Task 1:
Configure Traffic Telemetry Methods on Cisco IOS Software
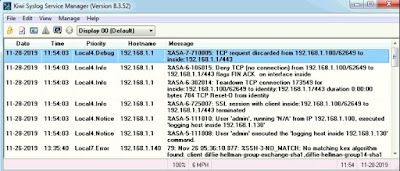
Add a device in Kiwi Syslog under File > Setup.
Download and run Colasoft Capsaoft NetFlowAnalyzer (free version) in Win7 machine (192.168.1.130).
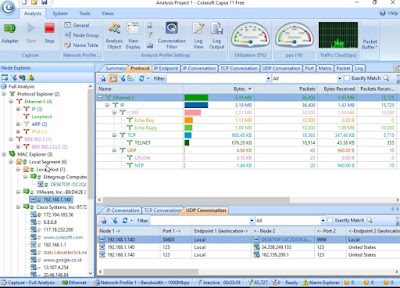
Expand Full Analysis > Protocol Explorer > MAC Explorer > IP Explorer.
Go to Protocol tab > IP Conversation (at the bottom).
Go to IP Endpoint tab > IP Conversation.
Go to IP Endpoint tab > TCP Conversation.
Go to IP Endpoint tab > UDP Conversation.
Go to IP Conversation tab > TCP Conversation.
Go to IP Conversation tab > UDP Conversation.
Go to TCP Conversation > Packets.
Go to Matrix tab > select various Top 100 graphs on the left.
Go to Packet tab. You can view real-time packet capture.
Go to Log tab. Select various Log on the left.
Configure a public NTP server sg.pool.ntp.org (162.159.200.123) under Configuration > Device Setup > System Time > NTP > Add.
Click Apply > Send.
Configure a remote Syslog Server under Configuration > Device Management > Logging > Syslog Servers > Add.
Select Interface: inside > type IP Address: 192.168.1.130 > leave the default Protocol: UDP and Port: 514 > click OK.
Configure Logging Filters on the ASA under Configuration > Device Management > Logging > Logging Filters.
Click Apply > Send.
Select Global - applies to all interfaces (default) > Next.
Select Create a new traffic class > type a name: ALL-TRAFFIC-NETFLOW > select Any traffic > click Next.
Enable Send for Collector: 192.168.1.100 > click OK.
Click Finish.
Configure
Timezone and NTP on IOS Router.
CSRv#show
clock
.01:59:59.016
UTC Tue Nov 26 2019
CSRv#configure
terminal
Enter
configuration commands, one per line.
End with CNTL/Z.
CSRv(config)#clock
timezone ?
WORD
name of time zone
CSRv(config)#clock
timezone SGT ?
<-23 - 23> Hours offset from UTC
CSRv(config)#clock
timezone SGT +8
CSRv(config)#ntp
?
access-group Control NTP access
allow Allow processing of packets
authenticate Authenticate time sources
authentication-key Authentication key for trusted time sources
broadcastdelay Estimated round-trip delay
clock-period Length of hardware clock tick
leap-handle To handle the leap seconds
logging Enable NTP message logging
master Act as NTP master clock
max-associations Set maximum number of associations
maxdistance Maximum Distance for synchronization
mindistance Minimum distance to consider for
clockhop
orphan Threshold Stratum for orphan mode
panic Reject time updates > panic
threshold (default 1000Sec)
passive NTP passive mode
peer Configure NTP peer
server Configure NTP server
source Configure interface for source
address
trusted-key Key numbers for trusted time sources
CSRv(config)#ntp
server ?
A.B.C.D
IP address of peer
WORD
Hostname of peer
X:X:X:X::X
IPv6 address of peer
ip
Use IP for DNS resolution
ipv6
Use IPv6 for DNS resolution
vrf
VPN Routing/Forwarding Information
CSRv(config)#ntp
server 162.159.200.1
Notice
the Stratum (st) is 3.
CSRv#show
ntp ?
associations
NTP associations
config
NTP server/peer configs
information
NTP Information
packets
NTP Packet statistics
status
NTP status
CSRv#show
ntp associations
address ref clock st
when poll reach delay
offset disp
*~162.159.200.1
10.35.8.220 3 17
64 3 4.958 122.502 64.168
~34.208.249.133 185.198.26.172 3
8 64 1 207.95
3.648 3939.1
* sys.peer, # selected, + candidate, -
outlyer, x falseticker, ~ configured
CSRv#show
clock
10:06:02.329
SGT Tue Nov 26 2019
CSRv#show
ntp associations detail
162.159.200.1 configured, ipv4, our_master, sane,
valid, stratum 3
ref ID
10.35.8.220 , time E1870784.42F966EF
(10:08:04.261 SGT Tue Nov 26 2019)
our mode
client, peer mode server, our poll intvl 64, peer poll intvl 64
root
delay 47.91 msec, root disp 0.50, reach 37, sync dist 337.06
delay
4.95 msec, offset 122.5023 msec, dispersion 4.45, jitter 305.03 msec
precision
2**25, version 4
assoc id
37157, assoc name 162.159.200.1
assoc in
packets 10, assoc out packets 10, assoc error packets 0
org time
00000000.00000000 (08:00:00.000 SGT Mon Jan 1 1900)
rec time
E18707B9.C9D12A48 (10:08:57.788 SGT Tue Nov 26 2019)
xmt time
E18707B9.C9D12A48 (10:08:57.788 SGT Tue Nov 26 2019)
filtdelay
= 7.94 5.96
5.96 5.90 5.96
6.95 4.95 5.97
filtoffset
= 713.29
565.80 415.93 262.40
131.09 126.46 122.50
117.90
filterror
= 0.97 1.96
2.97 4.00 4.89
4.92 4.95 4.98
minpoll =
6, maxpoll = 10
34.208.249.133
configured, ipv4, insane, invalid, stratum 3
ref ID
185.198.26.172 , time E1870173.AC385C83 (09:42:11.672 SGT Tue Nov 26 2019)
our mode
client, peer mode server, our poll intvl 64, peer poll intvl 64
root
delay 25.72 msec, root disp 40.78, reach 1, sync dist 1030.81
delay
206.93 msec, offset 697.8032 msec, dispersion 439.69, jitter 433.26 msec
precision
2**20, version 4
assoc id
37156, assoc name 34.208.249.133
assoc in
packets 3093, assoc out packets 3094, assoc error packets 0
org time
00000000.00000000 (08:00:00.000 SGT Mon Jan 1 1900)
rec time
E18707B2.DF6E3407 (10:08:50.872 SGT Tue Nov 26 2019)
xmt time
E18707B2.DF6E3407 (10:08:50.872 SGT Tue Nov 26 2019)
filtdelay
= 206.93 207.96
207.92 207.96 207.95
0.00 0.00 0.00
filtoffset
= 697.80
557.71 419.95 282.83
3.64 0.00 0.00
0.00
filterror
= 0.98 1.91
2.84 3.77 5.61 16000.0 16000.0 16000.0
minpoll =
6, maxpoll = 10
Configure
local and remote logging (syslog) on the IOS Router.
CSRv(config)#logging
?
Hostname or A.B.C.D IP address of the logging host
alarm Configure syslog for alarms
buffered Set buffered logging parameters
buginf Enable buginf logging for
debugging
cns-events Set CNS Event logging level
console Set console logging parameters
count Count every log message and
timestamp last occurance
delimiter Append delimiter to syslog messages
discriminator Create or modify a message
discriminator
dmvpn DMVPN Configuration
esm Set ESM filter restrictions
exception Limit size of exception flush
output
facility Facility parameter for syslog
messages
filter Specify logging filter
history Configure syslog history table
host Set syslog server IP address
and parameters
message-counter Configure log message to include certain
counter value
monitor Set terminal line (monitor)
logging parameters
on Enable logging to all
enabled destinations
origin-id Add origin ID to syslog messages
persistent Set persistent logging parameters
queue-limit Set logger message queue size
rate-limit Set messages per second limit
reload Set reload logging level
server-arp Enable sending ARP requests for
syslog servers when first configured
snmp-trap Set syslog level for sending snmp
trap
source-interface Specify interface for source address in
logging transactions
trap Set syslog server logging
level
userinfo Enable logging of user info on
privileged mode enabling
CSRv(config)#logging
on
CSRv(config)#logging
buffered ?
<0-7> Logging severity level
<4096-2147483647> Logging buffer size
alerts Immediate action needed (severity=1)
critical Critical conditions (severity=2)
debugging Debugging messages (severity=7)
discriminator Establish MD-Buffer association
emergencies System is unusable (severity=0)
errors Error conditions (severity=3)
filtered Enable filtered logging
informational Informational messages (severity=6)
notifications Normal but significant conditions
(severity=5)
warnings Warning conditions (severity=4)
xml Enable logging in XML to XML
logging buffer
<cr>
CSRv(config)#logging
buffered debugging
CSRv(config)#logging
host ?
Hostname or A.B.C.D IP address of the syslog server
ipv6 Configure IPv6 syslog server
CSRv(config)#logging
host 192.168.1.130
Download
and run Kiwi Syslog Server (free version) in Win7 machine (192.168.1.130).
Add a device in Kiwi Syslog under File > Setup.
I generated syslogs on the CSRv by bouncing an interface.
CSRv(config)#do
show ip interface brief
Interface IP-Address OK? Method Status Protocol
GigabitEthernet1 192.168.1.140 YES NVRAM
up up
GigabitEthernet2 unassigned YES NVRAM
administratively down down
CSRv(config)#interface
g2
CSRv(config-if)#no
shutdown
CSRv(config-if)#do
terminal monitor
CSRv(config-if)#
CSRv(config-if)#shutdown
CSRv(config-if)#end
CSRv#
Nov 26 02:25:16.874: %LINK-5-CHANGED: Interface
GigabitEthernet2, changed state to administratively down
CSRv#
Nov 26 02:25:17.910: %SYS-5-CONFIG_I: Configured
from console by admin on vty0 (192.168.1.100)
Issue a
show logging on CSRv to verify Syslog setup.
CSRv#show
logging
Syslog logging: enabled (0 messages dropped,
2 messages rate-limited, 0 flushes, 0 overruns, xml disabled, filtering
disabled)
No Active
Message Discriminator.
No
Inactive Message Discriminator.
Console logging: level debugging, 104
messages logged, xml disabled,
filtering disabled
Monitor logging: level debugging, 34
messages logged, xml disabled,
filtering disabled
Logging to: vty1(2)
Buffer
logging: level debugging, 105 messages
logged, xml disabled,
filtering disabled
Exception Logging: size (4096 bytes)
Count and timestamp logging messages:
disabled
Persistent logging: disabled
No active
filter modules.
Trap
logging: level informational, 73 message lines logged
Logging to 192.168.1.130 (udp
port 514, audit disabled,
link up),
3 message lines logged,
0 message lines rate-limited,
0 message lines dropped-by-MD,
xml disabled, sequence number
disabled
filtering disabled
Logging Source-Interface: VRF Name:
Log
Buffer (4096 bytes):
55.489:
AAA/AUTHEN/LOGIN (00000FC3): Pick method list 'ACCESS-1'
.Nov 24
12:10:03.028: AAA: parse name=tty3 idb type=-1 tty=-1
.Nov 24
12:10:03.028: AAA: name=tty3 flags=0x11 type=5 shelf=0 slot=0 adapter=0 port=3
channel=0
.Nov 24
12:10:03.028: AAA/MEMORY: create_user (0x7FD2F9B9DDE0) user='john-ise'
ruser='NULL' ds0=0 port='tty3' rem_addr='192.168.1.100' authen_type=ASCII
service=ENABLE priv=15 initial_task_id='0', vrf= (id=0)
.Nov 24
12:10:03.029: AAA/AUTHEN/START (1022751880): port='tty3' list='ACCESS-1'
action=LOGIN service=ENABLE
.Nov 24
12:10:03.029: AAA/AUTHEN/START (1022751880): using "default" list
.Nov 24
12:10:03.029: AAA/AUTHEN/START (1022751880): Unknown type for server group
"ACCESS-1". Skip it
.Nov 24
12:10:03.029: AAA/AUTHEN (1022751880): status = UNKNOWN
.Nov 24
12:10:03.029: AAA/AUTHEN/START (1022751880): Method=ENABLE
.Nov 24
12:10:03.030: AAA/AUTHEN (1022751880): status = GETPASS
.Nov 24
12:10:05.889: AAA/AUTHEN/CONT (1022751880): continue_login (user='(undef)')
.Nov 24
12:10:05.889: AAA/AUTHEN (1022751880): status = GETPASS
.Nov 24
12:10:05.890: AAA/AUTHEN/CONT (1022751880): Method=ENABLE
.Nov 24
12:10:05.890: AAA/AUTHEN(1022751880): password incorrect
.Nov 24
12:10:05.890: AAA/AUTHEN (1022751880): status = FAIL
.Nov 24
12:10:05.890: AAA/MEMORY: free_user (0x7FD2F9B9DDE0) user='NULL' ruser='NULL'
port='tty3' rem_addr='192.168.1.100' authen_type=ASCII service=ENABLE priv=15
vrf= (id=0)
.Nov 24
12:12:09.670: AAA: parse name=tty3 idb type=-1 tty=-1
.Nov 24
12:12:09.670: AAA: name=tty3 flags=0x11 type=5 shelf=0 slot=0 adapter=0 port=3
channel=0
.Nov 24
12:12:09.670: AAA/MEMORY: create_user (0x7FD35F807A70) user='john-ise'
ruser='NULL' ds0=0 port='tty3' rem_addr='192.168.1.100' authen_type=ASCII
service=ENABLE priv=15 initial_task_id='0', vrf= (id=0)
.Nov 24
12:12:09.670: AAA/AUTHEN/START (1262379625): port='tty3' list='ACCESS-1'
action=LOGIN service=ENABLE
.Nov 24
12:12:09.671: AAA/AUTHEN/START (1262379625): using "default" list
.Nov 24
12:12:09.671: AAA/AUTHEN/START (1262379625): Unknown type for server group
"ACCESS-1". Skip it
.Nov 24
12:12:09.671: AAA/AUTHEN (1262379625): status = UNKNOWN
.Nov 24
12:12:09.671: AAA/AUTHEN/START (1262379625): Method=ENABLE
.Nov 24
12:12:09.671: AAA/AUTHEN (1262379625): status = GETPASS
.Nov 24
12:12:12.258: AAA/AUTHEN/CONT (1262379625): continue_login (user='(undef)')
.Nov 24
12:12:12.258: AAA/AUTHEN (1262379625): status = GETPASS
.Nov 24
12:12:12.259: AAA/AUTHEN/CONT (1262379625): Method=ENABLE
.Nov 24
12:12:12.259: AAA/AUTHEN(1262379625): password incorrect
.Nov 24
12:12:12.259: AAA/AUTHEN (1262379625): status = FAIL
.Nov 24
12:12:12.259: AAA/MEMORY: free_user (0x7FD35F807A70) user='NULL' ruser='NULL'
port='tty3' rem_addr='192.168.1.100' authen_type=ASCII service=ENABLE priv=15
vrf= (id=0)
.Nov 24
12:25:08.532: %SYS-5-CONFIG_I: Configured from console by john-ise on vty0
(192.168.1.100)
.Nov 24
12:36:59.735: %SYS-5-CONFIG_I: Configured from console by john-ise on vty0
(192.168.1.100)
.Nov 24
12:37:11.693: %SYS-5-CONFIG_I: Configured from console by john-ise on vty0
(192.168.1.100)
.Nov 26
01:46:34.940: %SYS-5-CONFIG_I: Configured from console by admin on vty0
(192.168.1.100)
.Nov 26
01:58:43.282: %SYS-5-CONFIG_I: Configured from console by admin on vty0
(192.168.1.100)
.Nov 26
01:58:56.796: %SYS-5-CONFIG_I: Configured from console by admin on vty0
(192.168.1.100)
.Nov 26
02:00:47.653: %SYS-6-CLOCKUPDATE: System clock has been updated from 02:00:47
UTC Tue Nov 26 2019 to 10:00:47 SGT Tue Nov 26 2019, configured from console by
admin on vty0 (192.168.1.100).
Nov 26
02:05:44.684: %SYS-5-CONFIG_I: Configured from console by admin on vty0
(192.168.1.100)
Nov 26 02:11:59.785: %SYS-6-LOGGINGHOST_STARTSTOP:
Logging to host 192.168.1.130 port 0 CLI Request Triggered
Nov 26 02:12:00.786: %SYS-6-LOGGINGHOST_STARTSTOP:
Logging to host 192.168.1.130 port 514 started - CLI initiated
Nov 26 02:25:16.874: %LINK-5-CHANGED: Interface
GigabitEthernet2, changed state to administratively down
Nov 26 02:25:17.910: %SYS-5-CONFIG_I: Configured
from console by admin on vty0 (192.168.1.100)
Download and run Colasoft Capsaoft NetFlowAnalyzer (free version) in Win7 machine (192.168.1.130).
Configure
NetFlow v9 Exporter.
CSRv(config)#flow
?
exporter
Define a Flow Exporter
monitor
Define a Flow Monitor
record
Define a Flow Record
CSRv(config)#flow
exporter ?
WORD
Flow Exporter name
CSRv(config)#flow
exporter EXP-1
CSRv(config-flow-exporter)#?
default Set a command to its defaults
description Provide a description for this Flow
Exporter
destination Export destination configuration
dscp Optional DSCP
exit Exit from Flow Exporter
configuration mode
export-protocol Export protocol version
mtu Optional MTU
no Negate a command or set its
defaults
option Select an option for exporting
source Originating interface
template Flow Exporter template configuration
transport Transport protocol
ttl Optional TTL or hop limit
CSRv(config-flow-exporter)#destination
?
Hostname or A.B.C.D Destination IPv4 address or hostname
Hostname or X:X:X:X::X Destination IPv6 address or hostname
CSRv(config-flow-exporter)#destination
192.168.1.100
CSRv(config-flow-exporter)#transport
?
udp
UDP transport protocol
CSRv(config-flow-exporter)#transport
udp 9996
CSRv(config-flow-exporter)#export-protocol
?
ipfix
IPFIX (Version 10)
netflow-v5
NetFlow Version 5
netflow-v9
NetFlow Version 9
CSRv(config-flow-exporter)#export-protocol
netflow-v9
Configure
NetFlow v9 Monitor
CSRv(config)#flow
monitor MON-1
CSRv(config-flow-monitor)#?
cache
Configure Flow Cache parameters
default
Set a command to its defaults
description
Provide a description for this Flow Monitor
exit
Exit from Flow Monitor configuration mode
exporter
Add an Exporter to use to export records
no
Negate a command or set its defaults
record
Specify Flow Record to use to define Cache
statistics
Collect statistics
CSRv(config-flow-monitor)#exporter
?
EXP-1
User defined
CSRv(config-flow-monitor)#exporter
EXP-1
CSRv(config-flow-monitor)#record
?
netflow Traditional NetFlow collection
schemes
netflow-original Traditional IPv4 input NetFlow with origin
ASs
CSRv(config-flow-monitor)#record
netflow ?
ipv4
Traditional IPv4 NetFlow collection schemes
ipv6
Traditional IPv6 NetFlow collection schemes
CSRv(config-flow-monitor)#record
netflow ipv4 ?
as AS aggregation schemes
as-tos AS and TOS aggregation
schemes
bgp-nexthop-tos BGP next-hop and TOS aggregation
schemes
destination-prefix Destination Prefix aggregation schemes
destination-prefix-tos Destination Prefix and TOS aggregation
schemes
original-input Traditional IPv4 input NetFlow with
ASs
original-output Traditional IPv4 output NetFlow with
ASs
prefix Source and Destination
Prefixes aggregation schemes
prefix-port Prefixes and Ports aggregation
scheme
prefix-tos Prefixes and TOS aggregation
schemes
protocol-port Protocol and Ports aggregation
scheme
protocol-port-tos Protocol, Ports and TOS aggregation
scheme
source-prefix Source AS and Prefix aggregation
schemes
source-prefix-tos Source Prefix and TOS aggregation
schemes
CSRv(config-flow-monitor)#record
netflow ipv4 original-output
Apply
NetFlow v9 on CSRv interface.
CSRv(config)#interface
g1
CSRv(config-if)#ip
flow ?
monitor
Apply a Flow Monitor
CSRv(config-if)#ip
flow monitor ?
MON-1
User defined
CSRv(config-if)#ip
flow monitor MON-1 ?
input
Apply Flow Monitor on input traffic
multicast
Apply Flow Monitor on multicast traffic
output
Apply Flow Monitor on output traffic
sampler
Optional Sampler to apply to this Flow Monitor
unicast
Apply Flow Monitor on unicast traffic
CSRv(config-if)#ip
flow monitor MON-1 output
I configured NAT on CSRv and generated some traffic.
CSRv#ping
8.8.8.8 source 10.1.1.1
Type
escape sequence to abort.
Sending
5, 100-byte ICMP Echos to 8.8.8.8, timeout is 2 seconds:
Packet
sent with a source address of 10.1.1.1
.....
Success
rate is 0 percent (0/5)
CSRv#configure terminal
Enter
configuration commands, one per line.
End with CNTL/Z.
CSRv(config)#interface
g1
CSRv(config-if)#ip
nat outside
CSRv(config-if)#interface
loopback1
CSRv(config-if)#ip
nat inside
CSRv(config-if)#access-list
10 permit 10.1.1.0 0.0.0.255
CSRv(config)#ip
nat inside source list 10 interface g1 overload
CSRv#ping
8.8.8.8 source 10.1.1.1
Type
escape sequence to abort.
Sending
5, 100-byte ICMP Echos to 8.8.8.8, timeout is 2 seconds:
Packet
sent with a source address of 10.1.1.1
!!!!!
Success
rate is 100 percent (5/5), round-trip min/avg/max = 8/14/27 ms
CSRv#telnet
192.168.1.3
Trying
192.168.1.3 ... Open
### C3560
SENSS LAB ###
User
Access Verification
Password:
SW1>enable
Password:
SW1#
CSRv#telnet
192.168.1.1
Trying
192.168.1.1 ... Open
### ASA
SENSS LAB ###
User
Access Verification
Password:
User
enable_1 logged in to LAB-ASA5515x
Logins
over the last 37 days: 9. Last login:
05:29:18 UTC Nov 25 2019 from 192.168.1.100
Failed
logins since the last login: 0.
Type help
or '?' for a list of available commands.
LAB-ASA5515x>
enable
Password:
*****
LAB-ASA5515x#
CSRv#ssh
-l root 192.168.1.110
Password:
Linux
kali 5.2.0-kali2-amd64 #1 SMP Debian 5.2.9-2kali1 (2019-08-22) x86_64
The
programs included with the Kali GNU/Linux system are free software;
the exact
distribution terms for each program are described in the
individual
files in /usr/share/doc/*/copyright.
Kali
GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted
by applicable law.
Last
login: Tue Nov 26 00:41:21 2019 from 192.168.1.100
root@kali:~#
In
Colasoft Capsa, select the LAN adapter: Ethernet > select Full Analysis
(default) > click Start.
Expand Full Analysis > Protocol Explorer > MAC Explorer > IP Explorer.
Go to
Summary tab.
Notice
the VMware host CSRv 192.168.140.
Go to Protocol tab > IP Conversation (at the bottom).
Go to
Protocol tab > TCP Conversation.
Notice
the Telnet TCP 23 session from CSRv (192.168.1.140) to SW1 (192.168.1.3).
Go to
Protocol tab > UDP Conversation.
Notice
the NetFlow UDP 9996 session from CSRv (192.168.1.140) to Win10 PC (Local) and
NTP UDP 123 session to NTP server sg.pool.ntp.org (162.159.200.1).
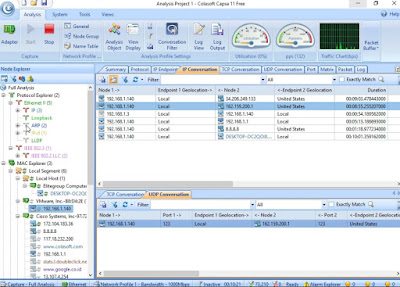
Go to IP Endpoint tab > IP Conversation.
Go to IP Endpoint tab > TCP Conversation.
Go to IP Endpoint tab > UDP Conversation.
Go to IP Conversation tab > TCP Conversation.
Go to IP Conversation tab > UDP Conversation.
Go to TCP Conversation > Packets.
Go to TCP
Conversation > select a TCP session > Data Flow.
Notice
CSRv (192.168.1.140) high number dynamic source port 35332 > destination TCP
port 23 (Telnet) to SW1 (192.168.1.3.).
Go to UDP
Conversation > select a session/flow > Packets.
Notice
the raw Packet Info capture at the bottom.
Click the
right arrow to view more tabs (click left to go to previous tabs).
Go to
Port tab. Notice the top talker ports: HTTP TCP 80, HTTPS/SSL TCP 443 and
Telnet TCP 23.
Go to Matrix tab > select various Top 100 graphs on the left.
Go to Packet tab. You can view real-time packet capture.
Go to Log tab. Select various Log on the left.
To verify
NetFlow export statistics, issue a show flow exporter statistics command.
CSRv#show
flow exporter statistics
Flow
Exporter EXP-1:
Packet send statistics (last cleared 01:00:32
ago):
Successfully sent:
298 (19128
bytes)
Client send statistics:
Client: Flow Monitor MON-1
Records added: 339
- sent: 339
Bytes added: 16950
- sent: 16950
To view
view NetFlow monitor (MON-1) cache, issue a show
flow monitor <MONITOR-NAME> cache format table command.
CSRv#show
flow monitor ?
MON-1
User defined
broker
Show the flow monitor broker
name
Name a specific Flow Monitor
type
Type of the Flow Monitor
|
Output modifiers
<cr>
CSRv#show
flow monitor MON-1 ?
cache
Flow monitor cache contents
statistics
Flow monitor statistics
|
Output modifiers
<cr>
CSRv#show
flow monitor MON-1 cache ?
filter
Display only matching flow records
format
Specify cache display format
sort
Sort the resulting flow records
|
Output modifiers
<cr>
CSRv#show
flow monitor MON-1 cache format ?
csv
Flow monitor cache contents in csv format
record
Flow monitor cache contents in record format
table
Flow monitor cache contents in table format
CSRv#show
flow monitor MON-1 cache format table
Cache type: Normal (Platform
cache)
Cache size: 200000
Current entries: 5
High Watermark: 9
Flows added: 377
Flows aged: 372
- Inactive timeout (
15 secs) 372
IPV4 SRC
ADDR IPV4 DST ADDR TRNS SRC PORT TRNS DST PORT
INTF OUTPUT FLOW SAMPLER
ID IP TOS IP PROT
ip src as ip dst as ipv4 next hop addr ipv4 src mask
ipv4 dst mask tcp flags intf input bytes pkts
time first time last
=============== =============== =============
=============
====================
=============== ====== =======
========= ========= ================== =============
============= ========= ==================== ==========
========== ============ ============
192.168.1.140 192.168.1.100 23 60689
Gi1
0 0xC0 6 0 0
192.168.1.100
/32 /24 0x18
Null
1423 30 14:31:20.706
14:31:35.110
192.168.1.140 192.168.1.100 23 60688
Gi1
0 0xC0 6 0 0
192.168.1.100
/32 /24 0x18
Null
9940 93 14:31:03.090
14:31:25.622
192.168.1.140 192.168.1.1 53251 23
Gi1
0 0xC0 6 0 0
192.168.1.1
/32 /24 0x1A
Null
2528 61 14:31:09.032
14:31:25.818
192.168.1.140 192.168.1.3 50180 23
Gi1
0 0xC0 6 0 0
192.168.1.3
/32 /24 0x1A
Null
1152 27 14:31:31.732
14:31:35.310
192.168.1.140 192.168.1.100 50605 9996
Gi1
0 0x00 17 0 0
192.168.1.100
/32 /24 0x00
Null
412 3 14:31:11.556
14:31:26.574
192.168.1.140 192.168.1.100 23 60604
Gi1
0 0xC0 6 0 0
192.168.1.100
/32 /24 0x18
Null
675 6 14:31:40.016
14:31:41.398
Task 2:
Configure Traffic Telemetry Methods on Cisco ASA
Configure
ASA Time Zone via ASDM under Configuration > Device Setup > System Time
> Clock > Time Zone: (GMT +08:00) Singapore.
Configure a public NTP server sg.pool.ntp.org (162.159.200.123) under Configuration > Device Setup > System Time > NTP > Add.
Click Apply > Send.
LAB-ASA5515x#
show ntp ?
associations
NTP associations
status
NTP status
LAB-ASA5515x#
show ntp associations
address ref clock st
when poll reach delay
offset disp
~162.159.200.123 10.35.8.220 3
45 64 0
4.6 -39655 16000.
* master (synced), # master (unsynced), +
selected, - candidate, ~ configured
LAB-ASA5515x#
show ntp status
Clock is unsynchronized, stratum 16, no reference
clock
nominal
freq is 99.9984 Hz, actual freq is 99.9984 Hz, precision is 2**6
reference
time is e189bbab.dc87df4c (11:21:15.861 SGT Thu Nov 28 2019)
clock
offset is -39655.2650 msec, root delay is 52.60 msec
root
dispersion is 55546.46 msec, peer dispersion is 16000.00 msec
NTP is
slow so you'll need to wait for few minutes for ASA to sync with the NTP
server.
Notice a
stratum of 3.
LAB-ASA5515x#
ping 162.159.200.123
Type
escape sequence to abort.
Sending
5, 100-byte ICMP Echos to 162.159.200.123, timeout is 2 seconds:
!!!!!
Success
rate is 100 percent (5/5), round-trip min/avg/max = 1/4/10 ms
LAB-ASA5515x#
show ntp associations
address ref clock st
when poll reach delay
offset disp
*~162.159.200.123
10.35.8.220 3 24
64 17 3.5
0.44 1893.5
* master (synced), # master (unsynced), +
selected, - candidate, ~ configured
LAB-ASA5515x#
show ntp associations detail
162.159.200.123 configured, our_master, sane, valid,
stratum 3
ref ID
10.35.8.220, time e189bc42.50cc575c (11:23:46.315 SGT Thu Nov 28 2019)
our mode
client, peer mode server, our poll intvl 64, peer poll intvl 64
root
delay 47.99 msec, root disp 0.56, reach 7, sync dist 3918.243
delay
3.49 msec, offset 0.4444 msec, dispersion 3891.94
precision
2**25, version 3
org time
e189bc44.33b4a2ce (11:23:48.201 SGT Thu Nov 28 2019)
rcv time
e189bc44.340a7d51 (11:23:48.203 SGT Thu Nov 28 2019)
xmt time
e189bc44.331f4ac9 (11:23:48.199 SGT Thu Nov 28 2019)
filtdelay
= 3.49 6.15
6.36 0.00 0.00
0.00 0.00 0.00
filtoffset
= 0.44 -1.14
-1.65 0.00 0.00
0.00 0.00 0.00
filterror
= 15.63 16.60
17.58 16000.0 16000.0 16000.0 16000.0 16000.0
Configure
Syslog on the ASA under Configuration > Device Management > Logging >
Logging Setup > select Enable Logging.
Configure a remote Syslog Server under Configuration > Device Management > Logging > Syslog Servers > Add.
Select Interface: inside > type IP Address: 192.168.1.130 > leave the default Protocol: UDP and Port: 514 > click OK.
Configure Logging Filters on the ASA under Configuration > Device Management > Logging > Logging Filters.
Double-click
ASDM, Internal Buffer and Syslog Servers > set the Severity level to
Debugging.
Under
Syslog from All Event Classes > select Filter on severity > select
Debugging > click OK.
Click Apply > Send.
Configure
a Modular Policy Framework (MPF) to enable sending of NetFlow traffic to the
collector under Configuration > Firewall > Service Policy Rules .
Select
inspection_default class > Add > Insert After.
Select Global - applies to all interfaces (default) > Next.
Select Create a new traffic class > type a name: ALL-TRAFFIC-NETFLOW > select Any traffic > click Next.
Enable Send for Collector: 192.168.1.100 > click OK.
Click Finish.