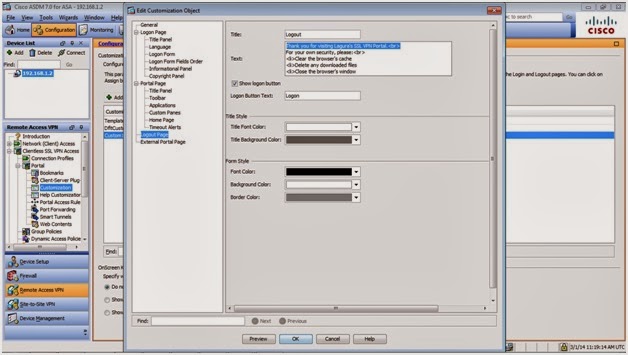
An important part of deploying an SSL VPN solution is customization. After all, businesses often have a logo or color scheme used throughout the company on various pieces of documentation, assets, or even their buildings. It is not only pleasing to the eye but important for the company's image to be able to extend this scheme to your VPN portal. It can also help remote users to identify who they are connected to and the portal resources they require.
You can modify the look and feel of the following pages for your users:
* Logon page
* Portal page
* Logout page
The customization option you choose will depend on the level of granularity and customization you require. Customization through the ASDM is based on predefined areas and sections of the profile pages that you easily modify by changing the color and text and uploading logos. If you choose to fully customize the portal without the use of the ASDM, you can upload your own XML files and code; however, you are restricted to use only those items supported by the ASA.
I took out my ASA 5505 just to be able to create customized clientless SSL VPN portal. For some reason, it doesn't let me emulate it in GNS3.
Licensed features for this platform:
Maximum Physical Interfaces : 8 perpetual
VLANs : 3 DMZ Restricted
Dual ISPs : Disabled perpetual
VLAN Trunk Ports : 0 perpetual
Inside Hosts : 10 perpetual
Failover : Disabled perpetual
Encryption-DES : Enabled perpetual
Encryption-3DES-AES : Enabled perpetual
AnyConnect Premium Peers : 2 perpetual // CLIENTLESS SSL VPN
AnyConnect Essentials : Disabled perpetual
Other VPN Peers : 10 perpetual // REMOTE ACCESS AND SITE-TO-SITE VPN
Total VPN Peers : 12 perpetual
Shared License : Disabled perpetual
AnyConnect for Mobile : Disabled perpetual
AnyConnect for Cisco VPN Phone : Disabled perpetual
Advanced Endpoint Assessment : Disabled perpetual
UC Phone Proxy Sessions : 2 perpetual
Total UC Proxy Sessions : 2 perpetual
Botnet Traffic Filter : Disabled perpetual
Intercompany Media Engine : Disabled perpetual
Cluster : Disabled perpetual
This platform has a Base license.
The Preview button (beside OK) is available on every customization page option and it opens on a Microsoft Word file. It will also prompt for a username and password prior to viewing. You can always preview any changes made before applying them to the ASA.
The onscreen keyboard is a Java-based keyboard that you can use to prevent potential keylogger software access to any credentials the user might be required to enter. This is a useful feature if your remote users are known to operate from publicly available computers or devices that you have no control over.
You can modify the look and feel of the following pages for your users:
* Logon page
* Portal page
* Logout page
The customization option you choose will depend on the level of granularity and customization you require. Customization through the ASDM is based on predefined areas and sections of the profile pages that you easily modify by changing the color and text and uploading logos. If you choose to fully customize the portal without the use of the ASDM, you can upload your own XML files and code; however, you are restricted to use only those items supported by the ASA.
I took out my ASA 5505 just to be able to create customized clientless SSL VPN portal. For some reason, it doesn't let me emulate it in GNS3.
Licensed features for this platform:
Maximum Physical Interfaces : 8 perpetual
VLANs : 3 DMZ Restricted
Dual ISPs : Disabled perpetual
VLAN Trunk Ports : 0 perpetual
Inside Hosts : 10 perpetual
Failover : Disabled perpetual
Encryption-DES : Enabled perpetual
Encryption-3DES-AES : Enabled perpetual
AnyConnect Premium Peers : 2 perpetual // CLIENTLESS SSL VPN
AnyConnect Essentials : Disabled perpetual
Other VPN Peers : 10 perpetual // REMOTE ACCESS AND SITE-TO-SITE VPN
Total VPN Peers : 12 perpetual
Shared License : Disabled perpetual
AnyConnect for Mobile : Disabled perpetual
AnyConnect for Cisco VPN Phone : Disabled perpetual
Advanced Endpoint Assessment : Disabled perpetual
UC Phone Proxy Sessions : 2 perpetual
Total UC Proxy Sessions : 2 perpetual
Botnet Traffic Filter : Disabled perpetual
Intercompany Media Engine : Disabled perpetual
Cluster : Disabled perpetual
This platform has a Base license.
The Preview button (beside OK) is available on every customization page option and it opens on a Microsoft Word file. It will also prompt for a username and password prior to viewing. You can always preview any changes made before applying them to the ASA.
The onscreen keyboard is a Java-based keyboard that you can use to prevent potential keylogger software access to any credentials the user might be required to enter. This is a useful feature if your remote users are known to operate from publicly available computers or devices that you have no control over.