IKEv1 provides a framework for the parameter negotiation and key exchange between VPN peers for the correct establishment of a (Security Association) SA.
However, the actual processes of key exchange and parameter negotiation are carried out by two protocols used by IKEv1:
* Internet Security Association and Key Management Protocol (ISAKMP)
* Oakley
ISAKMP takes care of parameter negotiation between peers (for example, DH groups, lifetimes, encryption and authentication). The process of negotiating these parameters between peers is required for the successful establishment of SAs. After an SA has been established, ISAKMP defines the procedures followed for correct maintenance and removal of the SA during connection termination.
Note: You will often find the terms ISAKMP and IKE used interchangeably in earlier versions of ASA (pre 8.4) and IOS reference IKEv1 functions and parameters.
Two mandatory IKEv1 phases (aptly named IKEv1 Phase 1 and IKEv1 Phase 2) must be followed by each peer before a communications tunnel can be established between them and they are ready for successful data transmision:
* IKEv1 Phase 1: During this phase, both peers negotiate parameters (integrity and encryption algorithms, authentication methods) to set up a secure and authenticated tunnel. This is also called a management channel because no user data is flowing through it (and it is actually a bidirectional IKE SA). Its sole scope is to handle secure Phase 2 negotiations. It is called bidirectional because both peers use only one session key to secure both incoming and outgoing traffic. Peer authentication can be carried out by one of the following methods:
- Pre-shared keys
- Digital certificates
* IKEv1 Phase 2: This second mandatory phase uses the negotiated parameters in Phase 1 for secure IPsec SA creation. However, unlike the single bidirectional SA created within Phase 1, the IPsec SA are unidirectional, meaning a different session key is used for each direction (one for inbound, or decrypted, traffic, and one for outbound, or encrypted, traffic). This is applicable for any administrator-configured source-destination network pair. Therefore, you might end up with four unidirectional IPsec SAs if you have two source-destination network pairs defined in a VPN policy.
I used my 871w IOS router and ASA 5505 firewall to establish an IKEv1 IPsec site-to-site VPN tunnel. This will help demonstrate the similarities and differences in configuring and troubleshooting for IKE Phase 1 and IKE Phase 2 VPN policies.
871W(config)#crypto ?
ca Certification authority
call Configure Crypto Call Admission Control
ctcp Configure cTCP encapsulation
dynamic-map Specify a dynamic crypto map template
engine Enter a crypto engine configurable menu
gdoi Configure GDOI policy
identity Enter a crypto identity list
ipsec Configure IPSEC policy
isakmp Configure ISAKMP policy
key Long term key operations
keyring Key ring commands
logging logging messages
map Enter a crypto map
mib Configure Crypto-related MIB Parameters
pki Public Key components
provisioning Secure Device Provisioning
wui Crypto HTTP configuration interfaces
xauth X-Auth parameters
871W(config)#crypto isakmp ?
aggressive-mode Disable ISAKMP aggressive mode
client Set client configuration policy
enable Enable ISAKMP
fragmentation IKE Fragmentation enabled if required
identity Set the identity which ISAKMP will use
invalid-spi-recovery Initiate IKE and send Invalid SPI Notify
keepalive Set a keepalive interval for use with IOS peers
key Set pre-shared key for remote peer
nat Set a nat keepalive interval for use with IOS peers
peer Set Peer Policy
policy Set policy for an ISAKMP protection suite
profile Define ISAKMP Profiles
xauth Set Extended Authentication values
871W(config)#crypto isakmp policy ?
<1-10000> Priority of protection suite
871W(config)#crypto isakmp policy 1 // IKE PHASE 1 POLICY; LOWER NUMBER PREFERRED
871W(config-isakmp)#?
ISAKMP commands:
authentication Set authentication method for protection suite
default Set a command to its defaults
encryption Set encryption algorithm for protection suite
exit Exit from ISAKMP protection suite configuration mode
group Set the Diffie-Hellman group
hash Set hash algorithm for protection suite
lifetime Set lifetime for ISAKMP security association
no Negate a command or set its defaults
871W(config-isakmp)#authentication ?
pre-share Pre-Shared Key
rsa-encr Rivest-Shamir-Adleman Encryption
rsa-sig Rivest-Shamir-Adleman Signature
871W(config-isakmp)#authentication pre-share
871W(config-isakmp)#encryption ?
3des Three key triple DES
aes AES - Advanced Encryption Standard.
des DES - Data Encryption Standard (56 bit keys).
871W(config-isakmp)#encryption aes ?
128 128 bit keys.
192 192 bit keys.
256 256 bit keys.
<cr>
871W(config-isakmp)#encryption aes 256 // USE STRONGER ALGORITHMS ON LOWER POLICY
871W(config-isakmp)#hash ?
md5 Message Digest 5
sha Secure Hash Standard
871W(config-isakmp)#hash sha
871W(config-isakmp)#group ?
1 Diffie-Hellman group 1
2 Diffie-Hellman group 2
5 Diffie-Hellman group 5
871W(config-isakmp)#group 2 // DEFAULT DH GROUP
871W(config-isakmp)#lifetime ?
<60-86400> lifetime in seconds
871W(config-isakmp)#lifetime 43200 // LOWER LIFETIME WILL BE CHOSEN BETWEEN VPN PEERS
871W(config-isakmp)#exit
871W(config)#crypto isakmp ?
aggressive-mode Disable ISAKMP aggressive mode
client Set client configuration policy
enable Enable ISAKMP
fragmentation IKE Fragmentation enabled if required
identity Set the identity which ISAKMP will use
invalid-spi-recovery Initiate IKE and send Invalid SPI Notify
keepalive Set a keepalive interval for use with IOS peers
key Set pre-shared key for remote peer
nat Set a nat keepalive interval for use with IOS peers
peer Set Peer Policy
policy Set policy for an ISAKMP protection suite
profile Define ISAKMP Profiles
xauth Set Extended Authentication values
871W(config)#crypto isakmp key ?
0 Specifies an UNENCRYPTED password will follow
6 Specifies an ENCRYPTED password will follow
871W(config)#crypto isakmp key 6 ?
WORD The HIDDEN user password string
871W(config)#crypto isakmp key 6 cisco ?
address define shared key with IP address
hostname define shared key with hostname
871W(config)#crypto isakmp key 6 cisco address ?
A.B.C.D Peer IP address
ipv6 define shared key with IPv6 address
871W(config)#crypto isakmp key 6 cisco address 192.168.1.2
871W(config)#crypto ipsec ?
client Configure a client
df-bit Handling of encapsulated DF bit.
fragmentation Handling of fragmentation of near-MTU sized packets
nat-transparency IPsec NAT transparency model
optional Enable optional encryption for IPSec
profile Configure an ipsec policy profile
security-association Security association parameters
transform-set Define transform and settings
871W(config)#crypto ipsec transform-set ?
WORD Transform set tag
871W(config)#crypto ipsec transform-set 871_IKEv1_TSET ?
ah-md5-hmac AH-HMAC-MD5 transform
ah-sha-hmac AH-HMAC-SHA transform
comp-lzs IP Compression using the LZS compression algorithm
esp-3des ESP transform using 3DES(EDE) cipher (168 bits)
esp-aes ESP transform using AES cipher
esp-des ESP transform using DES cipher (56 bits)
esp-md5-hmac ESP transform using HMAC-MD5 auth
esp-null ESP transform w/o cipher
esp-seal ESP transform using SEAL cipher (160 bits)
esp-sha-hmac ESP transform using HMAC-SHA auth
871W(config)#crypto ipsec transform-set 871_IKEv1_TSET esp-aes ?
128 128 bit keys.
192 192 bit keys.
256 256 bit keys.
ah-md5-hmac AH-HMAC-MD5 transform
ah-sha-hmac AH-HMAC-SHA transform
comp-lzs IP Compression using the LZS compression algorithm
esp-md5-hmac ESP transform using HMAC-MD5 auth
esp-sha-hmac ESP transform using HMAC-SHA auth
<cr>
871W(config)#crypto ipsec transform-set 871_IKEv1_TSET esp-aes 256 ?
ah-md5-hmac AH-HMAC-MD5 transform
ah-sha-hmac AH-HMAC-SHA transform
comp-lzs IP Compression using the LZS compression algorithm
esp-md5-hmac ESP transform using HMAC-MD5 auth
esp-sha-hmac ESP transform using HMAC-SHA auth
<cr>
871W(config)#crypto ipsec transform-set 871_IKEv1_TSET esp-aes 256 esp-sha-hmac // IKE PHASE 2 POLICY
871W(cfg-crypto-trans)#exit
871W(config)#access-list ?
<1-99> IP standard access list
<100-199> IP extended access list
<1100-1199> Extended 48-bit MAC address access list
<1300-1999> IP standard access list (expanded range)
<200-299> Protocol type-code access list
<2000-2699> IP extended access list (expanded range)
<700-799> 48-bit MAC address access list
dynamic-extended Extend the dynamic ACL absolute timer
rate-limit Simple rate-limit specific access list
871W(config)#access-list 100 ?
deny Specify packets to reject
dynamic Specify a DYNAMIC list of PERMITs or DENYs
permit Specify packets to forward
remark Access list entry comment
871W(config)#access-list 100 permit ?
<0-255> An IP protocol number
ahp Authentication Header Protocol
eigrp Cisco's EIGRP routing protocol
esp Encapsulation Security Payload
gre Cisco's GRE tunneling
icmp Internet Control Message Protocol
igmp Internet Gateway Message Protocol
ip Any Internet Protocol
ipinip IP in IP tunneling
nos KA9Q NOS compatible IP over IP tunneling
ospf OSPF routing protocol
pcp Payload Compression Protocol
tcp Transmission Control Protocol
udp User Datagram Protocol
871W(config)#access-list 100 permit ip ?
A.B.C.D Source address
any Any source host
host A single source host
871W(config)#access-list 100 permit ip host 192.168.1.1 host 192.168.1.2 // CRYPTO ACL; REMOTE VPN ACL MUST BE REVERSED (MIRRORED)
871W(config)#crypto map ?
WORD Crypto map tag
871W(config)#crypto map 871_IKEv1_CMAP ?
<1-65535> Sequence to insert into crypto map entry
client Specify client configuration settings
isakmp Specify isakmp configuration settings
isakmp-profile Specify isakmp profile to use
local-address Interface to use for local address for this crypto map
redundancy High availability options for this map
871W(config)#crypto map 871_IKEv1_CMAP 1 ?
gdoi GDOI
ipsec-isakmp IPSEC w/ISAKMP
ipsec-manual IPSEC w/manual keying
<cr>
871W(config)#crypto map 871_IKEv1_CMAP 1 ipsec-isakmp
% NOTE: This new crypto map will remain disabled until a peer
and a valid access list have been configured.
871W(config-crypto-map)#?
Crypto Map configuration commands:
default Set a command to its defaults
description Description of the crypto map statement policy
dialer Dialer related commands
exit Exit from crypto map configuration mode
match Match values.
no Negate a command or set its defaults
reverse-route Reverse Route Injection.
set Set values for encryption/decryption
871W(config-crypto-map)#set ?
identity Identity restriction.
ip Interface Internet Protocol config commands
isakmp-profile Specify isakmp Profile
nat Set NAT translation
peer Allowed Encryption/Decryption peer.
pfs Specify pfs settings
reverse-route Reverse Route Injection.
security-association Security association parameters
transform-set Specify list of transform sets in priority order
871W(config-crypto-map)#set peer ?
A.B.C.D IP address of peer
WORD Host name of the peer
871W(config-crypto-map)#set peer 192.168.1.2
871W(config-crypto-map)#set transform-set ?
WORD Proposal tag
871W(config-crypto-map)#set transform-set 871_IKEv1_TSET
871W(config-crypto-map)#match ?
address Match address of packets to encrypt.
871W(config-crypto-map)#match address ?
<100-199> IP access-list number
<2000-2699> IP access-list number (expanded range)
WORD Access-list name
871W(config-crypto-map)#match address 100
871W(config-crypto-map)#exit
871W(config)#interface bvi1
871W(config-if)#ip address 192.168.1.1
871W(config-if)#crypto map 871_IKEv1_CMAP
----
ASA5505(config)# crypto ?
configure mode commands/options:
ca Certification authority
dynamic-map Configure a dynamic crypto map
ikev1 Configure IKEv1 policy
ikev2 Configure IKEv2 policy
ipsec Configure transform-set, IPSec SA lifetime, and fragmentation
isakmp Configure ISAKMP
key Long term key operations
map Configure a crypto map
exec mode commands/options:
ca Certification authority
ASA5505(config)# crypto ikev1 ?
configure mode commands/options:
am-disable Disable inbound aggressive mode connections
enable Enable IKEv1 on the specified interface
ipsec-over-tcp Enable and configure IPSec over TCP
policy Set IKEv1 policy suite
ASA5505(config)# crypto ikev1 enable ?
configure mode commands/options:
Type an interface name to enable
inside Name of interface Vlan1
outside Name of interface Vlan2
ASA5505(config)# crypto ikev1 enable outside
ASA5505(config)# crypto ikev1 policy ?
configure mode commands/options:
<1-65535> Policy suite priority(1 highest, 65535 lowest)
ASA5505(config)# crypto ikev1 policy 1 // IKE PHASE 1 POLICY
ASA5505(config-ikev1-policy)# ?
crypto ikev1 policy configuration commands:
authentication Set authentication method (pre-share or rsa-sig)
encryption Set encryption algorithm (des, 3des, aes-128, aes-192, or
aes-256)
exit Exit from crypto ikev1 policy configuration mode
group Set Diffie-Hellman group (1,2 or 5)
hash Set hash algorithm (md5 or sha1)
help Help for crypto ikev1 policy configuration commands
lifetime Set IKEV1 SA lifetime (seconds)
no Negate a command or set its defaults
<cr>
ASA5505(config-ikev1-policy)# authentication ?
ikev1-policy mode commands/options:
crack set auth crack
pre-share set auth pre-share
rsa-sig set auth rsa-sig
ASA5505(config-ikev1-policy)# authentication pre-share
ASA5505(config-ikev1-policy)# encryption ?
ikev1-policy mode commands/options:
3des 3des encryption
aes aes-128 encryption
aes-192 aes-192 encryption
aes-256 aes-256 encryption
des des encryption
ASA5505(config-ikev1-policy)# encryption aes-256
ASA5505(config-ikev1-policy)# hash ?
ikev1-policy mode commands/options:
md5 set hash md5
sha set hash sha1
ASA5505(config-ikev1-policy)# hash sha
ASA5505(config-ikev1-policy)# group ?
ikev1-policy mode commands/options:
1 Diffie-Hellman group 1
2 Diffie-Hellman group 2
5 Diffie-Hellman group 5
7 Diffie-Hellman group 7 (DEPRECATED)
ASA5505(config-ikev1-policy)# group 2
ASA5505(config-ikev1-policy)# lifetime 86400 // 43200 SECONDS WILL BE CHOSEN
ASA5505(config-ikev1-policy)# exit
ASA5505(config)# crypto ipsec ?
configure mode commands/options:
df-bit Set IPsec DF policy
fragmentation Set IPsec fragmentation policy
ikev1 Set IKEv1 settings
ikev2 Set IKEv2 settings
security-association Set security association parameters
ASA5505(config)# crypto ipsec ikev1 ?
configure mode commands/options:
transform-set Define transform and settings
ASA5505(config)# crypto ipsec ikev1 transform-set ?
configure mode commands/options:
WORD < 64 char Transform set tag
ASA5505(config)# crypto ipsec ikev1 transform-set 5505_IKEv1_TSET ?
configure mode commands/options:
esp-3des esp 3des encryption
esp-aes esp aes 128 encryption
esp-aes-192 esp aes 192 encryption
esp-aes-256 esp aes 256 encryption
esp-des esp des encryption
esp-md5-hmac esp md5 authentication
esp-none esp no authentication
esp-null esp null encryption
esp-sha-hmac esp sha authentication
mode mode transport
ASA5505(config)# crypto ipsec ikev1 transform-set 5505_IKEv1_TSET esp-aes-256 ?
configure mode commands/options:
esp-3des esp 3des encryption
esp-aes esp aes 128 encryption
esp-aes-192 esp aes 192 encryption
esp-aes-256 esp aes 256 encryption
esp-des esp des encryption
esp-md5-hmac esp md5 authentication
esp-none esp no authentication
esp-null esp null encryption
esp-sha-hmac esp sha authentication
<cr>
ASA5505(config)# crypto ipsec ikev1 transform-set 5505_IKEv1_TSET esp-aes-256 esp-sha-hmac // IKE PHASE 2 POLICY
ASA5505(config)# access-list ?
configure mode commands/options:
WORD < 241 char Access list identifier
alert-interval Specify the alert interval for generating syslog message
106001 which alerts that the system has reached a deny flow
maximum. If not specified, the default value is 300 sec
deny-flow-max Specify the maximum number of concurrent deny flows that can
be created. If not specified, the default value is 4096
ASA5505(config)# access-list 100 ?
configure mode commands/options:
deny Specify packets to reject
extended Configure access policy for IP traffic through the system
line Use this to specify line number at which ACE should be entered
permit Specify packets to forward
remark Specify a comment (remark) for the access-list after this keyword
rename rename an existing access-list
standard Use this to configure policy having destination host or network
only
webtype Use this to configure WebVPN related policy
ASA5505(config)# access-list 100 extended ?
configure mode commands/options:
deny Specify packets to reject
permit Specify packets to forward
ASA5505(config)# access-list 100 extended permit ?
configure mode commands/options:
<0-255> Enter protocol number (0 - 255)
ah
eigrp
esp
gre
icmp
icmp6
igmp
igrp
ip
ipinip
ipsec
nos
object Specify a service object after this keyword
object-group Specify a service or protocol object-group after this keyword
ospf
pcp
pim
pptp
snp
tcp
udp
ASA5505(config)# access-list 100 extended permit ip ?
configure mode commands/options:
A.B.C.D Source IP address
X:X:X:X::X/<0-128> Source IPv6 address/prefix
any Abbreviation for source address/mask of
0.0.0.0/0.0.0.0 OR source prefix ::/0
any4 Abbreviation of source address and mask of 0.0.0.0
0.0.0.0
any6 Abbreviation for source prefix ::/0
host Use this keyword to configure source host
interface Use interface address as source address
object Keyword to enter source object name
object-group Network object-group for source address
object-group-security Keyword to specify security object-group for source
object-group-user Keyword to specify user object-group for source
security-group Keyword to specify inline security-group
user Keyword to specify user for source
user-group Keyword to specify user-group for source
ASA5505(config)# access-list 100 extended permit ip host ?
configure mode commands/options:
A.B.C.D Source host IPv4 address
X:X:X:X::X Source host IPv6 address
ASA5505(config)# access-list 100 extended permit ip host 192.168.1.2 ?
configure mode commands/options:
A.B.C.D Destination IP address
X:X:X:X::X/<0-128> Destination IPv6 address/prefix
any Abbreviation for destination address/mask of
0.0.0.0/0.0.0.0 OR destination prefix ::/0
any4 Abbreviation for destination address and mask of
0.0.0.0 0.0.0.0
any6 Abbreviation for destination prefix ::/0
host Use this keyword to configure destination host
interface Use interface address as destination address
object Keyword to enter destination object name
object-group Network object-group for destination address
object-group-security Keyword to specify security object-group for
destination
security-group Keyword to specify inline security-group
ASA5505(config)# access-list 100 extended permit ip host 192.168.1.2 host 192.168.1.1
ASA5505(config)# crypto map ?
configure mode commands/options:
WORD < 64 char Crypto map template tag
ASA5505(config)# crypto map 5505_IKEv1_CMAP ?
configure mode commands/options:
<1-65535> Sequence to insert into map entry
client Enable IKE extended authentication (Xauth)
interface Name of interface to apply the crypto map to
ASA5505(config)# crypto map 5505_IKEv1_CMAP 1 ?
configure mode commands/options:
annotation Specify annotation text - to be used by ASDM only
ipsec-isakmp IPSec w/ISAKMP
match Match address of packets to encrypt
set Specify crypto map settings
ASA5505(config)# crypto map 5505_IKEv1_CMAP 1 set ?
configure mode commands/options:
connection-type Specify connection-type for site-site connection based
on this entry
df-bit Set IPsec DF policy
ikev1 Configure IKEv1 policy
ikev2 Configure IKEv2 policy
nat-t-disable Disable nat-t negotiation for connections based on this
entry
peer Set IP address of peer
pfs Specify pfs settings
reverse-route Enable reverse route injection for connections based on
this entry
security-association Security association duration
tfc-packets Configure TFC packets to mask a tunnel's traffic
profile
trustpoint Specify trustpoint that defines the certificate to be
used while initiating a connection based on this entry
validate-icmp-errors Set Validate ICMP Errors
ASA5505(config)# crypto map 5505_IKEv1_CMAP 1 set peer ?
configure mode commands/options:
Hostname or A.B.C.D IP address
Hostname or X:X:X:X::X IPv6 address
ASA5505(config)# crypto map 5505_IKEv1_CMAP 1 set peer 192.168.1.1
ASA5505(config)# crypto map 5505_IKEv1_CMAP 1 set ikev1 ?
configure mode commands/options:
phase1-mode Specify mode(main or aggressive) to be used while initiating a
connection based on this entry
transform-set Specify list of transform sets in priority order
ASA5505(config)# crypto map 5505_IKEv1_CMAP 1 set ikev1 transform-set ?
configure mode commands/options:
WORD Proposal tag
ASA5505(config)# crypto map 5505_IKEv1_CMAP 1 set ikev1 transform-set 5505_IKEv1_TSET
ASA5505(config)# crypto map 5505_IKEv1_CMAP 1 match ?
configure mode commands/options:
address Match address of packets to encrypt
ASA5505(config)# crypto map 5505_IKEv1_CMAP 1 match address ?
configure mode commands/options:
WORD Access-list name
ASA5505(config)# crypto map 5505_IKEv1_CMAP 1 match address 100
ASA5505(config)# crypto map 5505_IKEv1_CMAP ?
configure mode commands/options:
<1-65535> Sequence to insert into map entry
client Enable IKE extended authentication (Xauth)
interface Name of interface to apply the crypto map to
ASA5505(config)# crypto map 5505_IKEv1_CMAP interface ?
configure mode commands/options:
Current available interface(s):
inside Name of interface Vlan1
outside Name of interface Vlan2
ASA5505(config)# crypto map 5505_IKEv1_CMAP interface outside
ASA5505(config)# tunnel-group ?
configure mode commands/options:
WORD < 65 char Enter the name of the tunnel group
ASA5505(config)# tunnel-group 192.168.1.1 ?
configure mode commands/options:
type Enter the type of this group-policy
ASA5505(config)# tunnel-group 192.168.1.1 type ?
configure mode commands/options:
ipsec-l2l IPSec Site to Site group
ipsec-ra IPSec Remote Access group (DEPRECATED)
remote-access Remote access (IPSec and WebVPN) group
webvpn WebVPN group (DEPRECATED)
ASA5505(config)# tunnel-group 192.168.1.1 type ipsec-l2l
ASA5505(config)# tunnel-group 192.168.1.1 ?
configure mode commands/options:
general-attributes Enter the general-attributes sub command mode
ipsec-attributes Enter the ipsec-attributes sub command mode
ASA5505(config)# tunnel-group 192.168.1.1 ipsec-attributes
ASA5505(config-tunnel-ipsec)# ?
tunnel-group configuration commands:
chain Enable sending certificate chain
exit Exit from tunnel-group IPSec attribute configuration mode
help Help for tunnel group configuration commands
ikev1 Configure IKEv1
ikev2 Configure IKEv2
isakmp Configure ISAKMP policy
no Remove an attribute value pair
peer-id-validate Validate identity of the peer using the peer's certificate
ASA5505(config-tunnel-ipsec)# ikev1 ?
tunnel-group-ipsec mode commands/options:
pre-shared-key Associate a pre-shared key with the connection policy
trust-point Select the trustpoint that identifies the cert to be
sent to the IKE peer
user-authentication Set the IKEv1 user authentication method
ASA5505(config-tunnel-ipsec)# ikev1 pre-shared-key ?
tunnel-group-ipsec mode commands/options:
0 Specifies an UNENCRYPTED password will follow
8 Specifies an ENCRYPTED password will follow
WORD < 129 char Enter an alphanumeric string between 1-128 characters
ASA5505(config-tunnel-ipsec)# ikev1 pre-shared-key cisco
Here are some helpful show and debug commands to troubleshoot IKEv1 IPsec site-to-site VPNs on an ASA and its equivalent commands on an IOS router:
ASA5505# show run crypto ikev1
crypto ikev1 enable outside
crypto ikev1 policy 1
authentication pre-share
encryption aes-256
hash sha
group 2
lifetime 86400
ASA5505# show run crypto ipsec
crypto ipsec ikev1 transform-set 5505_IKEv1_TSET esp-aes-256 esp-sha-hmac
ASA5505# show run crypto map
crypto map 5505_IKEv1_CMAP 1 match address 100
crypto map 5505_IKEv1_CMAP 1 set peer 192.168.1.1
crypto map 5505_IKEv1_CMAP 1 set ikev1 transform-set 5505_IKEv1_TSET
crypto map 5505_IKEv1_CMAP interface outside
ASA5505# show crypto isakmp sa
IKEv1 SAs:
Active SA: 1
Rekey SA: 0 (A tunnel will report 1 Active and 1 Rekey SA during rekey)
Total IKE SA: 1
1 IKE Peer: 192.168.1.1
Type : L2L Role : responder
Rekey : no State : MM_ACTIVE // QM_IDLE ON IOS ROUTER
There are no IKEv2 SAs
ASA5505# show crypto ipsec sa
interface: outside
Crypto map tag: 5505_IKEv1_CMAP, seq num: 1, local addr: 192.168.1.2
access-list 100 extended permit ip host 192.168.1.2 host 192.168.1.1
local ident (addr/mask/prot/port): (192.168.1.2/255.255.255.255/0/0)
remote ident (addr/mask/prot/port): (192.168.1.1/255.255.255.255/0/0)
current_peer: 192.168.1.1
#pkts encaps: 4, #pkts encrypt: 4, #pkts digest: 4
#pkts decaps: 4, #pkts decrypt: 4, #pkts verify: 4
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 4, #pkts comp failed: 0, #pkts decomp failed: 0
#pre-frag successes: 0, #pre-frag failures: 0, #fragments created: 0
#PMTUs sent: 0, #PMTUs rcvd: 0, #decapsulated frgs needing reassembly: 0
#TFC rcvd: 0, #TFC sent: 0
#Valid ICMP Errors rcvd: 0, #Invalid ICMP Errors rcvd: 0
#send errors: 0, #recv errors: 0
local crypto endpt.: 192.168.1.2/0, remote crypto endpt.: 192.168.1.1/0
path mtu 1500, ipsec overhead 74(44), media mtu 1500
PMTU time remaining (sec): 0, DF policy: copy-df
ICMP error validation: disabled, TFC packets: disabled
current outbound spi: A21332F0
current inbound spi : AF168576
inbound esp sas:
spi: 0xAF168576 (2937488758)
transform: esp-aes-256 esp-sha-hmac no compression
in use settings ={L2L, Tunnel, IKEv1, }
slot: 0, conn_id: 4096, crypto-map: 5505_IKEv1_CMAP
sa timing: remaining key lifetime (kB/sec): (4373999/3557)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x0000001F
outbound esp sas:
spi: 0xA21332F0 (2719167216)
transform: esp-aes-256 esp-sha-hmac no compression
in use settings ={L2L, Tunnel, IKEv1, }
slot: 0, conn_id: 4096, crypto-map: 5505_IKEv1_CMAP
sa timing: remaining key lifetime (kB/sec): (4373999/3557)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x00000001
871W#show crypto isakmp sa
IPv4 Crypto ISAKMP SA
dst src state conn-id slot status
192.168.1.2 192.168.1.1 QM_IDLE 2001 0 ACTIVE
IPv6 Crypto ISAKMP SA
871W#show crypto ipsec sa
interface: BVI1
Crypto map tag: 871_IKEv1_CMAP, local addr 192.168.1.1
protected vrf: (none)
local ident (addr/mask/prot/port): (192.168.1.1/255.255.255.255/0/0)
remote ident (addr/mask/prot/port): (192.168.1.2/255.255.255.255/0/0)
current_peer 192.168.1.2 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 4, #pkts encrypt: 4, #pkts digest: 4
#pkts decaps: 4, #pkts decrypt: 4, #pkts verify: 4
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 1, #recv errors 0
local crypto endpt.: 192.168.1.1, remote crypto endpt.: 192.168.1.2
path mtu 1500, ip mtu 1500, ip mtu idb BVI1
current outbound spi: 0xAF168576(2937488758)
inbound esp sas:
spi: 0xA21332F0(2719167216)
transform: esp-256-aes esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 1, flow_id: Motorola SEC 1.0:1, crypto map: 871_IKEv1_CMAP
sa timing: remaining key lifetime (k/sec): (4472107/3511)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0xAF168576(2937488758)
transform: esp-256-aes esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 2, flow_id: Motorola SEC 1.0:2, crypto map: 871_IKEv1_CMAP
sa timing: remaining key lifetime (k/sec): (4472107/3511)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE
outbound ah sas:
outbound pcp sas:
ASA5505# debug crypto ?
ca Set PKI debug levels
condition Set IPSec/ISAKMP debug filters
engine Set crypto engine debug levels
ike-common Set IKE common debug levels
ikev1 Set IKEV1 debug levels
ikev2 Set IKEV2 debug levels
ipsec Set IPSec debug levels
ss-api Set Crypto Secure Socket API debug levels
vpnclient Set EasyVPN client debug levels
ASA5505# debug crypto ikev1 ?
<1-255> Specify an optional debug level (default is 1)
timers debug the ikev1 timers
<cr>
ASA5505# debug crypto ikev1 255
ASA5505# Jul 27 15:47:06 [IKEv1 DEBUG]Group = 192.168.1.1, IP = 192.168.1.1, Sending keep-alive of type DPD R-U-THERE (seq number 0xfa85369)
Jul 27 15:47:06 [IKEv1 DEBUG]Group = 192.168.1.1, IP = 192.168.1.1, constructing blank hash payload
Jul 27 15:47:06 [IKEv1 DEBUG]Group = 192.168.1.1, IP = 192.168.1.1, constructing qm hash payload
Jul 27 15:47:06 [IKEv1]IP = 192.168.1.1, IKE_DECODE SENDING Message (msgid=c2227fd5) with payloads : HDR + HASH (8) + NOTIFY (11) + NONE (0) total length : 84
BEFORE ENCRYPTION
RAW PACKET DUMP on SEND
8e f0 e6 3e 21 0f 48 19 f9 0b 79 51 46 e5 b2 44 | ...>!.H...yQF..D
08 10 05 00 d5 7f 22 c2 1c 00 00 00 0b 00 00 18 | .....".........
0b 1c 28 95 78 17 70 07 09 7d 37 14 db 49 8c 48 | ..(.x.p..}7..I.H
ce 14 9a 4b 00 00 00 20 00 00 00 01 01 10 8d 28 | ...K... .......(
8e f0 e6 3e 21 0f 48 19 f9 0b 79 51 46 e5 b2 44 | ...>!.H...yQF..D
0f a8 53 69 | ..Si
ISAKMP Header
Initiator COOKIE: 8e f0 e6 3e 21 0f 48 19
Responder COOKIE: f9 0b 79 51 46 e5 b2 44
Next Payload: Hash
Version: 1.0
Exchange Type: Informational
Flags: (none)
MessageID: D57F22C2
Length: 469762048
Payload Hash
Next Payload: Notification
Reserved: 00
Payload Length: 24
Data:
0b 1c 28 95 78 17 70 07 09 7d 37 14 db 49 8c 48
ce 14 9a 4b
Payload Notification
Next Payload: None
Reserved: 00
Payload Length: 32
DOI: IPsec
Protocol-ID: PROTO_ISAKMP
Spi Size: 16
Notify Type: R_U_THERE
SPI:
8e f0 e6 3e 21 0f 48 19 f9 0b 79 51 46 e5 b2 44
Data: 0f a8 53 69
ISAKMP Header
Initiator COOKIE: 8e f0 e6 3e 21 0f 48 19
Responder COOKIE: f9 0b 79 51 46 e5 b2 44
Next Payload: Hash
Version: 1.0
Exchange Type: Informational
Flags: (Encryption)
MessageID: C2227FD5
Length: 92
IKE Recv RAW packet dump
8e f0 e6 3e 21 0f 48 19 f9 0b 79 51 46 e5 b2 44 | ...>!.H...yQF..D
08 10 05 01 1f 35 1f 3c 00 00 00 5c 00 4d bb 90 | .....5.<...\.M..
f3 85 9b 86 93 bb ab 22 d6 23 ef 7e e2 ad 16 65 | .......".#.~...e
62 1d 69 00 82 5c 34 86 74 fb c9 3a 6b 49 ab 08 | b.i..\4.t..:kI..
2c ff 94 d2 83 bb d4 1a 0c e7 53 29 ea b4 80 95 | ,.........S)....
13 31 8c 09 39 12 1a a4 76 bc d4 dd | .1..9...v...
RECV PACKET from 192.168.1.1
ISAKMP Header
Initiator COOKIE: 8e f0 e6 3e 21 0f 48 19
Responder COOKIE: f9 0b 79 51 46 e5 b2 44
Next Payload: Hash
Version: 1.0
Exchange Type: Informational
Flags: (Encryption)
MessageID: 1F351F3C
Length: 92
AFTER DECRYPTION
ISAKMP Header
Initiator COOKIE: 8e f0 e6 3e 21 0f 48 19
Responder COOKIE: f9 0b 79 51 46 e5 b2 44
Next Payload: Hash
Version: 1.0
Exchange Type: Informational
Flags: (Encryption)
MessageID: 1F351F3C
Length: 92
Payload Hash
Next Payload: Notification
Reserved: 00
Payload Length: 24
Data:
88 af 61 fc 7e ee 2c 17 b5 85 99 47 2a e5 96 e4
3d ce a7 94
Payload Notification
Next Payload: None
Reserved: 00
Payload Length: 32
DOI: IPsec
Protocol-ID: PROTO_ISAKMP
Spi Size: 16
Notify Type: R_U_THERE_ACK
SPI:
8e f0 e6 3e 21 0f 48 19 f9 0b 79 51 46 e5 b2 44
Data: 0f a8 53 69
Jul 27 15:47:06 [IKEv1]IP = 192.168.1.1, IKE_DECODE RECEIVED Message (msgid=1f351f3c) with payloads : HDR + HASH (8) + NOTIFY (11) + NONE (0) total length : 84
Jul 27 15:47:06 [IKEv1 DEBUG]Group = 192.168.1.1, IP = 192.168.1.1, processing hash payload
Jul 27 15:47:06 [IKEv1 DEBUG]Group = 192.168.1.1, IP = 192.168.1.1, processing notify payload
Jul 27 15:47:06 [IKEv1 DEBUG]Group = 192.168.1.1, IP = 192.168.1.1, Received keep-alive of type DPD R-U-THERE-ACK (seq number 0xfa85369)
Jul 27 15:47:16 [IKEv1 DEBUG]Group = 192.168.1.1, IP = 192.168.1.1, Sending keep-alive of type DPD R-U-THERE (seq number 0xfa8536a)
Jul 27 15:47:16 [IKEv1 DEBUG]Group = 192.168.1.1, IP = 192.168.1.1, constructing blank hash payload
Jul 27 15:47:16 [IKEv1 DEBUG]Group = 192.168.1.1, IP = 192.168.1.1, constructing qm hash payload
Jul 27 15:47:16 [IKEv1]IP = 192.168.1.1, IKE_DECODE SENDING Message (msgid=86feac10) with payloads : HDR + HASH (8) + NOTIFY (11) + NONE (0) total length : 84
BEFORE ENCRYPTION
RAW PACKET DUMP on SEND
8e f0 e6 3e 21 0f 48 19 f9 0b 79 51 46 e5 b2 44 | ...>!.H...yQF..D
08 10 05 00 10 ac fe 86 1c 00 00 00 0b 00 00 18 | ................
e9 ee f3 46 cb a6 4b 95 0d f0 c7 83 48 a5 75 50 | ...F..K.....H.uP
a0 49 b4 d9 00 00 00 20 00 00 00 01 01 10 8d 28 | .I..... .......(
8e f0 e6 3e 21 0f 48 19 f9 0b 79 51 46 e5 b2 44 | ...>!.H...yQF..D
0f a8 53 6a | ..Sj
ISAKMP Header
Initiator COOKIE: 8e f0 e6 3e 21 0f 48 19
Responder COOKIE: f9 0b 79 51 46 e5 b2 44
Next Payload: Hash
Version: 1.0
Exchange Type: Informational
Flags: (none)
MessageID: 10ACFE86
Length: 469762048
Payload Hash
Next Payload: Notification
Reserved: 00
Payload Length: 24
Data:
e9 ee f3 46 cb a6 4b 95 0d f0 c7 83 48 a5 75 50
a0 49 b4 d9
Payload Notification
Next Payload: None
Reserved: 00
Payload Length: 32
DOI: IPsec
Protocol-ID: PROTO_ISAKMP
Spi Size: 16
Notify Type: R_U_THERE
SPI:
8e f0 e6 3e 21 0f 48 19 f9 0b 79 51 46 e5 b2 44
Data: 0f a8 53 6a
ISAKMP Header
Initiator COOKIE: 8e f0 e6 3e 21 0f 48 19
Responder COOKIE: f9 0b 79 51 46 e5 b2 44
Next Payload: Hash
Version: 1.0
Exchange Type: Informational
Flags: (Encryption)
MessageID: 86FEAC10
Length: 92
IKE Recv RAW packet dump
8e f0 e6 3e 21 0f 48 19 f9 0b 79 51 46 e5 b2 44 | ...>!.H...yQF..D
08 10 05 01 9c c2 18 86 00 00 00 5c e2 d6 cb 79 | ...........\...y
77 f5 33 51 aa 10 b5 7f 7c 9c 08 da e2 7a 18 d7 | w.3Q...|....z..
93 8f ff 73 bf ce 66 40 8c 81 28 ec 50 ad 58 af | ...s..f@..(.P.X.
8c 64 42 b1 88 ea 12 2b 50 ce cf c8 d7 4e 5c 6e | .dB....+P....N\n
e0 48 b8 b9 a5 d6 f2 b8 c7 d8 1e 16 | .H..........
RECV PACKET from 192.168.1.1
ISAKMP Header
Initiator COOKIE: 8e f0 e6 3e 21 0f 48 19
Responder COOKIE: f9 0b 79 51 46 e5 b2 44
Next Payload: Hash
Version: 1.0
Exchange Type: Informational
Flags: (Encryption)
MessageID: 9CC21886
Length: 92
AFTER DECRYPTION
ISAKMP Header
Initiator COOKIE: 8e f0 e6 3e 21 0f 48 19
Responder COOKIE: f9 0b 79 51 46 e5 b2 44
Next Payload: Hash
Version: 1.0
Exchange Type: Informational
Flags: (Encryption)
MessageID: 9CC21886
Length: 92
Payload Hash
Next Payload: Notification
Reserved: 00
Payload Length: 24
Data:
9e 3b ae fa 17 d3 f0 0d a3 80 7a 6f 04 13 e0 b8
d4 00 6e ba
Payload Notification
Next Payload: None
Reserved: 00
Payload Length: 32
DOI: IPsec
Protocol-ID: PROTO_ISAKMP
Spi Size: 16
Notify Type: R_U_THERE_ACK
SPI:
8e f0 e6 3e 21 0f 48 19 f9 0b 79 51 46 e5 b2 44
Data: 0f a8 53 6a
Jul 27 15:47:16 [IKEv1]IP = 192.168.1.1, IKE_DECODE RECEIVED Message (msgid=9cc21886) with payloads : HDR + HASH (8) + NOTIFY (11) + NONE (0) total length : 84
Jul 27 15:47:16 [IKEv1 DEBUG]Group = 192.168.1.1, IP = 192.168.1.1, processing hash payload
Jul 27 15:47:16 [IKEv1 DEBUG]Group = 192.168.1.1, IP = 192.168.1.1, processing notify payload
Jul 27 15:47:16 [IKEv1 DEBUG]Group = 192.168.1.1, IP = 192.168.1.1, Received keep-alive of type DPD R-U-THERE-ACK (seq number 0xfa8536a)
However, the actual processes of key exchange and parameter negotiation are carried out by two protocols used by IKEv1:
* Internet Security Association and Key Management Protocol (ISAKMP)
* Oakley
ISAKMP takes care of parameter negotiation between peers (for example, DH groups, lifetimes, encryption and authentication). The process of negotiating these parameters between peers is required for the successful establishment of SAs. After an SA has been established, ISAKMP defines the procedures followed for correct maintenance and removal of the SA during connection termination.
Note: You will often find the terms ISAKMP and IKE used interchangeably in earlier versions of ASA (pre 8.4) and IOS reference IKEv1 functions and parameters.
Two mandatory IKEv1 phases (aptly named IKEv1 Phase 1 and IKEv1 Phase 2) must be followed by each peer before a communications tunnel can be established between them and they are ready for successful data transmision:
* IKEv1 Phase 1: During this phase, both peers negotiate parameters (integrity and encryption algorithms, authentication methods) to set up a secure and authenticated tunnel. This is also called a management channel because no user data is flowing through it (and it is actually a bidirectional IKE SA). Its sole scope is to handle secure Phase 2 negotiations. It is called bidirectional because both peers use only one session key to secure both incoming and outgoing traffic. Peer authentication can be carried out by one of the following methods:
- Pre-shared keys
- Digital certificates
* IKEv1 Phase 2: This second mandatory phase uses the negotiated parameters in Phase 1 for secure IPsec SA creation. However, unlike the single bidirectional SA created within Phase 1, the IPsec SA are unidirectional, meaning a different session key is used for each direction (one for inbound, or decrypted, traffic, and one for outbound, or encrypted, traffic). This is applicable for any administrator-configured source-destination network pair. Therefore, you might end up with four unidirectional IPsec SAs if you have two source-destination network pairs defined in a VPN policy.
I used my 871w IOS router and ASA 5505 firewall to establish an IKEv1 IPsec site-to-site VPN tunnel. This will help demonstrate the similarities and differences in configuring and troubleshooting for IKE Phase 1 and IKE Phase 2 VPN policies.
871W(config)#crypto ?
ca Certification authority
call Configure Crypto Call Admission Control
ctcp Configure cTCP encapsulation
dynamic-map Specify a dynamic crypto map template
engine Enter a crypto engine configurable menu
gdoi Configure GDOI policy
identity Enter a crypto identity list
ipsec Configure IPSEC policy
isakmp Configure ISAKMP policy
key Long term key operations
keyring Key ring commands
logging logging messages
map Enter a crypto map
mib Configure Crypto-related MIB Parameters
pki Public Key components
provisioning Secure Device Provisioning
wui Crypto HTTP configuration interfaces
xauth X-Auth parameters
871W(config)#crypto isakmp ?
aggressive-mode Disable ISAKMP aggressive mode
client Set client configuration policy
enable Enable ISAKMP
fragmentation IKE Fragmentation enabled if required
identity Set the identity which ISAKMP will use
invalid-spi-recovery Initiate IKE and send Invalid SPI Notify
keepalive Set a keepalive interval for use with IOS peers
key Set pre-shared key for remote peer
nat Set a nat keepalive interval for use with IOS peers
peer Set Peer Policy
policy Set policy for an ISAKMP protection suite
profile Define ISAKMP Profiles
xauth Set Extended Authentication values
871W(config)#crypto isakmp policy ?
<1-10000> Priority of protection suite
871W(config)#crypto isakmp policy 1 // IKE PHASE 1 POLICY; LOWER NUMBER PREFERRED
871W(config-isakmp)#?
ISAKMP commands:
authentication Set authentication method for protection suite
default Set a command to its defaults
encryption Set encryption algorithm for protection suite
exit Exit from ISAKMP protection suite configuration mode
group Set the Diffie-Hellman group
hash Set hash algorithm for protection suite
lifetime Set lifetime for ISAKMP security association
no Negate a command or set its defaults
871W(config-isakmp)#authentication ?
pre-share Pre-Shared Key
rsa-encr Rivest-Shamir-Adleman Encryption
rsa-sig Rivest-Shamir-Adleman Signature
871W(config-isakmp)#authentication pre-share
871W(config-isakmp)#encryption ?
3des Three key triple DES
aes AES - Advanced Encryption Standard.
des DES - Data Encryption Standard (56 bit keys).
871W(config-isakmp)#encryption aes ?
128 128 bit keys.
192 192 bit keys.
256 256 bit keys.
<cr>
871W(config-isakmp)#encryption aes 256 // USE STRONGER ALGORITHMS ON LOWER POLICY
871W(config-isakmp)#hash ?
md5 Message Digest 5
sha Secure Hash Standard
871W(config-isakmp)#hash sha
871W(config-isakmp)#group ?
1 Diffie-Hellman group 1
2 Diffie-Hellman group 2
5 Diffie-Hellman group 5
871W(config-isakmp)#group 2 // DEFAULT DH GROUP
871W(config-isakmp)#lifetime ?
<60-86400> lifetime in seconds
871W(config-isakmp)#lifetime 43200 // LOWER LIFETIME WILL BE CHOSEN BETWEEN VPN PEERS
871W(config-isakmp)#exit
871W(config)#crypto isakmp ?
aggressive-mode Disable ISAKMP aggressive mode
client Set client configuration policy
enable Enable ISAKMP
fragmentation IKE Fragmentation enabled if required
identity Set the identity which ISAKMP will use
invalid-spi-recovery Initiate IKE and send Invalid SPI Notify
keepalive Set a keepalive interval for use with IOS peers
key Set pre-shared key for remote peer
nat Set a nat keepalive interval for use with IOS peers
peer Set Peer Policy
policy Set policy for an ISAKMP protection suite
profile Define ISAKMP Profiles
xauth Set Extended Authentication values
871W(config)#crypto isakmp key ?
0 Specifies an UNENCRYPTED password will follow
6 Specifies an ENCRYPTED password will follow
871W(config)#crypto isakmp key 6 ?
WORD The HIDDEN user password string
871W(config)#crypto isakmp key 6 cisco ?
address define shared key with IP address
hostname define shared key with hostname
871W(config)#crypto isakmp key 6 cisco address ?
A.B.C.D Peer IP address
ipv6 define shared key with IPv6 address
871W(config)#crypto isakmp key 6 cisco address 192.168.1.2
871W(config)#crypto ipsec ?
client Configure a client
df-bit Handling of encapsulated DF bit.
fragmentation Handling of fragmentation of near-MTU sized packets
nat-transparency IPsec NAT transparency model
optional Enable optional encryption for IPSec
profile Configure an ipsec policy profile
security-association Security association parameters
transform-set Define transform and settings
871W(config)#crypto ipsec transform-set ?
WORD Transform set tag
871W(config)#crypto ipsec transform-set 871_IKEv1_TSET ?
ah-md5-hmac AH-HMAC-MD5 transform
ah-sha-hmac AH-HMAC-SHA transform
comp-lzs IP Compression using the LZS compression algorithm
esp-3des ESP transform using 3DES(EDE) cipher (168 bits)
esp-aes ESP transform using AES cipher
esp-des ESP transform using DES cipher (56 bits)
esp-md5-hmac ESP transform using HMAC-MD5 auth
esp-null ESP transform w/o cipher
esp-seal ESP transform using SEAL cipher (160 bits)
esp-sha-hmac ESP transform using HMAC-SHA auth
871W(config)#crypto ipsec transform-set 871_IKEv1_TSET esp-aes ?
128 128 bit keys.
192 192 bit keys.
256 256 bit keys.
ah-md5-hmac AH-HMAC-MD5 transform
ah-sha-hmac AH-HMAC-SHA transform
comp-lzs IP Compression using the LZS compression algorithm
esp-md5-hmac ESP transform using HMAC-MD5 auth
esp-sha-hmac ESP transform using HMAC-SHA auth
<cr>
871W(config)#crypto ipsec transform-set 871_IKEv1_TSET esp-aes 256 ?
ah-md5-hmac AH-HMAC-MD5 transform
ah-sha-hmac AH-HMAC-SHA transform
comp-lzs IP Compression using the LZS compression algorithm
esp-md5-hmac ESP transform using HMAC-MD5 auth
esp-sha-hmac ESP transform using HMAC-SHA auth
<cr>
871W(config)#crypto ipsec transform-set 871_IKEv1_TSET esp-aes 256 esp-sha-hmac // IKE PHASE 2 POLICY
871W(cfg-crypto-trans)#exit
871W(config)#access-list ?
<1-99> IP standard access list
<100-199> IP extended access list
<1100-1199> Extended 48-bit MAC address access list
<1300-1999> IP standard access list (expanded range)
<200-299> Protocol type-code access list
<2000-2699> IP extended access list (expanded range)
<700-799> 48-bit MAC address access list
dynamic-extended Extend the dynamic ACL absolute timer
rate-limit Simple rate-limit specific access list
871W(config)#access-list 100 ?
deny Specify packets to reject
dynamic Specify a DYNAMIC list of PERMITs or DENYs
permit Specify packets to forward
remark Access list entry comment
871W(config)#access-list 100 permit ?
<0-255> An IP protocol number
ahp Authentication Header Protocol
eigrp Cisco's EIGRP routing protocol
esp Encapsulation Security Payload
gre Cisco's GRE tunneling
icmp Internet Control Message Protocol
igmp Internet Gateway Message Protocol
ip Any Internet Protocol
ipinip IP in IP tunneling
nos KA9Q NOS compatible IP over IP tunneling
ospf OSPF routing protocol
pcp Payload Compression Protocol
tcp Transmission Control Protocol
udp User Datagram Protocol
871W(config)#access-list 100 permit ip ?
A.B.C.D Source address
any Any source host
host A single source host
871W(config)#access-list 100 permit ip host 192.168.1.1 host 192.168.1.2 // CRYPTO ACL; REMOTE VPN ACL MUST BE REVERSED (MIRRORED)
871W(config)#crypto map ?
WORD Crypto map tag
871W(config)#crypto map 871_IKEv1_CMAP ?
<1-65535> Sequence to insert into crypto map entry
client Specify client configuration settings
isakmp Specify isakmp configuration settings
isakmp-profile Specify isakmp profile to use
local-address Interface to use for local address for this crypto map
redundancy High availability options for this map
871W(config)#crypto map 871_IKEv1_CMAP 1 ?
gdoi GDOI
ipsec-isakmp IPSEC w/ISAKMP
ipsec-manual IPSEC w/manual keying
<cr>
871W(config)#crypto map 871_IKEv1_CMAP 1 ipsec-isakmp
% NOTE: This new crypto map will remain disabled until a peer
and a valid access list have been configured.
871W(config-crypto-map)#?
Crypto Map configuration commands:
default Set a command to its defaults
description Description of the crypto map statement policy
dialer Dialer related commands
exit Exit from crypto map configuration mode
match Match values.
no Negate a command or set its defaults
reverse-route Reverse Route Injection.
set Set values for encryption/decryption
871W(config-crypto-map)#set ?
identity Identity restriction.
ip Interface Internet Protocol config commands
isakmp-profile Specify isakmp Profile
nat Set NAT translation
peer Allowed Encryption/Decryption peer.
pfs Specify pfs settings
reverse-route Reverse Route Injection.
security-association Security association parameters
transform-set Specify list of transform sets in priority order
871W(config-crypto-map)#set peer ?
A.B.C.D IP address of peer
WORD Host name of the peer
871W(config-crypto-map)#set peer 192.168.1.2
871W(config-crypto-map)#set transform-set ?
WORD Proposal tag
871W(config-crypto-map)#set transform-set 871_IKEv1_TSET
871W(config-crypto-map)#match ?
address Match address of packets to encrypt.
871W(config-crypto-map)#match address ?
<100-199> IP access-list number
<2000-2699> IP access-list number (expanded range)
WORD Access-list name
871W(config-crypto-map)#match address 100
871W(config-crypto-map)#exit
871W(config)#interface bvi1
871W(config-if)#ip address 192.168.1.1
871W(config-if)#crypto map 871_IKEv1_CMAP
----
ASA5505(config)# crypto ?
configure mode commands/options:
ca Certification authority
dynamic-map Configure a dynamic crypto map
ikev1 Configure IKEv1 policy
ikev2 Configure IKEv2 policy
ipsec Configure transform-set, IPSec SA lifetime, and fragmentation
isakmp Configure ISAKMP
key Long term key operations
map Configure a crypto map
exec mode commands/options:
ca Certification authority
ASA5505(config)# crypto ikev1 ?
configure mode commands/options:
am-disable Disable inbound aggressive mode connections
enable Enable IKEv1 on the specified interface
ipsec-over-tcp Enable and configure IPSec over TCP
policy Set IKEv1 policy suite
ASA5505(config)# crypto ikev1 enable ?
configure mode commands/options:
Type an interface name to enable
inside Name of interface Vlan1
outside Name of interface Vlan2
ASA5505(config)# crypto ikev1 enable outside
ASA5505(config)# crypto ikev1 policy ?
configure mode commands/options:
<1-65535> Policy suite priority(1 highest, 65535 lowest)
ASA5505(config)# crypto ikev1 policy 1 // IKE PHASE 1 POLICY
ASA5505(config-ikev1-policy)# ?
crypto ikev1 policy configuration commands:
authentication Set authentication method (pre-share or rsa-sig)
encryption Set encryption algorithm (des, 3des, aes-128, aes-192, or
aes-256)
exit Exit from crypto ikev1 policy configuration mode
group Set Diffie-Hellman group (1,2 or 5)
hash Set hash algorithm (md5 or sha1)
help Help for crypto ikev1 policy configuration commands
lifetime Set IKEV1 SA lifetime (seconds)
no Negate a command or set its defaults
<cr>
ASA5505(config-ikev1-policy)# authentication ?
ikev1-policy mode commands/options:
crack set auth crack
pre-share set auth pre-share
rsa-sig set auth rsa-sig
ASA5505(config-ikev1-policy)# authentication pre-share
ASA5505(config-ikev1-policy)# encryption ?
ikev1-policy mode commands/options:
3des 3des encryption
aes aes-128 encryption
aes-192 aes-192 encryption
aes-256 aes-256 encryption
des des encryption
ASA5505(config-ikev1-policy)# encryption aes-256
ASA5505(config-ikev1-policy)# hash ?
ikev1-policy mode commands/options:
md5 set hash md5
sha set hash sha1
ASA5505(config-ikev1-policy)# hash sha
ASA5505(config-ikev1-policy)# group ?
ikev1-policy mode commands/options:
1 Diffie-Hellman group 1
2 Diffie-Hellman group 2
5 Diffie-Hellman group 5
7 Diffie-Hellman group 7 (DEPRECATED)
ASA5505(config-ikev1-policy)# group 2
ASA5505(config-ikev1-policy)# lifetime 86400 // 43200 SECONDS WILL BE CHOSEN
ASA5505(config-ikev1-policy)# exit
ASA5505(config)# crypto ipsec ?
configure mode commands/options:
df-bit Set IPsec DF policy
fragmentation Set IPsec fragmentation policy
ikev1 Set IKEv1 settings
ikev2 Set IKEv2 settings
security-association Set security association parameters
ASA5505(config)# crypto ipsec ikev1 ?
configure mode commands/options:
transform-set Define transform and settings
ASA5505(config)# crypto ipsec ikev1 transform-set ?
configure mode commands/options:
WORD < 64 char Transform set tag
ASA5505(config)# crypto ipsec ikev1 transform-set 5505_IKEv1_TSET ?
configure mode commands/options:
esp-3des esp 3des encryption
esp-aes esp aes 128 encryption
esp-aes-192 esp aes 192 encryption
esp-aes-256 esp aes 256 encryption
esp-des esp des encryption
esp-md5-hmac esp md5 authentication
esp-none esp no authentication
esp-null esp null encryption
esp-sha-hmac esp sha authentication
mode mode transport
ASA5505(config)# crypto ipsec ikev1 transform-set 5505_IKEv1_TSET esp-aes-256 ?
configure mode commands/options:
esp-3des esp 3des encryption
esp-aes esp aes 128 encryption
esp-aes-192 esp aes 192 encryption
esp-aes-256 esp aes 256 encryption
esp-des esp des encryption
esp-md5-hmac esp md5 authentication
esp-none esp no authentication
esp-null esp null encryption
esp-sha-hmac esp sha authentication
<cr>
ASA5505(config)# crypto ipsec ikev1 transform-set 5505_IKEv1_TSET esp-aes-256 esp-sha-hmac // IKE PHASE 2 POLICY
ASA5505(config)# access-list ?
configure mode commands/options:
WORD < 241 char Access list identifier
alert-interval Specify the alert interval for generating syslog message
106001 which alerts that the system has reached a deny flow
maximum. If not specified, the default value is 300 sec
deny-flow-max Specify the maximum number of concurrent deny flows that can
be created. If not specified, the default value is 4096
ASA5505(config)# access-list 100 ?
configure mode commands/options:
deny Specify packets to reject
extended Configure access policy for IP traffic through the system
line Use this to specify line number at which ACE should be entered
permit Specify packets to forward
remark Specify a comment (remark) for the access-list after this keyword
rename rename an existing access-list
standard Use this to configure policy having destination host or network
only
webtype Use this to configure WebVPN related policy
ASA5505(config)# access-list 100 extended ?
configure mode commands/options:
deny Specify packets to reject
permit Specify packets to forward
ASA5505(config)# access-list 100 extended permit ?
configure mode commands/options:
<0-255> Enter protocol number (0 - 255)
ah
eigrp
esp
gre
icmp
icmp6
igmp
igrp
ip
ipinip
ipsec
nos
object Specify a service object after this keyword
object-group Specify a service or protocol object-group after this keyword
ospf
pcp
pim
pptp
snp
tcp
udp
ASA5505(config)# access-list 100 extended permit ip ?
configure mode commands/options:
A.B.C.D Source IP address
X:X:X:X::X/<0-128> Source IPv6 address/prefix
any Abbreviation for source address/mask of
0.0.0.0/0.0.0.0 OR source prefix ::/0
any4 Abbreviation of source address and mask of 0.0.0.0
0.0.0.0
any6 Abbreviation for source prefix ::/0
host Use this keyword to configure source host
interface Use interface address as source address
object Keyword to enter source object name
object-group Network object-group for source address
object-group-security Keyword to specify security object-group for source
object-group-user Keyword to specify user object-group for source
security-group Keyword to specify inline security-group
user Keyword to specify user for source
user-group Keyword to specify user-group for source
ASA5505(config)# access-list 100 extended permit ip host ?
configure mode commands/options:
A.B.C.D Source host IPv4 address
X:X:X:X::X Source host IPv6 address
ASA5505(config)# access-list 100 extended permit ip host 192.168.1.2 ?
configure mode commands/options:
A.B.C.D Destination IP address
X:X:X:X::X/<0-128> Destination IPv6 address/prefix
any Abbreviation for destination address/mask of
0.0.0.0/0.0.0.0 OR destination prefix ::/0
any4 Abbreviation for destination address and mask of
0.0.0.0 0.0.0.0
any6 Abbreviation for destination prefix ::/0
host Use this keyword to configure destination host
interface Use interface address as destination address
object Keyword to enter destination object name
object-group Network object-group for destination address
object-group-security Keyword to specify security object-group for
destination
security-group Keyword to specify inline security-group
ASA5505(config)# access-list 100 extended permit ip host 192.168.1.2 host 192.168.1.1
ASA5505(config)# crypto map ?
configure mode commands/options:
WORD < 64 char Crypto map template tag
ASA5505(config)# crypto map 5505_IKEv1_CMAP ?
configure mode commands/options:
<1-65535> Sequence to insert into map entry
client Enable IKE extended authentication (Xauth)
interface Name of interface to apply the crypto map to
ASA5505(config)# crypto map 5505_IKEv1_CMAP 1 ?
configure mode commands/options:
annotation Specify annotation text - to be used by ASDM only
ipsec-isakmp IPSec w/ISAKMP
match Match address of packets to encrypt
set Specify crypto map settings
ASA5505(config)# crypto map 5505_IKEv1_CMAP 1 set ?
configure mode commands/options:
connection-type Specify connection-type for site-site connection based
on this entry
df-bit Set IPsec DF policy
ikev1 Configure IKEv1 policy
ikev2 Configure IKEv2 policy
nat-t-disable Disable nat-t negotiation for connections based on this
entry
peer Set IP address of peer
pfs Specify pfs settings
reverse-route Enable reverse route injection for connections based on
this entry
security-association Security association duration
tfc-packets Configure TFC packets to mask a tunnel's traffic
profile
trustpoint Specify trustpoint that defines the certificate to be
used while initiating a connection based on this entry
validate-icmp-errors Set Validate ICMP Errors
ASA5505(config)# crypto map 5505_IKEv1_CMAP 1 set peer ?
configure mode commands/options:
Hostname or A.B.C.D IP address
Hostname or X:X:X:X::X IPv6 address
ASA5505(config)# crypto map 5505_IKEv1_CMAP 1 set peer 192.168.1.1
ASA5505(config)# crypto map 5505_IKEv1_CMAP 1 set ikev1 ?
configure mode commands/options:
phase1-mode Specify mode(main or aggressive) to be used while initiating a
connection based on this entry
transform-set Specify list of transform sets in priority order
ASA5505(config)# crypto map 5505_IKEv1_CMAP 1 set ikev1 transform-set ?
configure mode commands/options:
WORD Proposal tag
ASA5505(config)# crypto map 5505_IKEv1_CMAP 1 set ikev1 transform-set 5505_IKEv1_TSET
ASA5505(config)# crypto map 5505_IKEv1_CMAP 1 match ?
configure mode commands/options:
address Match address of packets to encrypt
ASA5505(config)# crypto map 5505_IKEv1_CMAP 1 match address ?
configure mode commands/options:
WORD Access-list name
ASA5505(config)# crypto map 5505_IKEv1_CMAP 1 match address 100
ASA5505(config)# crypto map 5505_IKEv1_CMAP ?
configure mode commands/options:
<1-65535> Sequence to insert into map entry
client Enable IKE extended authentication (Xauth)
interface Name of interface to apply the crypto map to
ASA5505(config)# crypto map 5505_IKEv1_CMAP interface ?
configure mode commands/options:
Current available interface(s):
inside Name of interface Vlan1
outside Name of interface Vlan2
ASA5505(config)# crypto map 5505_IKEv1_CMAP interface outside
ASA5505(config)# tunnel-group ?
configure mode commands/options:
WORD < 65 char Enter the name of the tunnel group
ASA5505(config)# tunnel-group 192.168.1.1 ?
configure mode commands/options:
type Enter the type of this group-policy
ASA5505(config)# tunnel-group 192.168.1.1 type ?
configure mode commands/options:
ipsec-l2l IPSec Site to Site group
ipsec-ra IPSec Remote Access group (DEPRECATED)
remote-access Remote access (IPSec and WebVPN) group
webvpn WebVPN group (DEPRECATED)
ASA5505(config)# tunnel-group 192.168.1.1 type ipsec-l2l
ASA5505(config)# tunnel-group 192.168.1.1 ?
configure mode commands/options:
general-attributes Enter the general-attributes sub command mode
ipsec-attributes Enter the ipsec-attributes sub command mode
ASA5505(config)# tunnel-group 192.168.1.1 ipsec-attributes
ASA5505(config-tunnel-ipsec)# ?
tunnel-group configuration commands:
chain Enable sending certificate chain
exit Exit from tunnel-group IPSec attribute configuration mode
help Help for tunnel group configuration commands
ikev1 Configure IKEv1
ikev2 Configure IKEv2
isakmp Configure ISAKMP policy
no Remove an attribute value pair
peer-id-validate Validate identity of the peer using the peer's certificate
ASA5505(config-tunnel-ipsec)# ikev1 ?
tunnel-group-ipsec mode commands/options:
pre-shared-key Associate a pre-shared key with the connection policy
trust-point Select the trustpoint that identifies the cert to be
sent to the IKE peer
user-authentication Set the IKEv1 user authentication method
ASA5505(config-tunnel-ipsec)# ikev1 pre-shared-key ?
tunnel-group-ipsec mode commands/options:
0 Specifies an UNENCRYPTED password will follow
8 Specifies an ENCRYPTED password will follow
WORD < 129 char Enter an alphanumeric string between 1-128 characters
ASA5505(config-tunnel-ipsec)# ikev1 pre-shared-key cisco
Here are some helpful show and debug commands to troubleshoot IKEv1 IPsec site-to-site VPNs on an ASA and its equivalent commands on an IOS router:
ASA5505# show run crypto ikev1
crypto ikev1 enable outside
crypto ikev1 policy 1
authentication pre-share
encryption aes-256
hash sha
group 2
lifetime 86400
ASA5505# show run crypto ipsec
crypto ipsec ikev1 transform-set 5505_IKEv1_TSET esp-aes-256 esp-sha-hmac
ASA5505# show run crypto map
crypto map 5505_IKEv1_CMAP 1 match address 100
crypto map 5505_IKEv1_CMAP 1 set peer 192.168.1.1
crypto map 5505_IKEv1_CMAP 1 set ikev1 transform-set 5505_IKEv1_TSET
crypto map 5505_IKEv1_CMAP interface outside
ASA5505# show crypto isakmp sa
IKEv1 SAs:
Active SA: 1
Rekey SA: 0 (A tunnel will report 1 Active and 1 Rekey SA during rekey)
Total IKE SA: 1
1 IKE Peer: 192.168.1.1
Type : L2L Role : responder
Rekey : no State : MM_ACTIVE // QM_IDLE ON IOS ROUTER
There are no IKEv2 SAs
ASA5505# show crypto ipsec sa
interface: outside
Crypto map tag: 5505_IKEv1_CMAP, seq num: 1, local addr: 192.168.1.2
access-list 100 extended permit ip host 192.168.1.2 host 192.168.1.1
local ident (addr/mask/prot/port): (192.168.1.2/255.255.255.255/0/0)
remote ident (addr/mask/prot/port): (192.168.1.1/255.255.255.255/0/0)
current_peer: 192.168.1.1
#pkts encaps: 4, #pkts encrypt: 4, #pkts digest: 4
#pkts decaps: 4, #pkts decrypt: 4, #pkts verify: 4
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 4, #pkts comp failed: 0, #pkts decomp failed: 0
#pre-frag successes: 0, #pre-frag failures: 0, #fragments created: 0
#PMTUs sent: 0, #PMTUs rcvd: 0, #decapsulated frgs needing reassembly: 0
#TFC rcvd: 0, #TFC sent: 0
#Valid ICMP Errors rcvd: 0, #Invalid ICMP Errors rcvd: 0
#send errors: 0, #recv errors: 0
local crypto endpt.: 192.168.1.2/0, remote crypto endpt.: 192.168.1.1/0
path mtu 1500, ipsec overhead 74(44), media mtu 1500
PMTU time remaining (sec): 0, DF policy: copy-df
ICMP error validation: disabled, TFC packets: disabled
current outbound spi: A21332F0
current inbound spi : AF168576
inbound esp sas:
spi: 0xAF168576 (2937488758)
transform: esp-aes-256 esp-sha-hmac no compression
in use settings ={L2L, Tunnel, IKEv1, }
slot: 0, conn_id: 4096, crypto-map: 5505_IKEv1_CMAP
sa timing: remaining key lifetime (kB/sec): (4373999/3557)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x0000001F
outbound esp sas:
spi: 0xA21332F0 (2719167216)
transform: esp-aes-256 esp-sha-hmac no compression
in use settings ={L2L, Tunnel, IKEv1, }
slot: 0, conn_id: 4096, crypto-map: 5505_IKEv1_CMAP
sa timing: remaining key lifetime (kB/sec): (4373999/3557)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x00000001
871W#show crypto isakmp sa
IPv4 Crypto ISAKMP SA
dst src state conn-id slot status
192.168.1.2 192.168.1.1 QM_IDLE 2001 0 ACTIVE
IPv6 Crypto ISAKMP SA
871W#show crypto ipsec sa
interface: BVI1
Crypto map tag: 871_IKEv1_CMAP, local addr 192.168.1.1
protected vrf: (none)
local ident (addr/mask/prot/port): (192.168.1.1/255.255.255.255/0/0)
remote ident (addr/mask/prot/port): (192.168.1.2/255.255.255.255/0/0)
current_peer 192.168.1.2 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 4, #pkts encrypt: 4, #pkts digest: 4
#pkts decaps: 4, #pkts decrypt: 4, #pkts verify: 4
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 1, #recv errors 0
local crypto endpt.: 192.168.1.1, remote crypto endpt.: 192.168.1.2
path mtu 1500, ip mtu 1500, ip mtu idb BVI1
current outbound spi: 0xAF168576(2937488758)
inbound esp sas:
spi: 0xA21332F0(2719167216)
transform: esp-256-aes esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 1, flow_id: Motorola SEC 1.0:1, crypto map: 871_IKEv1_CMAP
sa timing: remaining key lifetime (k/sec): (4472107/3511)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0xAF168576(2937488758)
transform: esp-256-aes esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 2, flow_id: Motorola SEC 1.0:2, crypto map: 871_IKEv1_CMAP
sa timing: remaining key lifetime (k/sec): (4472107/3511)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE
outbound ah sas:
outbound pcp sas:
ASA5505# debug crypto ?
ca Set PKI debug levels
condition Set IPSec/ISAKMP debug filters
engine Set crypto engine debug levels
ike-common Set IKE common debug levels
ikev1 Set IKEV1 debug levels
ikev2 Set IKEV2 debug levels
ipsec Set IPSec debug levels
ss-api Set Crypto Secure Socket API debug levels
vpnclient Set EasyVPN client debug levels
ASA5505# debug crypto ikev1 ?
<1-255> Specify an optional debug level (default is 1)
timers debug the ikev1 timers
<cr>
ASA5505# debug crypto ikev1 255
ASA5505# Jul 27 15:47:06 [IKEv1 DEBUG]Group = 192.168.1.1, IP = 192.168.1.1, Sending keep-alive of type DPD R-U-THERE (seq number 0xfa85369)
Jul 27 15:47:06 [IKEv1 DEBUG]Group = 192.168.1.1, IP = 192.168.1.1, constructing blank hash payload
Jul 27 15:47:06 [IKEv1 DEBUG]Group = 192.168.1.1, IP = 192.168.1.1, constructing qm hash payload
Jul 27 15:47:06 [IKEv1]IP = 192.168.1.1, IKE_DECODE SENDING Message (msgid=c2227fd5) with payloads : HDR + HASH (8) + NOTIFY (11) + NONE (0) total length : 84
BEFORE ENCRYPTION
RAW PACKET DUMP on SEND
8e f0 e6 3e 21 0f 48 19 f9 0b 79 51 46 e5 b2 44 | ...>!.H...yQF..D
08 10 05 00 d5 7f 22 c2 1c 00 00 00 0b 00 00 18 | .....".........
0b 1c 28 95 78 17 70 07 09 7d 37 14 db 49 8c 48 | ..(.x.p..}7..I.H
ce 14 9a 4b 00 00 00 20 00 00 00 01 01 10 8d 28 | ...K... .......(
8e f0 e6 3e 21 0f 48 19 f9 0b 79 51 46 e5 b2 44 | ...>!.H...yQF..D
0f a8 53 69 | ..Si
ISAKMP Header
Initiator COOKIE: 8e f0 e6 3e 21 0f 48 19
Responder COOKIE: f9 0b 79 51 46 e5 b2 44
Next Payload: Hash
Version: 1.0
Exchange Type: Informational
Flags: (none)
MessageID: D57F22C2
Length: 469762048
Payload Hash
Next Payload: Notification
Reserved: 00
Payload Length: 24
Data:
0b 1c 28 95 78 17 70 07 09 7d 37 14 db 49 8c 48
ce 14 9a 4b
Payload Notification
Next Payload: None
Reserved: 00
Payload Length: 32
DOI: IPsec
Protocol-ID: PROTO_ISAKMP
Spi Size: 16
Notify Type: R_U_THERE
SPI:
8e f0 e6 3e 21 0f 48 19 f9 0b 79 51 46 e5 b2 44
Data: 0f a8 53 69
ISAKMP Header
Initiator COOKIE: 8e f0 e6 3e 21 0f 48 19
Responder COOKIE: f9 0b 79 51 46 e5 b2 44
Next Payload: Hash
Version: 1.0
Exchange Type: Informational
Flags: (Encryption)
MessageID: C2227FD5
Length: 92
IKE Recv RAW packet dump
8e f0 e6 3e 21 0f 48 19 f9 0b 79 51 46 e5 b2 44 | ...>!.H...yQF..D
08 10 05 01 1f 35 1f 3c 00 00 00 5c 00 4d bb 90 | .....5.<...\.M..
f3 85 9b 86 93 bb ab 22 d6 23 ef 7e e2 ad 16 65 | .......".#.~...e
62 1d 69 00 82 5c 34 86 74 fb c9 3a 6b 49 ab 08 | b.i..\4.t..:kI..
2c ff 94 d2 83 bb d4 1a 0c e7 53 29 ea b4 80 95 | ,.........S)....
13 31 8c 09 39 12 1a a4 76 bc d4 dd | .1..9...v...
RECV PACKET from 192.168.1.1
ISAKMP Header
Initiator COOKIE: 8e f0 e6 3e 21 0f 48 19
Responder COOKIE: f9 0b 79 51 46 e5 b2 44
Next Payload: Hash
Version: 1.0
Exchange Type: Informational
Flags: (Encryption)
MessageID: 1F351F3C
Length: 92
AFTER DECRYPTION
ISAKMP Header
Initiator COOKIE: 8e f0 e6 3e 21 0f 48 19
Responder COOKIE: f9 0b 79 51 46 e5 b2 44
Next Payload: Hash
Version: 1.0
Exchange Type: Informational
Flags: (Encryption)
MessageID: 1F351F3C
Length: 92
Payload Hash
Next Payload: Notification
Reserved: 00
Payload Length: 24
Data:
88 af 61 fc 7e ee 2c 17 b5 85 99 47 2a e5 96 e4
3d ce a7 94
Payload Notification
Next Payload: None
Reserved: 00
Payload Length: 32
DOI: IPsec
Protocol-ID: PROTO_ISAKMP
Spi Size: 16
Notify Type: R_U_THERE_ACK
SPI:
8e f0 e6 3e 21 0f 48 19 f9 0b 79 51 46 e5 b2 44
Data: 0f a8 53 69
Jul 27 15:47:06 [IKEv1]IP = 192.168.1.1, IKE_DECODE RECEIVED Message (msgid=1f351f3c) with payloads : HDR + HASH (8) + NOTIFY (11) + NONE (0) total length : 84
Jul 27 15:47:06 [IKEv1 DEBUG]Group = 192.168.1.1, IP = 192.168.1.1, processing hash payload
Jul 27 15:47:06 [IKEv1 DEBUG]Group = 192.168.1.1, IP = 192.168.1.1, processing notify payload
Jul 27 15:47:06 [IKEv1 DEBUG]Group = 192.168.1.1, IP = 192.168.1.1, Received keep-alive of type DPD R-U-THERE-ACK (seq number 0xfa85369)
Jul 27 15:47:16 [IKEv1 DEBUG]Group = 192.168.1.1, IP = 192.168.1.1, Sending keep-alive of type DPD R-U-THERE (seq number 0xfa8536a)
Jul 27 15:47:16 [IKEv1 DEBUG]Group = 192.168.1.1, IP = 192.168.1.1, constructing blank hash payload
Jul 27 15:47:16 [IKEv1 DEBUG]Group = 192.168.1.1, IP = 192.168.1.1, constructing qm hash payload
Jul 27 15:47:16 [IKEv1]IP = 192.168.1.1, IKE_DECODE SENDING Message (msgid=86feac10) with payloads : HDR + HASH (8) + NOTIFY (11) + NONE (0) total length : 84
BEFORE ENCRYPTION
RAW PACKET DUMP on SEND
8e f0 e6 3e 21 0f 48 19 f9 0b 79 51 46 e5 b2 44 | ...>!.H...yQF..D
08 10 05 00 10 ac fe 86 1c 00 00 00 0b 00 00 18 | ................
e9 ee f3 46 cb a6 4b 95 0d f0 c7 83 48 a5 75 50 | ...F..K.....H.uP
a0 49 b4 d9 00 00 00 20 00 00 00 01 01 10 8d 28 | .I..... .......(
8e f0 e6 3e 21 0f 48 19 f9 0b 79 51 46 e5 b2 44 | ...>!.H...yQF..D
0f a8 53 6a | ..Sj
ISAKMP Header
Initiator COOKIE: 8e f0 e6 3e 21 0f 48 19
Responder COOKIE: f9 0b 79 51 46 e5 b2 44
Next Payload: Hash
Version: 1.0
Exchange Type: Informational
Flags: (none)
MessageID: 10ACFE86
Length: 469762048
Payload Hash
Next Payload: Notification
Reserved: 00
Payload Length: 24
Data:
e9 ee f3 46 cb a6 4b 95 0d f0 c7 83 48 a5 75 50
a0 49 b4 d9
Payload Notification
Next Payload: None
Reserved: 00
Payload Length: 32
DOI: IPsec
Protocol-ID: PROTO_ISAKMP
Spi Size: 16
Notify Type: R_U_THERE
SPI:
8e f0 e6 3e 21 0f 48 19 f9 0b 79 51 46 e5 b2 44
Data: 0f a8 53 6a
ISAKMP Header
Initiator COOKIE: 8e f0 e6 3e 21 0f 48 19
Responder COOKIE: f9 0b 79 51 46 e5 b2 44
Next Payload: Hash
Version: 1.0
Exchange Type: Informational
Flags: (Encryption)
MessageID: 86FEAC10
Length: 92
IKE Recv RAW packet dump
8e f0 e6 3e 21 0f 48 19 f9 0b 79 51 46 e5 b2 44 | ...>!.H...yQF..D
08 10 05 01 9c c2 18 86 00 00 00 5c e2 d6 cb 79 | ...........\...y
77 f5 33 51 aa 10 b5 7f 7c 9c 08 da e2 7a 18 d7 | w.3Q...|....z..
93 8f ff 73 bf ce 66 40 8c 81 28 ec 50 ad 58 af | ...s..f@..(.P.X.
8c 64 42 b1 88 ea 12 2b 50 ce cf c8 d7 4e 5c 6e | .dB....+P....N\n
e0 48 b8 b9 a5 d6 f2 b8 c7 d8 1e 16 | .H..........
RECV PACKET from 192.168.1.1
ISAKMP Header
Initiator COOKIE: 8e f0 e6 3e 21 0f 48 19
Responder COOKIE: f9 0b 79 51 46 e5 b2 44
Next Payload: Hash
Version: 1.0
Exchange Type: Informational
Flags: (Encryption)
MessageID: 9CC21886
Length: 92
AFTER DECRYPTION
ISAKMP Header
Initiator COOKIE: 8e f0 e6 3e 21 0f 48 19
Responder COOKIE: f9 0b 79 51 46 e5 b2 44
Next Payload: Hash
Version: 1.0
Exchange Type: Informational
Flags: (Encryption)
MessageID: 9CC21886
Length: 92
Payload Hash
Next Payload: Notification
Reserved: 00
Payload Length: 24
Data:
9e 3b ae fa 17 d3 f0 0d a3 80 7a 6f 04 13 e0 b8
d4 00 6e ba
Payload Notification
Next Payload: None
Reserved: 00
Payload Length: 32
DOI: IPsec
Protocol-ID: PROTO_ISAKMP
Spi Size: 16
Notify Type: R_U_THERE_ACK
SPI:
8e f0 e6 3e 21 0f 48 19 f9 0b 79 51 46 e5 b2 44
Data: 0f a8 53 6a
Jul 27 15:47:16 [IKEv1]IP = 192.168.1.1, IKE_DECODE RECEIVED Message (msgid=9cc21886) with payloads : HDR + HASH (8) + NOTIFY (11) + NONE (0) total length : 84
Jul 27 15:47:16 [IKEv1 DEBUG]Group = 192.168.1.1, IP = 192.168.1.1, processing hash payload
Jul 27 15:47:16 [IKEv1 DEBUG]Group = 192.168.1.1, IP = 192.168.1.1, processing notify payload
Jul 27 15:47:16 [IKEv1 DEBUG]Group = 192.168.1.1, IP = 192.168.1.1, Received keep-alive of type DPD R-U-THERE-ACK (seq number 0xfa8536a)
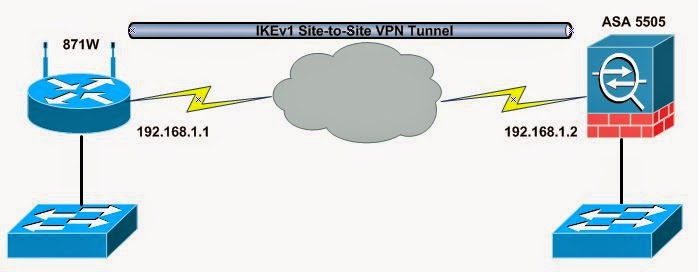
No comments:
Post a Comment