We've been using Cisco AnyConnect to VPN back to our corporate network and intranet resources. It gives the same experience as the Cisco's legacy VPN client and also ties back to our Active Directory (AD) profile which allows for single sign-on (SSO). VPN has many flavors and below is one of them, which is the remote access SSL VPN lab that I did on my Cisco ASA 5505 firewall.
Router(config-if)#hostname R1
R1(config)#ip route 0.0.0.0 0.0.0.0 serial0/0/0
R1(config)#interface fastethernet0/0
R1(config-if)#ip address 209.165.200.225 255.255.255.248
R1(config-if)#no shutdown
R1(config-if)#
*Jul 5 03:17:49.787: %LINK-3-UPDOWN: Interface FastEthernet0/0, changed state to up
*Jul 5 03:17:50.787: %LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet0/0, changed state to up
R1(config-if)#interface serial0/0/0
R1(config-if)#ip address 10.1.1.1 255.255.255.252
R1(config-if)#no shutdown
R1(config-if)#
*Jul 5 03:18:07.115: %LINK-3-UPDOWN: Interface Serial0/0/0, changed state to down
R1(config-if)#clock rate 64000
Router(config)#hostname R2
R2(config)#interface serial0/0/0
R2(config-if)#ip address 10.1.1.2 255.255.255.252
R2(config-if)#no shutdown
R2(config-if)#
*Jul 5 03:17:55.143: %LINK-3-UPDOWN: Interface Serial0/0/0, changed state to up
*Jul 5 03:17:56.143: %LINEPROTO-5-UPDOWN: Line protocol on Interface Serial0/0/0, changed state to up
R2(config-if)#do ping 10.1.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.1.1.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 28/28/32 ms
R2(config-if)#interface serial0/0/1
R2(config-if)#ip address 10.2.2.2 255.255.255.252
R2(config-if)#no shutdown
R2(config-if)#
*Jul 5 03:18:17.699: %LINK-3-UPDOWN: Interface Serial0/0/1, changed state to down
R2(config-if)#clock rate 64000
R2(config-if)#exit
R2(config)#ip route 209.165.200.224 255.255.255.248 serial0/0/0
R2(config)#ip route 172.16.3.0 255.255.255.0 serial0/0/1
Router(config)#hostname R3
R3(config)#interface fastethernet0/1
R3(config-if)#ip address 172.16.3.1 255.255.255.0
R3(config-if)#no shutdown
R3(config-if)#
*Jul 5 03:22:00.983: %LINK-3-UPDOWN: Interface FastEthernet0/1, changed state to up
*Jul 5 03:22:01.983: %LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet0/1, changed state to up
R3(config-if)#interface serial0/0/1
R3(config-if)#ip address 10.2.2.1 255.255.255.252
R3(config-if)#no shutdown
R3(config-if)#
*Jul 5 03:22:24.015: %LINK-3-UPDOWN: Interface Serial0/0/1, changed state to up
*Jul 5 03:22:25.015: %LINEPROTO-5-UPDOWN: Line protocol on Interface Serial0/0/1, changed state to up
R3(config-if)#do ping 10.2.2.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.2.2.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 28/28/28 ms
R3(config-if)#exit
R3(config)#ip route 0.0.0.0 0.0.0.0 serial0/0/1
R1(config)#ip http server
R1(config)#enable password cisco
R1(config)#line vty 0 4
R1(config-line)#password cisco
R1(config-line)#login
R1(config)#line console 0
R1(config-line)#password cisco
R1(config-line)#login
Switch(config)#hostname S1
Switch(config)#hostname S2
Switch(config)#hostname S3
ciscoasa> enable
Password: <ENTER>
ciscoasa# conf t
ciscoasa(config)#
***************************** NOTICE *****************************
Help to improve the ASA platform by enabling anonymous reporting,
which allows Cisco to securely receive minimal error and health
information from the device. To learn more about this feature,
please visit: http://www.cisco.com/go/smartcall
Would you like to enable anonymous error reporting to help improve
the product? [Y]es, [N]o, [A]sk later: n
In the future, if you would like to enable this feature,
issue the command "call-home reporting anonymous".
Please remember to save your configuration.
ciscoasa(config)# hostname CCNAS-ASA
CCNAS-ASA(config)# domain-name ccnasecurity.com
CCNAS-ASA(config)# enable password cisco
CCNAS-ASA(config)# passwd cisco
CCNAS-ASA(config)# interface ethernet0/0
CCNAS-ASA(config-if)# switchport access vlan 2
CCNAS-ASA(config-if)# no shutdown
CCNAS-ASA(config-if)# interface ethernet0/1
CCNAS-ASA(config-if)# switchport access vlan 1
CCNAS-ASA(config-if)# no shutdown
CCNAS-ASA(config-if)# interface ethernet0/2
CCNAS-ASA(config-if)# switchport access vlan 3
CCNAS-ASA(config-if)# no shutdown
CCNAS-ASA(config-if)# interface vlan1
CCNAS-ASA(config-if)# nameif inside
INFO: Security level for "inside" set to 100 by default.
CCNAS-ASA(config-if)# security-level 100
CCNAS-ASA(config-if)# ip address 192.168.1.1 255.255.255.0
CCNAS-ASA(config-if)# interface vlan2
CCNAS-ASA(config-if)# nameif outside
INFO: Security level for "outside" set to 0 by default.
CCNAS-ASA(config-if)# security-level 0
CCNAS-ASA(config-if)# ip address 209.165.200.226 255.255.255.248
CCNAS-ASA(config-if)# interface vlan3
CCNAS-ASA(config-if)# no forward interface vlan1
CCNAS-ASA(config-if)# nameif dmz
INFO: Security level for "dmz" set to 0 by default.
CCNAS-ASA(config-if)# security-level 70
CCNAS-ASA(config-if)# ip address 192.168.2.1 255.255.255.0
CCNAS-ASA(config-if)# object network inside-net
CCNAS-ASA(config-network-object)# subnet 192.168.1.0 255.255.255.0
CCNAS-ASA(config-network-object)# object network dmz-server
CCNAS-ASA(config-network-object)# host 192.168.2.3
CCNAS-ASA(config-network-object)# access-list OUTSIDE-DMZ extended permit ip any host 192.168.2.3
CCNAS-ASA(config)# object network inside-net
CCNAS-ASA(config-network-object)# nat (inside,outside) dynamic interface
CCNAS-ASA(config-network-object)# object network dmz-server
CCNAS-ASA(config-network-object)# nat (dmz,outside) static 209.165.200.227
CCNAS-ASA(config-network-object)# access-group OUTSIDE-DMZ in interface outside
CCNAS-ASA(config)# route outside 0.0.0.0 0.0.0.0 209.165.200.225
CCNAS-ASA(config)# username admin password cisco123
CCNAS-ASA(config)# aaa authentication telnet console LOCAL
CCNAS-ASA(config)# aaa authentication ssh console LOCAL
CCNAS-ASA(config)# aaa authentication http console LOCAL
CCNAS-ASA(config)# http server enable
CCNAS-ASA(config)# http 192.168.1.0 255.255.255.0 inside
CCNAS-ASA(config)# ssh 192.168.1.0 255.255.255.0 inside
CCNAS-ASA(config)# telnet 192.168.1.0 255.255.255.0 inside
CCNAS-ASA(config)# telnet timeout 10
CCNAS-ASA(config)# ssh timeout 10
CCNAS-ASA(config)# policy-map global_policy
CCNAS-ASA(config-pmap)# class inspection_default
CCNAS-ASA(config-pmap-c)# inspect icmp
CCNAS-ASA(config-pmap-c)# crypto key generate rsa modulus 1024
WARNING: You have a RSA keypair already defined named <Default-RSA-Key>.
Do you really want to replace them? [yes/no]: y
Keypair generation process begin. Please wait...
To configure Clientless SSL VPN Remote Access in ASDM, we go to Wizards > VPN Wizards > Clientless SSL VPN Wizard.
We verify the SSL VPN login (via HTTPS) by opening 209.165.200.226 on a web browser on PC-C.
You'll be redirected to another URL when clicking on Web Mail. For this example, I've used the web server on a Catalyst 3560 switch.
To monitor VPN session in ASDM, we go to Monitoring > VPN > VPN Statistics > Sessions. In CLI, we issue the command show vpn-sessiondb webvpn.
CCNAS-ASA# show vpn-sessiondb webvpn
Session Type: WebVPN
Username : VPN-User Index : 3
Public IP : 172.16.3.3
Protocol : Clientless
License : AnyConnect Premium
Encryption : Clientless: (1)RC4 Hashing : Clientless: (1)SHA1
Bytes Tx : 236858 Bytes Rx : 15757
Group Policy : ClientlessVPN-Grp-Pol Tunnel Group : DefaultWEBVPNGroup
Login Time : 04:55:06 UTC Sun Jul 5 2015
Duration : 0h:01m:14s
Inactivity : 0h:00m:00s
NAC Result : Unknown
VLAN Mapping : N/A VLAN : none
CCNAS-ASA# write erase
Erase configuration in flash memory? [confirm]
[OK]
CCNAS-ASA# reload
System config has been modified. Save? [Y]es/[N]o:
Proceed with reload? [confirm]
CCNAS-ASA#
***
*** --- START GRACEFUL SHUTDOWN ---
Shutting down isakmp
Shutting down webvpn
Shutting down License Controller
Shutting down File system
***
*** --- SHUTDOWN NOW ---
Process shutdown finished
<OUTPUT TRUNCATED>
ciscoasa> enable
Password:
ciscoasa# conf t
ciscoasa(config)#
***************************** NOTICE *****************************
Help to improve the ASA platform by enabling anonymous reporting,
which allows Cisco to securely receive minimal error and health
information from the device. To learn more about this feature,
please visit: http://www.cisco.com/go/smartcall
Would you like to enable anonymous error reporting to help improve
the product? [Y]es, [N]o, [A]sk later: n
In the future, if you would like to enable this feature,
issue the command "call-home reporting anonymous".
Please remember to save your configuration.
ciscoasa(config)# hostname CCNAS-ASA
CCNAS-ASA(config)# domain-name ccnasecurity.com
CCNAS-ASA(config)# enable password cisco
CCNAS-ASA(config)# passwd cisco
CCNAS-ASA(config)# interface ethernet0/0
CCNAS-ASA(config-if)# switchport access vlan 2
CCNAS-ASA(config-if)# no shutdown
CCNAS-ASA(config-if)# interface ethernet0/1
CCNAS-ASA(config-if)# switchport access vlan 1
CCNAS-ASA(config-if)# no shutdown
CCNAS-ASA(config-if)# interface ethernet0/2
CCNAS-ASA(config-if)# switchport access vlan 3
CCNAS-ASA(config-if)# no shutdown
CCNAS-ASA(config-if)# interface vlan 1
CCNAS-ASA(config-if)# nameif inside
INFO: Security level for "inside" set to 100 by default.
CCNAS-ASA(config-if)# security-level 100
CCNAS-ASA(config-if)# ip address 192.168.1.1 255.255.255.0
CCNAS-ASA(config-if)# interface vlan 2
CCNAS-ASA(config-if)# nameif outside
INFO: Security level for "outside" set to 0 by default.
CCNAS-ASA(config-if)# security-level 0
CCNAS-ASA(config-if)# ip address 209.165.200.226 255.255.255.248
CCNAS-ASA(config-if)# interface vlan 3
CCNAS-ASA(config-if)# no forward interface vlan 1
CCNAS-ASA(config-if)# nameif dmz
INFO: Security level for "dmz" set to 0 by default.
CCNAS-ASA(config-if)# security-level 70
CCNAS-ASA(config-if)# ip address 192.168.2.1 255.255.255.0
CCNAS-ASA(config-if)# object network inside-net
CCNAS-ASA(config-network-object)# subnet 192.168.1.0 255.255.255.0
CCNAS-ASA(config-network-object)# nat (inside,outside) dynamic interface
CCNAS-ASA(config-network-object)# exit
CCNAS-ASA(config)# object network dmz-server
CCNAS-ASA(config-network-object)# host 192.168.2.3
CCNAS-ASA(config-network-object)# nat (dmz,outside) static 209.165.200.227
CCNAS-ASA(config-network-object)# exit
CCNAS-ASA(config)# access-list OUTSIDE-DMZ extended permit ip any host 192.168.2.3
CCNAS-ASA(config)# access-group OUTSIDE-DMZ in interface outside
CCNAS-ASA(config)# route outside 0 0 209.165.200.225
CCNAS-ASA(config)# username admin password cisco123 privilege 15
CCNAS-ASA(config)# aaa authentication telnet console LOCAL
CCNAS-ASA(config)# aaa authentication ssh console LOCAL
CCNAS-ASA(config)# aaa authentication http console LOCAL
CCNAS-ASA(config)# http server enable
CCNAS-ASA(config)# http 192.168.1.0 255.255.255.0 inside
CCNAS-ASA(config)# ssh 192.168.1.0 255.255.255.0 inside
CCNAS-ASA(config)# telnet 192.168.1.0 255.255.255.0 inside
CCNAS-ASA(config)# telnet timeout 10
CCNAS-ASA(config)# ssh timeout 10
CCNAS-ASA(config)# policy-map global_policy
CCNAS-ASA(config-pmap)# class inspection_default
CCNAS-ASA(config-pmap-c)# inspect icmp
CCNAS-ASA(config-pmap-c)# exit
CCNAS-ASA(config-pmap)# crypto key generate rsa modulus 1024
WARNING: You have a RSA keypair already defined named <Default-RSA-Key>.
Do you really want to replace them? [yes/no]: y
Keypair generation process begin. Please wait...
CCNAS-ASA(config)#
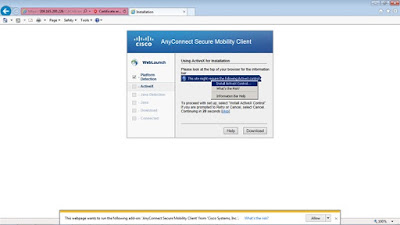
To configure AnyConnect SSL VPN Remote Access using ASDM, we to go Wizards > VPN Wizards > AnyConnect VPN.
We login to https://209.165.200.226 from PC-C and it will automatically go through the process of downloading the AnyConnect VPN client.
CCNAS-ASA# show vpn-sessiondb anyconnect
Session Type: AnyConnect
Username : VPN-User Index : 2
Assigned IP : 192.168.1.33 Public IP : 172.16.3.3
Protocol : Clientless SSL-Tunnel DTLS-Tunnel
License : AnyConnect Premium
Encryption : Clientless: (1)RC4 SSL-Tunnel: (1)RC4 DTLS-Tunnel: (1)AES128
Hashing : Clientless: (1)SHA1 SSL-Tunnel: (1)SHA1 DTLS-Tunnel: (1)SHA1
Bytes Tx : 118089 Bytes Rx : 112949
Group Policy : GroupPolicy_AnyC-SSL-VPN-Con-Prof
Tunnel Group : AnyC-SSL-VPN-Con-Prof
Login Time : 10:35:42 UTC Sun Jul 5 2015
Duration : 0h:06m:42s
Inactivity : 0h:00m:00s
NAC Result : Unknown
VLAN Mapping : N/A VLAN : none
R1(config)#ip route 0.0.0.0 0.0.0.0 serial0/0/0
R1(config)#interface fastethernet0/0
R1(config-if)#ip address 209.165.200.225 255.255.255.248
R1(config-if)#no shutdown
R1(config-if)#
*Jul 5 03:17:49.787: %LINK-3-UPDOWN: Interface FastEthernet0/0, changed state to up
*Jul 5 03:17:50.787: %LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet0/0, changed state to up
R1(config-if)#interface serial0/0/0
R1(config-if)#ip address 10.1.1.1 255.255.255.252
R1(config-if)#no shutdown
R1(config-if)#
*Jul 5 03:18:07.115: %LINK-3-UPDOWN: Interface Serial0/0/0, changed state to down
R1(config-if)#clock rate 64000
Router(config)#hostname R2
R2(config)#interface serial0/0/0
R2(config-if)#ip address 10.1.1.2 255.255.255.252
R2(config-if)#no shutdown
R2(config-if)#
*Jul 5 03:17:55.143: %LINK-3-UPDOWN: Interface Serial0/0/0, changed state to up
*Jul 5 03:17:56.143: %LINEPROTO-5-UPDOWN: Line protocol on Interface Serial0/0/0, changed state to up
R2(config-if)#do ping 10.1.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.1.1.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 28/28/32 ms
R2(config-if)#interface serial0/0/1
R2(config-if)#ip address 10.2.2.2 255.255.255.252
R2(config-if)#no shutdown
R2(config-if)#
*Jul 5 03:18:17.699: %LINK-3-UPDOWN: Interface Serial0/0/1, changed state to down
R2(config-if)#clock rate 64000
R2(config-if)#exit
R2(config)#ip route 209.165.200.224 255.255.255.248 serial0/0/0
R2(config)#ip route 172.16.3.0 255.255.255.0 serial0/0/1
Router(config)#hostname R3
R3(config)#interface fastethernet0/1
R3(config-if)#ip address 172.16.3.1 255.255.255.0
R3(config-if)#no shutdown
R3(config-if)#
*Jul 5 03:22:00.983: %LINK-3-UPDOWN: Interface FastEthernet0/1, changed state to up
*Jul 5 03:22:01.983: %LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet0/1, changed state to up
R3(config-if)#interface serial0/0/1
R3(config-if)#ip address 10.2.2.1 255.255.255.252
R3(config-if)#no shutdown
R3(config-if)#
*Jul 5 03:22:24.015: %LINK-3-UPDOWN: Interface Serial0/0/1, changed state to up
*Jul 5 03:22:25.015: %LINEPROTO-5-UPDOWN: Line protocol on Interface Serial0/0/1, changed state to up
R3(config-if)#do ping 10.2.2.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.2.2.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 28/28/28 ms
R3(config-if)#exit
R3(config)#ip route 0.0.0.0 0.0.0.0 serial0/0/1
R1(config)#ip http server
R1(config)#enable password cisco
R1(config)#line vty 0 4
R1(config-line)#password cisco
R1(config-line)#login
R1(config)#line console 0
R1(config-line)#password cisco
R1(config-line)#login
Switch(config)#hostname S1
Switch(config)#hostname S2
Switch(config)#hostname S3
ciscoasa> enable
Password: <ENTER>
ciscoasa# conf t
ciscoasa(config)#
***************************** NOTICE *****************************
Help to improve the ASA platform by enabling anonymous reporting,
which allows Cisco to securely receive minimal error and health
information from the device. To learn more about this feature,
please visit: http://www.cisco.com/go/smartcall
Would you like to enable anonymous error reporting to help improve
the product? [Y]es, [N]o, [A]sk later: n
In the future, if you would like to enable this feature,
issue the command "call-home reporting anonymous".
Please remember to save your configuration.
ciscoasa(config)# hostname CCNAS-ASA
CCNAS-ASA(config)# domain-name ccnasecurity.com
CCNAS-ASA(config)# enable password cisco
CCNAS-ASA(config)# passwd cisco
CCNAS-ASA(config)# interface ethernet0/0
CCNAS-ASA(config-if)# switchport access vlan 2
CCNAS-ASA(config-if)# no shutdown
CCNAS-ASA(config-if)# interface ethernet0/1
CCNAS-ASA(config-if)# switchport access vlan 1
CCNAS-ASA(config-if)# no shutdown
CCNAS-ASA(config-if)# interface ethernet0/2
CCNAS-ASA(config-if)# switchport access vlan 3
CCNAS-ASA(config-if)# no shutdown
CCNAS-ASA(config-if)# interface vlan1
CCNAS-ASA(config-if)# nameif inside
INFO: Security level for "inside" set to 100 by default.
CCNAS-ASA(config-if)# security-level 100
CCNAS-ASA(config-if)# ip address 192.168.1.1 255.255.255.0
CCNAS-ASA(config-if)# interface vlan2
CCNAS-ASA(config-if)# nameif outside
INFO: Security level for "outside" set to 0 by default.
CCNAS-ASA(config-if)# security-level 0
CCNAS-ASA(config-if)# ip address 209.165.200.226 255.255.255.248
CCNAS-ASA(config-if)# interface vlan3
CCNAS-ASA(config-if)# no forward interface vlan1
CCNAS-ASA(config-if)# nameif dmz
INFO: Security level for "dmz" set to 0 by default.
CCNAS-ASA(config-if)# security-level 70
CCNAS-ASA(config-if)# ip address 192.168.2.1 255.255.255.0
CCNAS-ASA(config-if)# object network inside-net
CCNAS-ASA(config-network-object)# subnet 192.168.1.0 255.255.255.0
CCNAS-ASA(config-network-object)# object network dmz-server
CCNAS-ASA(config-network-object)# host 192.168.2.3
CCNAS-ASA(config-network-object)# access-list OUTSIDE-DMZ extended permit ip any host 192.168.2.3
CCNAS-ASA(config)# object network inside-net
CCNAS-ASA(config-network-object)# nat (inside,outside) dynamic interface
CCNAS-ASA(config-network-object)# object network dmz-server
CCNAS-ASA(config-network-object)# nat (dmz,outside) static 209.165.200.227
CCNAS-ASA(config-network-object)# access-group OUTSIDE-DMZ in interface outside
CCNAS-ASA(config)# route outside 0.0.0.0 0.0.0.0 209.165.200.225
CCNAS-ASA(config)# username admin password cisco123
CCNAS-ASA(config)# aaa authentication telnet console LOCAL
CCNAS-ASA(config)# aaa authentication ssh console LOCAL
CCNAS-ASA(config)# aaa authentication http console LOCAL
CCNAS-ASA(config)# http server enable
CCNAS-ASA(config)# http 192.168.1.0 255.255.255.0 inside
CCNAS-ASA(config)# ssh 192.168.1.0 255.255.255.0 inside
CCNAS-ASA(config)# telnet 192.168.1.0 255.255.255.0 inside
CCNAS-ASA(config)# telnet timeout 10
CCNAS-ASA(config)# ssh timeout 10
CCNAS-ASA(config)# policy-map global_policy
CCNAS-ASA(config-pmap)# class inspection_default
CCNAS-ASA(config-pmap-c)# inspect icmp
CCNAS-ASA(config-pmap-c)# crypto key generate rsa modulus 1024
WARNING: You have a RSA keypair already defined named <Default-RSA-Key>.
Do you really want to replace them? [yes/no]: y
Keypair generation process begin. Please wait...
To configure Clientless SSL VPN Remote Access in ASDM, we go to Wizards > VPN Wizards > Clientless SSL VPN Wizard.
We verify the SSL VPN login (via HTTPS) by opening 209.165.200.226 on a web browser on PC-C.
You'll be redirected to another URL when clicking on Web Mail. For this example, I've used the web server on a Catalyst 3560 switch.
To monitor VPN session in ASDM, we go to Monitoring > VPN > VPN Statistics > Sessions. In CLI, we issue the command show vpn-sessiondb webvpn.
CCNAS-ASA# show vpn-sessiondb webvpn
Session Type: WebVPN
Username : VPN-User Index : 3
Public IP : 172.16.3.3
Protocol : Clientless
License : AnyConnect Premium
Encryption : Clientless: (1)RC4 Hashing : Clientless: (1)SHA1
Bytes Tx : 236858 Bytes Rx : 15757
Group Policy : ClientlessVPN-Grp-Pol Tunnel Group : DefaultWEBVPNGroup
Login Time : 04:55:06 UTC Sun Jul 5 2015
Duration : 0h:01m:14s
Inactivity : 0h:00m:00s
NAC Result : Unknown
VLAN Mapping : N/A VLAN : none
CCNAS-ASA# write erase
Erase configuration in flash memory? [confirm]
[OK]
CCNAS-ASA# reload
System config has been modified. Save? [Y]es/[N]o:
Proceed with reload? [confirm]
CCNAS-ASA#
***
*** --- START GRACEFUL SHUTDOWN ---
Shutting down isakmp
Shutting down webvpn
Shutting down License Controller
Shutting down File system
***
*** --- SHUTDOWN NOW ---
Process shutdown finished
<OUTPUT TRUNCATED>
ciscoasa> enable
Password:
ciscoasa# conf t
ciscoasa(config)#
***************************** NOTICE *****************************
Help to improve the ASA platform by enabling anonymous reporting,
which allows Cisco to securely receive minimal error and health
information from the device. To learn more about this feature,
please visit: http://www.cisco.com/go/smartcall
Would you like to enable anonymous error reporting to help improve
the product? [Y]es, [N]o, [A]sk later: n
In the future, if you would like to enable this feature,
issue the command "call-home reporting anonymous".
Please remember to save your configuration.
ciscoasa(config)# hostname CCNAS-ASA
CCNAS-ASA(config)# domain-name ccnasecurity.com
CCNAS-ASA(config)# enable password cisco
CCNAS-ASA(config)# passwd cisco
CCNAS-ASA(config)# interface ethernet0/0
CCNAS-ASA(config-if)# switchport access vlan 2
CCNAS-ASA(config-if)# no shutdown
CCNAS-ASA(config-if)# interface ethernet0/1
CCNAS-ASA(config-if)# switchport access vlan 1
CCNAS-ASA(config-if)# no shutdown
CCNAS-ASA(config-if)# interface ethernet0/2
CCNAS-ASA(config-if)# switchport access vlan 3
CCNAS-ASA(config-if)# no shutdown
CCNAS-ASA(config-if)# interface vlan 1
CCNAS-ASA(config-if)# nameif inside
INFO: Security level for "inside" set to 100 by default.
CCNAS-ASA(config-if)# security-level 100
CCNAS-ASA(config-if)# ip address 192.168.1.1 255.255.255.0
CCNAS-ASA(config-if)# interface vlan 2
CCNAS-ASA(config-if)# nameif outside
INFO: Security level for "outside" set to 0 by default.
CCNAS-ASA(config-if)# security-level 0
CCNAS-ASA(config-if)# ip address 209.165.200.226 255.255.255.248
CCNAS-ASA(config-if)# interface vlan 3
CCNAS-ASA(config-if)# no forward interface vlan 1
CCNAS-ASA(config-if)# nameif dmz
INFO: Security level for "dmz" set to 0 by default.
CCNAS-ASA(config-if)# security-level 70
CCNAS-ASA(config-if)# ip address 192.168.2.1 255.255.255.0
CCNAS-ASA(config-if)# object network inside-net
CCNAS-ASA(config-network-object)# subnet 192.168.1.0 255.255.255.0
CCNAS-ASA(config-network-object)# nat (inside,outside) dynamic interface
CCNAS-ASA(config-network-object)# exit
CCNAS-ASA(config)# object network dmz-server
CCNAS-ASA(config-network-object)# host 192.168.2.3
CCNAS-ASA(config-network-object)# nat (dmz,outside) static 209.165.200.227
CCNAS-ASA(config-network-object)# exit
CCNAS-ASA(config)# access-list OUTSIDE-DMZ extended permit ip any host 192.168.2.3
CCNAS-ASA(config)# access-group OUTSIDE-DMZ in interface outside
CCNAS-ASA(config)# route outside 0 0 209.165.200.225
CCNAS-ASA(config)# username admin password cisco123 privilege 15
CCNAS-ASA(config)# aaa authentication telnet console LOCAL
CCNAS-ASA(config)# aaa authentication ssh console LOCAL
CCNAS-ASA(config)# aaa authentication http console LOCAL
CCNAS-ASA(config)# http server enable
CCNAS-ASA(config)# http 192.168.1.0 255.255.255.0 inside
CCNAS-ASA(config)# ssh 192.168.1.0 255.255.255.0 inside
CCNAS-ASA(config)# telnet 192.168.1.0 255.255.255.0 inside
CCNAS-ASA(config)# telnet timeout 10
CCNAS-ASA(config)# ssh timeout 10
CCNAS-ASA(config)# policy-map global_policy
CCNAS-ASA(config-pmap)# class inspection_default
CCNAS-ASA(config-pmap-c)# inspect icmp
CCNAS-ASA(config-pmap-c)# exit
CCNAS-ASA(config-pmap)# crypto key generate rsa modulus 1024
WARNING: You have a RSA keypair already defined named <Default-RSA-Key>.
Do you really want to replace them? [yes/no]: y
Keypair generation process begin. Please wait...
CCNAS-ASA(config)#
To configure AnyConnect SSL VPN Remote Access using ASDM, we to go Wizards > VPN Wizards > AnyConnect VPN.
We login to https://209.165.200.226 from PC-C and it will automatically go through the process of downloading the AnyConnect VPN client.
CCNAS-ASA# show vpn-sessiondb anyconnect
Session Type: AnyConnect
Username : VPN-User Index : 2
Assigned IP : 192.168.1.33 Public IP : 172.16.3.3
Protocol : Clientless SSL-Tunnel DTLS-Tunnel
License : AnyConnect Premium
Encryption : Clientless: (1)RC4 SSL-Tunnel: (1)RC4 DTLS-Tunnel: (1)AES128
Hashing : Clientless: (1)SHA1 SSL-Tunnel: (1)SHA1 DTLS-Tunnel: (1)SHA1
Bytes Tx : 118089 Bytes Rx : 112949
Group Policy : GroupPolicy_AnyC-SSL-VPN-Con-Prof
Tunnel Group : AnyC-SSL-VPN-Con-Prof
Login Time : 10:35:42 UTC Sun Jul 5 2015
Duration : 0h:06m:42s
Inactivity : 0h:00m:00s
NAC Result : Unknown
VLAN Mapping : N/A VLAN : none








































No comments:
Post a Comment