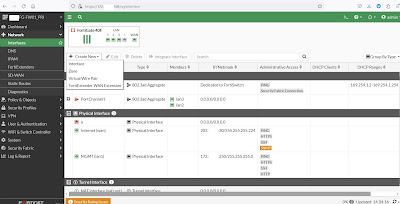
Here's a link to configure a link aggregation (LACP) interface in a FortiGate firewall. To configure, go to Global VDOM (if using Multi VDOM) > Network > Interfaces > Create New > Interface.
Type a Name > select Type: 802.3ad Aggregate.
Under Interface members > click add (+ icon) > select interfaces: lan2 and lan3.
To create an 802.1Q Layer 3 sub-interface via the aggregated link, go to Network > Interfaces > Create New > Interface.
Type a Name > select Type: VLAN > select VLAN protocol: 802.1Q (default) > select the created aggregated interface: PortChannel1 > type VLAN ID: 300 > select Role: LAN (optional).
Under Addressing mode > select: Manual > Type IP/Netmask: 172.27.100.1/255.255.255.248 (can also type: /29) > under Administrative Access > select: HTTP (for lab VM), HTTPS, SSH and PING > click OK.
I've configured an EtherChannel interface in the adjacent Cisco switch using ports FE0/1 and FE0/2 and also connected a PC using the inside VLAN 300.
SW01#configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
SW01(config)#vlan 300
SW01(config-vlan)# name LAB-INSIDE
SW01(config-vlan)#exit
SW01(config)#interface range Fa0/1-2
SW01(config-if-range)# description
### PortChannel1 ###
SW01(config-if-range)# switchport trunk encapsulation dot1q
SW01(config-if-range)# switchport mode trunk
SW01(config-if-range)# channel-group 1 mode active
Creating a port-channel interface Port-channel 1
SW01(config-if-range)# no shutdown
SW01(config-if-range)#
*Mar 17 01:08:11.597: %LINEPROTO-5-UPDOWN: Line protocol on Interface Vlan1, changed state to down
*Mar 17 01:08:12.570: %LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet0/1, changed state to down
*Mar 17 01:08:12.587: %LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet0/2, changed state to down
*Mar 17 01:08:19.373: %LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet0/2, changed state to up
*Mar 17 01:08:19.399: %LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet0/1, changed state to up
*Mar 17 01:08:20.355: %LINK-3-UPDOWN: Interface Port-channel1, changed state to up
*Mar 17 01:08:21.362: %LINEPROTO-5-UPDOWN: Line protocol on Interface Port-channel1, changed state to up
SW01(config-if-range)#
SW01(config-if-range)#interface port-channel1
SW01(config-if)# switchport trunk encapsulation dot1q
SW01(config-if)# switchport mode trunk
SW01(config-if)#
SW01(config-if)#interface Fa0/12
SW01(config-if)# description ### TEST PC: 172.27.100.2 ###
SW01(config-if)# switchport mode access
SW01(config-if)# switchport access vlan 300
SW01(config-if)#end
W01#write memory
Building configuration...
[OK]
SW01#show interface description
Interface Status Protocol Description
Vl1 up down
Fa0/1 up up ### PortChannel1 ###
Fa0/2 up up ### PortChannel1 ###
Fa0/3 down down
Fa0/4 down down
Fa0/5 down down
Fa0/6 down down
Fa0/7 down down
Fa0/8 down down
Fa0/9 down down
Fa0/10 down down
Fa0/11 down down
Fa0/12 up up ### TEST PC: 172.27.100.2 ###
Fa0/13 down down
Fa0/14 down down
Fa0/15 down down
Fa0/16 down down
Fa0/17 down down
Fa0/18 down down
Fa0/19 down down
Fa0/20 down down
Fa0/21 down down
Fa0/22 down down
Fa0/23 down down
Fa0/24 down down
Gi0/1 down down
Gi0/2 down down
Po1 up up
SW01#show
etherchannel summary // NOTICE THE LACP PROTOCOL WAS USED
Flags: D - down P - bundled in port-channel
I - stand-alone s - suspended
H - Hot-standby (LACP only)
R - Layer3 S - Layer2
U - in use f - failed to allocate aggregator
M - not in use, minimum links not met
u - unsuitable for bundling
w - waiting to be aggregated
d - default port
Number of channel-groups in use: 1
Number of aggregators: 1
Group Port-channel Protocol Ports
------+-------------+-----------+-----------------------------------------------
1 Po1(SU) LACP Fa0/1(P) Fa0/2(P)
I've assigned the PC with an IP address 172.27.100.2/29 and can ping the FortiGate remote/gateway IP address.
C:\Users\john>ipconfig
Windows IP Configuration
Ethernet adapter Ethernet:
Connection-specific DNS Suffix . :
Link-local IPv6 Address . . . . . : fe80::b6e2:2fc0:a2d7:10ab%cd
IPv4 Address. . . . . . . . . . . : 172.27.100.2
Subnet Mask . . . . . . . . . . . : 255.255.255.248
Default Gateway . . . . . . . . . : 172.27.100.1
C:\Users\john>ping 172.27.100.1
Pinging 172.27.100.1 with 32 bytes of data:
Reply from 172.27.100.1: bytes=32 time=1ms TTL=255
Reply from 172.27.100.1: bytes=32 time=1ms TTL=255
Reply from 172.27.100.1: bytes=32 time=1ms TTL=255
Reply from 172.27.100.1: bytes=32 time=1ms TTL=255
Ping statistics for 172.27.100.1:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 1ms, Maximum = 1ms, Average = 1ms
I can ping the FortiGate Layer 3 sub-interface (VLAN 300) and lan2 and lan3 ports showed as green/up.
I tried to simulate an interface failure by disconnecting the RJ45 cable in lan2 port.
There was a single ping packet loss/drop that was observed.
C:\Users\john>ping 172.27.100.1 -t
Pinging 172.27.100.1 with 32 bytes of data:
Reply from 172.27.100.1: bytes=32 time=1ms TTL=255
Reply from 172.27.100.1: bytes=32 time=9ms TTL=255
Reply from 172.27.100.1: bytes=32 time=1ms TTL=255
Reply from 172.27.100.1: bytes=32 time=15ms TTL=255
Request timed out.
Reply from 172.27.100.1: bytes=32 time=1ms TTL=255
Reply from 172.27.100.1: bytes=32 time=1ms TTL=255
Reply from 172.27.100.1: bytes=32 time=1ms TTL=255
Reply from 172.27.100.1: bytes=32 time=1ms TTL=255
Reply from 172.27.100.1: bytes=32 time=1ms TTL=255
Reply from 172.27.100.1: bytes=32 time=1ms TTL=255
Ping statistics for 172.27.100.1:
Packets: Sent = 11, Received = 10, Lost = 1 (9% loss),
Approximate round trip times in milli-seconds:
Minimum = 1ms, Maximum = 15ms, Average = 3ms
Control-C
^C