.211:80 -
icmp 29 172.x.x.5:10 202.x.x.30:60426 8.8.8.8:8 -
tcp 3564 172.x.x.5:29031 202.x.x.30:29031 54.151.118.105:443
Here's a link in using the debug flow tool in a FortiGate firewall.
There's no equivalent packet-tracer command in FortiGate which generates a virtual packet to verify routing, ACL and NAT similar to Cisco ASA firewall. To find the matching Firewall Policy rule, use Debug Flow or diagnose debug flow CLI command:
Go to VDOM: internet > Network > Diagnostics > Debug flow tab.
Type the number of packets (count): 100 (default) > enable/toggle Filters > select Filter type: Basic (default) > select IP type: IPv4 (default) > type IP address: 8.8.8.8 > select Protocol: ICMP.
Click
Start debug flow.
Generate packets to capture. Click Stop debug flow when finished.
SW01#ping 8.8.8.8 source 172.x.x.5 repeat 100
Type escape sequence to abort.
Sending 100, 100-byte ICMP Echos to 8.8.8.8, timeout is 2 seconds:
Packet sent with a source address of 172.x.x.5
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
Success rate is 100 percent (100/100), round-trip min/avg/max = 1/4/9 ms
You can view offline or save as CSV file.
Notice policy-2 is matched and SNAT (Source NAT) is used.
Below are the diagnose debug CLI commands:
diagnose debug reset // CLEAR ALL DIAGNOSE SETTINGS
diagnose debug flow filter addr <SOURCE OR DESTINATION IP> // BY DEFAULT THERE'S NO FILTER, DEFINE OR NARROW DOWN SPECIFIC IP
diagnose flow trace start <PACKET COUNT>
diagnose debug enable // TURN ON DEBUG
diagnose debug disable // TURN OFF DEBUG, SIMILAR TO CISCO'S undebug all
FG-FW01_PRI # config vdom // GO TO A VDOM
FW01_PRI (vdom) # edit internet
current vf=internet:4
FW01_PRI (internet) # diagnose debug reset
FW01_PRI (internet) # diagnose debug flow
filter Trace packet with filter.
filter6 Trace packet with IPv6 filter.
trace Start/stop trace.
show Enable/disable display of trace on console.
FW01_PRI (internet) # diagnose debug flow filter
clear Clear filter.
vd Index of virtual domain.
vd-name Name of virtual domain.
proto Protocol number.
addr IP address.
saddr Source IP address.
daddr Destination IP address.
port port
sport Source port.
dport Destination port.
negate Inverse filter.
FW01_PRI (internet) # diagnose debug flow filter addr
<xxx.xxx.xxx.xxx> Host IP (ip1/from).
FW01_PRI (internet) # diagnose debug flow filter addr 8.8.8.8
FW01_PRI (internet) # diagnose debug flow trace
start Start trace.
stop Stop trace.
start6 Start IPv6 trace.
stop6 Stop IPv6 trace.
FW01_PRI (internet) # diagnose debug flow trace start
<xxx> Repeat number.
FW01_PRI (internet) # diagnose debug flow trace start 100
FW01_PRI (internet) # diagnose debug enable
FW01_PRI (internet) # id=65308 trace_id=5 func=print_pkt_detail line=5868 msg="vd-internet:0 received a packet(proto=1, 172.x.x.5:13->8.8.8.8:2048) tun_id=0.0.0.0 from LAG1-INSIDE. type=8, code=0, id=13, seq=0."
id=65308 trace_id=5 func=init_ip_session_common line=6049 msg="allocate a new session-0026c30d, tun_id=0.0.0.0"
id=65308 trace_id=5 func=vf_ip_route_input_common line=2605 msg="find a route: flag=04000000 gw-202.x.x.1 via wan"
id=65308 trace_id=5 func=__iprope_tree_check line=524 msg="gnum-100004, use int hash, slot=53, len=3"
id=65308 trace_id=5 func=get_new_addr line=1228 msg="find SNAT: IP-202.x.x.30(from IPPOOL), port-60429"
id=65308 trace_id=5 func=fw_forward_handler line=922 msg="Allowed by Policy-2: SNAT"
id=65308 trace_id=5 func=ids_receive line=428 msg="send to ips"
id=65308 trace_id=5 func=__ip_session_run_tuple line=3485 msg="SNAT 172.x.x.5->202.x.x.30:60429"
id=65308 trace_id=6 func=print_pkt_detail line=5868 msg="vd-internet:0 received a packet(proto=1, 8.8.8.8:60429->202.x.x.30:0) tun_id=0.0.0.0 from wan. type=0, code=0, id=60429, seq=0."
id=65308 trace_id=6 func=resolve_ip_tuple_fast line=5956 msg="Find an existing session, id-0026c30d, reply direction"
id=65308 trace_id=6 func=__ip_session_run_tuple line=3498 msg="DNAT 202.x.x.30:0->172.x.x.5:13"
id=65308 trace_id=6 func=vf_ip_route_input_common line=2605 msg="find a route: flag=00000000 gw-172.x.x.5 via LAG1-INSIDE"
id=65308 trace_id=6 func=npu_handle_session44 line=1199 msg="Trying to offloading session from wan to LAG1-INSIDE, skb.npu_flag=00000000 ses.state=00010204 ses.npu_state=0x04001008"
id=65308 trace_id=6 func=fw_forward_dirty_handler line=414 msg="state=00010204, state2=00000001, npu_state=04001008"
id=65308 trace_id=7 func=print_pkt_detail line=5868 msg="vd-internet:0 received a packet(proto=1, 172.x.x.5:13->8.8.8.8:2048) tun_id=0.0.0.0 from LAG1-INSIDE. type=8, code=0, id=13, seq=1."
id=65308 trace_id=7 func=resolve_ip_tuple_fast line=5956 msg="Find an existing session, id-0026c30d, original direction"
id=65308 trace_id=7 func=npu_handle_session44 line=1199 msg="Trying to offloading session from LAG1-INSIDE to wan, skb.npu_flag=00000400 ses.state=00010204 ses.npu_state=0x04001008"
id=65308 trace_id=7 func=ip_session_install_npu_session line=358 msg="npu session installation succeeded"
id=65308 trace_id=7 func=fw_forward_dirty_handler line=414 msg="state=00010204, state2=00000001, npu_state=04001408"
id=65308 trace_id=7 func=__ip_session_run_tuple line=3485 msg="SNAT 172.x.x.5->202.x.x.30:60429"
id=65308 trace_id=8 func=print_pkt_detail line=5868 msg="vd-internet:0 received a packet(proto=1, 8.8.8.8:60429->202.x.x.30:0) tun_id=0.0.0.0 from wan. type=0, code=0, id=60429, seq=1."
id=65308 trace_id=8 func=resolve_ip_tuple_fast line=5956 msg="Find an existing session, id-0026c30d, reply direction"
id=65308 trace_id=8 func=__ip_session_run_tuple line=3498 msg="DNAT 202.x.x.30:0->172.x.x.5:13"
id=65308 trace_id=8 func=npu_handle_session44 line=1199 msg="Trying to offloading session from wan to LAG1-INSIDE, skb.npu_flag=00000400 ses.state=00010204 ses.npu_state=0x04001408"
id=65308 trace_id=8 func=ip_session_install_npu_session line=358 msg="npu session installation succeeded"
id=65308 trace_id=8 func=fw_forward_dirty_handler line=414 msg="state=00010204, state2=00000001, npu_state=04001c08"
FW01_PRI (internet) # diagnose debug disable
You can use the Policy lookup tool (with magnifying glass icon) under Firewall Policy.
Select Incoming Interface: LAG1-INSIDE > select IP Version (IPv4 by default) > select Protocol: TCP (default) > type Source: 172.x.x.5 > type Destination: 8.8.8.8 > type Destination Port: 8 (ICMP request) > click Search.
The matching Firewall Policy will be selected/highlighted in red.