Cisco has announced their new "Next Level" Certification, which will take effect on February 24th, 2020. It includes major changes such as the new certification paths for DevNet, CCENT has been replaced with Cisco Certified Technician (CCT), there's only a single CCNA, a completed CCNP exam will be converted to a Cisco Specialist cert and passing a CCNP Core Exam will qualify you for the CCIE. The study materials for these new tracks are slowly being released and while waiting for the Official Certification Guides (OCG), I plan to take up CCNP Security SENSS (300-206) so I can re-certify both my CCNP R/S and CCNP Security for another three years. Also according to the CCNP Migration Tool, passing SENSS will qualify me for the Cisco Certified Specialist (for Web Content Security) and it would require me to only pass SCOR 350-701 to earn the new CCNP Security certification.
To help me prepare, I read the Implementing Cisco Edge Network Security Solutions (SENSS) Student Guide and the previous FIREWALL 642-618 OCG since there's no official OCG released for SENSS. I also watched both INE and CBT Nuggets SENSS training videos and performed labs using the Cisco Edge Network Security Solutions (SENSS) Lab Guide. Below is my SENSS lab network topology which consists of a Cisco ASA 5515-X firewall, Cisco 3560 L3 switch and VMs such as CSR1000V, ISE 2.0, Windows 7 and Kali Linux. This is the first lab blog which is the Cisco device hardening for an IOS router and ASA firewall.
Task 1: Configure Management Plane Security Controls on Cisco IOS Software
Click Yes to accept the CSRv RSA key.
Add a host or device under Tools > SNMP Entities.
Type Name: CSRv > Name: CSRv > Address: 192.168.1.140 > select SNMP V3 > under SNMPv3 > type Security Name: admin > select Security Level: Auth, Priv > select Auth Protocol: SHA > type password: cisco123 > select Priv Protocol: AES128 > type password: cisco123 > click OK > Save.
Select SSH > select: Interface Name: inside > type IP Address: 192.168.1.0 > select or type Mask: 255.255.255.0 > click OK.
Under SSH Settings > Allowed SSH Version > select 2 > click Apply.
To preview CLI commands, go to Tools > Preferences.
Select under Communications > tick Preview commands before sending them to the device.
Click Send.
Create a local user account under Configuration > Device Management > Users/AAA > User Accounts > Add.
Type Username: admin > Password: cisco > under Access Restriction > select Full access (ASDM, SSH, Telnet and Console) > select Privilege Level: 15 > click OK.
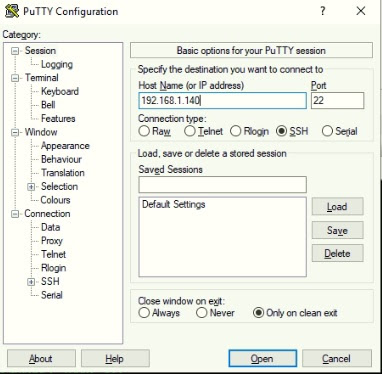
Open PuTTY and SSH to the ASA (192.168.1.1).
Click Yes to continue and accept the ASA RSA key.
Login using the admin local account created earlier.
On the same window under USM (User-based Security Model) tab > click Add > type Group name: GROUP-1 > select Security Level: priv (Authentication&Encryption).
Go to SNMPv3 User/Group.
Click Add > SNMP User.
Select Group Name: GROUP-1 (default) > type Username: admin > select Authentication Algorithm: SHA > type Authentication Password (re-type to confirm): cisco123 > select Encryption Algorithm: AES > type Encryption Password (re-type to confirm): cisco123 > select AES Size: 128 (default) > click OK.
On the same ASDM window, under SNMP Host Access List > click Add.
Select Interface Name: inside > type IP Address: 192.168.1.130 (Win7) > select SNMP Version: 3 > select or type Username/Group: admin > leave the Server Poll/Trap specification enabled (default).
Click OK > Send > Apply.
Select ASA from the drop-down option.
Click Add.
Type a Name: CSRv > optionally type a Description > type IP Address: 192.168.1.140 (default is /32 mask) > select Device Profile: Cisco.
Enable RADIUS > type Shared Secret: cisco
Click Show to display the Shared Secret.
Click Submit (found at the bottom).
You can alternatively click CSRv > Duplicate to add the ASA device and just modify its IP address.
Type Name: ASA > optionally type a Description > type IP Address: 192.168.1.1 > click Submit.
Create a user account in ISE under Administration > Identities.
Click Users (left-hand side) > Add.
Type a Name: john-ise > leave Status: Enabled (default) > optionally type Email > type Passwords: Cisco123 for both the Login and Enable passwords.
Click Submit.
You're required to create a complex password, otherwise the below pop-up message will appear.
You can view RADIUS logs in ISE under Operations > RADIUS Livelog.
You're required to install Adobe Flash. Click on the red block icon to Allow Adobe Flash.
Open a new web browser and re-login to ISE.
Notice under the Home Dashboard > Authentication there's a Passed count of 2.
A new web browser will open.
Go to Operations > Reports > ISE Reports > Endpoints and Users > Time Range: Today > Run.
Go to RADIUS Accounting > Time Range: Today > Run.
Click Details to view more info. A new web browser will open.
Go to RADIUS Authentication > Time Range: Today > Run.
Click Details to view more info. A new web browser will open.
Task 4: Configure Management Access AAA on Cisco ASA
Configure an AAA Server Group under Configuration > Device Management > Users/AAA > AAA Server Groups > Add.
Type AAA Server Group Name: RADIUS-1 > select Protocol: RADIUS > leave other settings in default > click OK.
Select RADIUS-1 (AAA Server Group) > under Servers in the Selected Group > click Add.
Select Interface Name: inside > type Server Name or IP Address: 192.168.1.1 > type the Server Secret Key: cisco (should be the same in ISE) > type Common Password: cisco > click OK.
You can verify AAA authentication to ISE by clicking Test > select Authentication > type Username: john-ise > type Password: Cisco123 > click OK.
Apply AAA on the ASA under Configuration > Device Management > Users/AAA > AAA Access.
Under Authentication tab > enable SSH > select Server Group: RADIUS-1 > Use LOCAL when server group fails is enabled by default.
Go to Authorization tab > Under Perform authorization for exec shell access > select Enable > Remote server.
Go to Accounting tab > enable SSH > Server Group: RADIUS-1 (default).
Click Apply. A pop-up message will appear. Click Yes to Continue.
Open PuTTY and SSH to ASA (192.168.1.1) using the john-ise ISE login account.
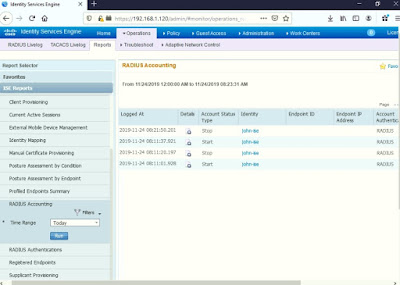
To view RADIUS logs in ISE, go to Operations > Reports > ISE Reports > RADIUS Accounting > Time Range: Today > Run.
Click Details to view more info. A new web browser will be opened.
Go to Operations > Reports > ISE Reports > RADIUS Authentication > Time Range: Today > Run.
Click Details to view more info. A new web browser will be opened.
To help me prepare, I read the Implementing Cisco Edge Network Security Solutions (SENSS) Student Guide and the previous FIREWALL 642-618 OCG since there's no official OCG released for SENSS. I also watched both INE and CBT Nuggets SENSS training videos and performed labs using the Cisco Edge Network Security Solutions (SENSS) Lab Guide. Below is my SENSS lab network topology which consists of a Cisco ASA 5515-X firewall, Cisco 3560 L3 switch and VMs such as CSR1000V, ISE 2.0, Windows 7 and Kali Linux. This is the first lab blog which is the Cisco device hardening for an IOS router and ASA firewall.
Task 1: Configure Management Plane Security Controls on Cisco IOS Software
Configure
a hostname, domain name for creating the RSA key pair.
CSRv#configure
terminal
Enter
configuration commands, one per line.
End with CNTL/Z.
CSRv(config)#ip
domain-name lab.com
CSRv(config)#crypto
key generate rsa modulus 2048
The name for the keys will be: CSRv.lab.com
% The key
modulus size is 2048 bits
%
Generating 2048 bit RSA keys, keys will be non-exportable...
[OK]
(elapsed time was 3 seconds)
CSRv(config)#ip
ssh version ?
2
Protocol Version to be supported
CSRv(config)#ip
ssh version 2
CSRv(config)#username
admin privilege 15 password cisco
CSRv(config)#line
vty 0 4
CSRv(config-line)#transport
input ?
acercon
Remote console for ACE-based blade
all
All protocols
lat
DEC LAT protocol
mop
DEC MOP Remote Console Protocol
nasi
NASI protocol
none
No protocols
pad
X.3 PAD
rlogin
Unix rlogin protocol
ssh
TCP/IP SSH protocol
telnet
TCP/IP Telnet protocol
udptn
UDPTN async via UDP protocol
CSRv(config-line)#transport
input all
CSRv(config-line)#login
?
local
Local password checking
<cr>
CSRv(config-line)#login
local
Open
PuTTY and SSH to CSRv 192.168.1.140.
Click Yes to accept the CSRv RSA key.
Configure
SNMP Contact and Location on CSRv.
CSRv(config)#snmp-server
?
accounting SNMP Accounting parameters
cache Enable SNMP cache
chassis-id String to uniquely identify this
chassis
community Enable SNMP; set community string and
access privs
contact Text for mib object sysContact
context Create/Delete a context apart from
default
dbal snmp database access layer
drop Silently drop SNMP packets
enable Enable SNMP Traps
engineID Configure a local or remote SNMPv3
engineID
file-transfer File transfer related commands
group Define a User Security Model group
host Specify hosts to receive SNMP
notifications
ifindex Enable ifindex persistence
inform Configure SNMP Informs options
ip IP ToS configuration for SNMP
traffic
location Text for mib object sysLocation
manager Modify SNMP manager parameters
packetsize Largest SNMP packet size
password-policy SNMP v3 users password policy
queue-length Message queue length for each TRAP host
source-interface Assign an source interface
system-shutdown Enable use of the SNMP reload command
tftp-server-list Limit TFTP servers used via SNMP
trap SNMP trap options
trap-source Assign an interface for the source
address of all traps
trap-timeout Set timeout for TRAP message
retransmissions
user Define a user who can access the
SNMP engine
view Define an SNMPv2 MIB view
CSRv(config)#snmp-server
contact ?
LINE
identification of the contact person for this managed node
CSRv(config)#snmp-server
contact John Lagura
CSRv(config)#snmp-server
location ?
LINE
The physical location of this node
CSRv(config)#snmp-server
location Singapore
Configure
SNMPv3 User and Group on CSRv.
CSRv(config)#snmp-server
group ?
WORD
Name of the group
CSRv(config)#snmp-server
group GROUP-1 ?
v1
group using the v1 security model
v2c
group using the v2c security model
v3
group using the User Security Model (SNMPv3)
CSRv(config)#snmp-server
group GROUP-1 v3 ?
auth
group using the authNoPriv Security Level
noauth
group using the noAuthNoPriv Security Level
priv
group using SNMPv3 authPriv security level
CSRv(config)#snmp-server
group GROUP-1 v3 priv
CSRv(config)#snmp-server
user ?
WORD
Name of the user
CSRv(config)#snmp-server
user admin ?
WORD
Group to which the user belongs
CSRv(config)#snmp-server
user admin GROUP-1 ?
remote
Specify a remote SNMP entity to which the user belongs
v1
user using the v1 security model
v2c
user using the v2c security model
v3
user using the v3 security model
CSRv(config)#snmp-server
user admin GROUP-1 v3 ?
access
specify an access-list associated with this group
auth
authentication parameters for the user
encrypted
specifying passwords as MD5 or SHA digests
<cr>
CSRv(config)#snmp-server
user admin GROUP-1 v3 auth ?
md5
Use HMAC MD5 algorithm for authentication
sha
Use HMAC SHA algorithm for authentication
CSRv(config)#snmp-server
user admin GROUP-1 v3 auth sha ?
WORD
authentication password for user
CSRv(config)#snmp-server
user admin GROUP-1 v3 auth sha cisco123 ?
access
specify an access-list associated with this group
priv
encryption parameters for the user
<cr>
CSRv(config)#snmp-server
user admin GROUP-1 v3 auth sha cisco123 priv ?
3des
Use 168 bit 3DES algorithm for encryption
aes
Use AES algorithm for encryption
des
Use 56 bit DES algorithm for encryption
CSRv(config)#snmp-server
user admin GROUP-1 v3 auth sha cisco123 priv aes ?
128
Use 128 bit AES algorithm for encryption
192
Use 192 bit AES algorithm for encryption
256
Use 256 bit AES algorithm for encryption
CSRv(config)#snmp-server
user admin GROUP-1 v3 auth sha cisco priv aes 128 ?
WORD
privacy password for user
CSRv(config)#snmp-server
user admin GROUP-1 v3 auth sha cisco123 priv aes 128 cisco123
Configure
SNMP Server and sending of SNMP Traps
CSRv(config)#snmp-server
host ?
WORD
IP/IPV6 address of SNMP notification host
CSRv(config)#snmp-server
host 192.168.1.130 ?
WORD
SNMPv1/v2c community string or SNMPv3 user name
informs
Send Inform messages to this host
traps
Send Trap messages to this host
version
SNMP version to use for notification messages
vrf
VPN Routing instance for this host
CSRv(config)#snmp-server
host 192.168.1.130 version ?
1 Use
SNMPv1
2c Use
SNMPv2c
3 Use
SNMPv3
CSRv(config)#snmp-server
host 192.168.1.130 version 3 ?
auth
Use the SNMPv3 authNoPriv Security Level
noauth
Use the SNMPv3 noAuthNoPriv Security Level
priv
Use the SNMPv3 authPriv Security Level
CSRv(config)#snmp-server
host 192.168.1.130 version 3 priv ?
WORD
SNMPv1/v2c community string or SNMPv3 user name
CSRv(config)#snmp-server
host 192.168.1.130 version 3 priv admin
CSRv(config)#snmp-server
enable ?
traps
Enable SNMP Traps
CSRv(config)#snmp-server
enable traps
To verify
SNMP statistics and User configuration use the show snmp
and show snmp user repectively.
CSRv#show
snmp ?
chassis
show snmp chassis
community
show snmp communities
contact
show snmp contacts
context
show snmp contexts
engineID
show local and remote SNMP engine IDs
group
show SNMPv3 groups
host
show snmp hosts
location
show snmp location
mib
show mib objects
pending
snmp manager pending requests
sessions
snmp manager sessions
stats
show snmp statistics
user
show SNMPv3 users
view
show snmp views
|
Output modifiers
<cr>
CSRv#show
snmp
Chassis:
970RTIIDHGK
Contact:
John Lagura
Location:
Singapore
0 SNMP
packets input
0 Bad SNMP version errors
0 Unknown community name
0 Illegal operation for community name
supplied
0 Encoding errors
0 Number of requested variables
0 Number of altered variables
0 Get-request PDUs
0 Get-next PDUs
0 Set-request PDUs
0 Input queue packet drops (Maximum queue
size 1000)
0 SNMP
packets output
0 Too big errors (Maximum packet size 1500)
0 No such name errors
0 Bad values errors
0 General errors
0 Response PDUs
0 Trap PDUs
Packets
currently in SNMP process input queue: 0
SNMP
global trap: enabled
SNMP
logging: enabled
Logging to 192.168.1.130.162, 0/10, 0 sent,
0 dropped.
CSRv#show
snmp user
User
name: admin
Engine
ID: 800000090300000C29B8D42E
storage-type:
nonvolatile active
Authentication
Protocol: SHA
Privacy
Protocol: AES128
Group-name:
GROUP-1
Download
and run HiliSoft MIB Browser on Windows 7 machine (192.168.1.130).
Add a host or device under Tools > SNMP Entities.
Type Name: CSRv > Name: CSRv > Address: 192.168.1.140 > select SNMP V3 > under SNMPv3 > type Security Name: admin > select Security Level: Auth, Priv > select Auth Protocol: SHA > type password: cisco123 > select Priv Protocol: AES128 > type password: cisco123 > click OK > Save.
To verify
SNMPv3, expand iso > org > dod > internet > mgmt > mib-2 >
system > sysContact > Get > click Go/Play (green arrow icon).
Notice
the Value of John Lagura.
Click
sysLocation > Get > Go.
Notice
the Value of Singapore.
Open a
terminal prompt on Kali Linux machine (192.168.1.110) and run the SNMP Walk command: snmpwalk -v3 -l
authPriv -u admin -a SHA -A cisco123 -x AES -X cisco123 192.168.1.140.
I ran SNMP Walk on several terminal prompts to simulate an SNMP Flood Attack and overwhelm the CSRv CPU.
Issue a show processes cpu sorted on CSRv to view CPU
utilization.
Notice
the CPU jumped to 22% and SNMP ENGINE Process had a 7.04% CPU usage.
CSRv#show
processes cpu sorted
CPU utilization for five seconds: 1%/0%; one minute:
0%; five minutes: 0%
PID Runtime(ms) Invoked uSecs
5Sec 1Min 5Min TTY Process
9
48135 6245 7707
0.39% 0.12% 0.11%
0 Check heaps
121
6088 2088644 2
0.23% 0.09% 0.08%
0 L2 LISP Punt Pro
220
800 266152 3
0.07% 0.01% 0.00%
0 Tunnel BGP
194
2779 1055371 2
0.07% 0.03% 0.02%
0 IPAM Manager
117
268 5380 49
0.07% 0.00% 0.00%
0 IOSXE-RP Punt Se
408
2420 533168 4
0.07% 0.02% 0.00%
0 MMA DB TIMER
185
2485 533169 4
0.07% 0.04% 0.02%
0 VRRS Main thread
99
1024 341783 2
0.07% 0.01% 0.00%
0 100ms check
8
0 1 0
0.00% 0.00% 0.00%
0 RO Notify Timers
7
2 1 2000
0.00% 0.00% 0.00%
0 EDDRI_MAIN
3
0 1 0
0.00% 0.00% 0.00%
0 PKI Trustpool
<SNIP>
CSRv#show
processes cpu sorted
CPU utilization for five seconds: 16%/3%; one
minute: 3%; five minutes: 1%
PID Runtime(ms) Invoked uSecs
5Sec 1Min 5Min TTY Process
482 1410 3478 405
4.55% 0.74% 0.29%
0 SNMP ENGINE
450
955 6967 137
3.43% 0.50% 0.19%
0 IP SNMP
470
683 3477 196
2.55% 0.36% 0.13%
0 PDU DISPATCHER
117
576 8799 65
1.19% 0.16% 0.06%
0 IOSXE-RP Punt Se
194
2903 1058738 2
0.23% 0.09% 0.04%
0 IPAM Manager
121
6295 2095288 3
0.15% 0.15% 0.11%
0 L2 LISP Punt Pro
185
2548 534882 4
0.15% 0.06% 0.03%
0 VRRS Main thread
389
289 34842 8
0.07% 0.00% 0.00%
0 NTP
77
7883 31599 249
0.07% 0.03% 0.00%
0 IOSD ipc task
197
2726 1058738 2
0.07% 0.05% 0.03%
0 IP ARP Retry Age
408
2489 534880 4
0.07% 0.05% 0.02%
0 MMA DB TIMER
11
0 1 0
0.00% 0.00% 0.00%
0 DiscardQ Backgro
13
1 253 3
0.00% 0.00% 0.00%
0 WATCH_AFS
12
0 2 0
0.00% 0.00% 0.00%
0 Timers
CSRv#show
processes cpu sorted
CPU utilization for five seconds: 22%/4%; one
minute: 6%; five minutes: 2%
PID Runtime(ms) Invoked uSecs
5Sec 1Min 5Min TTY Process
482 1910 4568 418
7.04% 1.58% 0.49%
0 SNMP ENGINE
450
1314 9155 143
5.12% 1.14% 0.34%
0 IP SNMP
470
916 4567 200
2.95% 0.75% 0.22%
0 PDU DISPATCHER
117
709 9919 71
1.83% 0.38% 0.11%
0 IOSXE-RP Punt Se
618
133 290 458
0.31% 0.03% 0.00%
1 Virtual Exec
121
6310 2095804 3
0.23% 0.16% 0.11%
0 L2 LISP Punt Pro
194
2913 1059007 2
0.15% 0.11% 0.05%
0 IPAM Manager
408
2497 535019 4
0.15% 0.06% 0.02%
0 MMA DB TIMER
99
1053 342969 3
0.07% 0.01% 0.00%
0 100ms check
344
1159 13712 84
0.07% 0.00% 0.00%
0 DiagCard1/-1
455
486 35435 13
0.07% 0.00% 0.00%
0 Crypto IKEv2
197
2730 1059007 2
0.07% 0.05% 0.03%
0 IP ARP Retry Age
13
1 253 3
0.00% 0.00% 0.00%
0 WATCH_AFS
12
0 2 0
0.00% 0.00% 0.00%
0 Timers
<SNIP>
Configure
a Control Plan Protection (CPPr) policy on CSRv to mitigate SNMP Flood Attack.
Configure
an Extended ACL to capture SNMP traffic.
CSRv(config)#ip
access-list extended SNMP
CSRv(config-ext-nacl)#permit
udp any any eq snmp
Configure
a Class Map to match the ACL created earlier.
CSRv(config)#class-map
SNMP-CMAP
CSRv(config-cmap)#match
?
access-group Access group
any Any packets
application Application to match
cac Call Admission Control
class-map Class map
cos IEEE 802.1Q/ISL class of
service/user priority values
destination-address Destination address
discard-class Discard behavior identifier
dscp Match DSCP in IPv4 and IPv6
packets
group-object Match object-group
input-interface Select an input interface to match
ip IP specific values
metadata Metadata to match
mpls Multi Protocol Label Switching
specific values
not Negate this match result
packet Layer 3 Packet length
precedence Match Precedence in IPv4 and IPv6
packets
protocol Protocol
qos-group Qos-group
security-group Security group
source-address Source address
vlan VLANs to match
CSRv(config-cmap)#match
access-group ?
<1-2799> Access list index
name
Named Access List
CSRv(config-cmap)#match
access-group name ?
WORD
Access List name
CSRv(config-cmap)#match
access-group name SNMP
Configure
a Policy Map to "police" SNMP traffic to just 32 kbps only.
CSRv(config)#policy-map
CPPr
CSRv(config-pmap)#?
Policy-map
configuration commands:
class
policy criteria
description
Policy-Map description
exit
Exit from policy-map configuration mode
no
Negate or set default values of a command
CSRv(config-pmap)#class
SNMP-CMAP
CSRv(config-pmap-c)#?
Policy-map
class configuration commands:
admit Admit the request for
bandwidth Bandwidth
exit Exit from class action
configuration mode
fair-queue Enable Flow-based Fair Queuing in this
Class
forward forward action
netflow-sampler NetFlow action
no Negate or set default values of
a command
police Police
priority Strict Scheduling Priority for this
Class
queue-limit Queue Max Threshold for Tail Drop
random-detect Enable Random Early Detection as drop
policy
service-policy Configure QoS Service Policy
set Set QoS values
shape Traffic Shaping
CSRv(config-pmap-c)#police
?
<8000-10000000000> Target Bit Rate (bIts per second) (postfix k,
m, g optional; decimal point allo
cir Committed information rate
rate Specify police rate, PCR for
hierarchical policies or SCR for single-level ATM 4.0 policer policies
CSRv(config-pmap-c)#police
rate ?
<1-10000000000> Rate value (postfix k, m, g optional; decimal
point allowed)
percent % of interface bandwidth for rate
CSRv(config-pmap-c)#police
rate 32000 ?
account Overhead Accounting
bps Treat 'rate' value in
bits-per-second
burst Specify 'burst' parameter
conform-action action when rate is less than conform burst
cps Treat 'rate' value in
cells-per-second
peak-rate Specify peak rate or PCR for
single-level ATM 4.0 policer policies
pps Treat 'rate' value in
packets-per-second
<cr>
CSRv(config-pmap-c)#police
rate 32000 bps ?
account Overhead Accounting
burst Specify 'burst' parameter
conform-action action when rate is less than conform burst
peak-rate Specify peak rate or PCR for
single-level ATM 4.0 policer policies
<cr>
CSRv(config-pmap-c)#police
rate 32000 bps burst ?
<1000-512000000> Burst value in bytes
CSRv(config-pmap-c)#police
rate 32000 bps burst 1500 ?
bytes
Treat 'burst' value as bytes
CSRv(config-pmap-c)#police
rate 32000 bps burst 1500 bytes ?
account Overhead Accounting
conform-action action when rate is less than conform burst
peak-burst Specify 'peak-burst' parameter for
'peak-rate'
peak-rate Specify peak rate or PCR for
single-level ATM 4.0 policer policies
<cr>
CSRv(config-pmap-c)#police
rate 32000 bps burst 1500 bytes conform-action ?
drop drop packet
set-clp-transmit set atm clp and send it
set-cos-inner-transmit rewrite packet inner cos and send
it
set-cos-transmit rewrite packet cos and send
it
set-discard-class-transmit set discard-class and send it
set-dscp-transmit set dscp and send it
set-dscp-tunnel-transmit rewrite tunnel packet dscp and send
it
set-mpls-exp-imposition-transmit set exp at tag imposition and send it
set-mpls-exp-topmost-transmit set exp on topmost label and send it
set-prec-transmit rewrite packet precedence and
send it
set-prec-tunnel-transmit rewrite tunnel packet precedence and
send it
set-qos-transmit set qos-group and send it
transmit transmit packet
CSRv(config-pmap-c)#police
rate 32000 bps burst 1500 bytes conform-action transmit ?
exceed-action
action when rate is within conform and conform + exceed burst
<cr>
CSRv(config-pmap-c)#police
rate 32000 bps burst 1500 bytes conform-action transmit exceed-action ?
drop drop packet
set-clp-transmit set atm clp and send it
set-cos-inner-transmit set inner cos and send it
set-cos-transmit set cos and send it
set-discard-class-transmit set discard-class and send it
set-dscp-transmit set dscp and send it
set-dscp-tunnel-transmit rewrite tunnel packet dscp and send
it
set-mpls-exp-imposition-transmit set exp at tag imposition and send it
set-mpls-exp-topmost-transmit set exp on topmost label and send it
set-prec-transmit rewrite packet precedence and
send it
set-prec-tunnel-transmit rewrite tunnel packet precedence and
send it
set-qos-transmit set qos-group and send it
transmit transmit packet
CSRv(config-pmap-c)#police
rate 32000 bps burst 1500 bytes conform-action transmit exceed-action drop
Apply the
Policy Map to the Control Plane.
CSRv(config)#control-plane
CSRv(config-cp)#?
Control
Plane configuration commands:
exit Exit from control-plane
configuration mode
no Negate or set default values of a
command
service-policy Configure QOS Service Policy
CSRv(config-cp)#service-policy
?
input
Assign policy-map to the input of an interface
output
Assign policy-map to the output of an interface
CSRv(config-cp)#service-policy
input CPPr
I ran
again multiple SNMP Walk on Kali Linux towards CSRv.
Notice
the CSRv CPU is only 2-3% and SNMP ENGINE Process is less than 1%.
CSRv#show
processes cpu sorted
CPU utilization for five seconds: 3%/0%; one minute:
2%; five minutes: 1%
PID Runtime(ms) Invoked uSecs
5Sec 1Min 5Min TTY Process
618
375 798 469
0.47% 0.13% 0.06%
1 Virtual Exec
121
7890 2198311 3
0.31% 0.22% 0.16%
0 L2 LISP Punt Pro
482 2480 5889 421
0.31% 0.11% 0.02%
0 SNMP ENGINE
117
900 12403 72
0.23% 0.04% 0.01%
0 IOSXE-RP Punt Se
197
3483 1110677 3
0.23% 0.14% 0.08%
0 IP ARP Retry Age
219
256 17978 14
0.07% 0.00% 0.00%
0 Spanning Tree
194
3619 1110678 3
0.07% 0.08% 0.06%
0 IPAM Manager
185
3149 561076 5
0.07% 0.09% 0.06%
0 VRRS Main thread
286
42 4065 10
0.07% 0.00% 0.00%
0 TCP Timer
450
1675 11801 141
0.07% 0.06% 0.01%
0 IP SNMP
470
1227 5886 208
0.07% 0.06% 0.01%
0 PDU DISPATCHER
408
3039 561075 5
0.07% 0.08% 0.05%
0 MMA DB TIMER
220
1024 280084 3
0.07% 0.03% 0.00%
0 Tunnel BGP
91
113 35959 3
0.07% 0.00% 0.00%
0 RP HA Periodic
83
664 17961 36
0.07% 0.01% 0.00%
0 PuntInject Keepa
77
8329 33191 250
0.07% 0.05% 0.02%
0 IOSD ipc task
99
1297 359658 3
0.07% 0.04% 0.02%
0 100ms check
17
0 1 0
0.00% 0.00% 0.00%
0 WSMA_NOTIFY
<SNIP>
CSRv#show
processes cpu sorted
CPU utilization for five seconds: 2%/0%; one minute:
2%; five minutes: 1%
PID Runtime(ms) Invoked uSecs
5Sec 1Min 5Min TTY Process
134
11421 1201 9509
0.55% 0.06% 0.00%
0 Per-minute Jobs
121
7908 2198602 3
0.23% 0.22% 0.16%
0 L2 LISP Punt Pro
450
1680 11863 141
0.23% 0.07% 0.02%
0 IP SNMP
482 2488 5920 420
0.23% 0.12% 0.03%
0 SNMP ENGINE
185
3151 561152 5
0.15% 0.09% 0.06%
0 VRRS Main thread
470
1234 5917 208
0.15% 0.07% 0.02%
0 PDU DISPATCHER
197
3487 1110826 3
0.15% 0.14% 0.08%
0 IP ARP Retry Age
2
1889 7194 262
0.07% 0.01% 0.00%
0 Load Meter
618
380 806 471
0.07% 0.13% 0.06%
1 Virtual Exec
117
901 12442 72
0.07% 0.05% 0.01%
0 IOSXE-RP Punt Se
295
302 17981 16
0.07% 0.00% 0.00%
0 CEF: IPv4 proces
276
165 35948 4
0.07% 0.00% 0.00%
0 nbar-sdavc-sched
220
1024 280122 3
0.07% 0.03% 0.00%
0 Tunnel BGP
455
521 37164 14
0.07% 0.00% 0.00%
0 Crypto IKEv2
408
3045 561150 5
0.07% 0.07% 0.05%
0 MMA DB TIMER
194
3620 1110826 3
0.07% 0.08% 0.07%
0 IPAM Manager
16
0 1 0
0.00% 0.00% 0.00%
0 DB Notification
15
0 1 0
0.00% 0.00% 0.00%
0 DB Lock Manager
<SNIP>
The SNMP
Walk process ran very slow due to the CCPr policy on CSRv. Issue a show policy-map control-plane to verify
matched packets.
CSRv#show
policy-map control-plane ?
all
Show all control plane policies
input
Input policy
output
Output policy
|
Output modifiers
<cr>
CSRv#show
policy-map control-plane
Control Plane
Service-policy input: CPPr
Class-map: SNMP-CMAP (match-all)
3006
packets, 532464 bytes
5 minute offered rate 15000 bps, drop
rate 2000 bps
Match: access-group name SNMP
police:
rate 32000 bps, burst 1500 bytes
conformed 2458 packets, 435337 bytes; actions:
transmit
exceeded
548 packets, 97127 bytes; actions:
drop
conformed 12000 bps, exceeded 2000 bps
Class-map: class-default (match-any)
608 packets, 28469 bytes
5 minute offered rate 1000 bps, drop rate
0000 bps
Match: any
Task 2:
Configure Management Plane Security Controls on Cisco ASA
Configure
SSH and HTTPS access via ASDM under Configuration > Device Management >
Management Access > ASDM/HTTPS/Telnet/SSH > click Add.
Select SSH > select: Interface Name: inside > type IP Address: 192.168.1.0 > select or type Mask: 255.255.255.0 > click OK.
Under SSH Settings > Allowed SSH Version > select 2 > click Apply.
To preview CLI commands, go to Tools > Preferences.
Select under Communications > tick Preview commands before sending them to the device.
Click Send.
Create a local user account under Configuration > Device Management > Users/AAA > User Accounts > Add.
Type Username: admin > Password: cisco > under Access Restriction > select Full access (ASDM, SSH, Telnet and Console) > select Privilege Level: 15 > click OK.
To enable
LOCAL authentication using the local user account, go to Configuration >
Device Management > Users/AAA > AAA Access > Authentication tab >
tick HTTP/ASDM and tick SSH.
The
Server Group: LOCAL is automatically selected.
Open PuTTY and SSH to the ASA (192.168.1.1).
Click Yes to continue and accept the ASA RSA key.
Login using the admin local account created earlier.
Configure
SNMP Contact and Location on the ASA under Configuration > Device Management
> Management Access > SNMP.
Type
Contact: John L > type ASA Location: SG.
On the same window under USM (User-based Security Model) tab > click Add > type Group name: GROUP-1 > select Security Level: priv (Authentication&Encryption).
Go to SNMPv3 User/Group.
Click Add > SNMP User.
Select Group Name: GROUP-1 (default) > type Username: admin > select Authentication Algorithm: SHA > type Authentication Password (re-type to confirm): cisco123 > select Encryption Algorithm: AES > type Encryption Password (re-type to confirm): cisco123 > select AES Size: 128 (default) > click OK.
On the same ASDM window, under SNMP Host Access List > click Add.
Select Interface Name: inside > type IP Address: 192.168.1.130 (Win7) > select SNMP Version: 3 > select or type Username/Group: admin > leave the Server Poll/Trap specification enabled (default).
Click OK > Send > Apply.
Open MIB
Browser > Tools > SNMP Entities > click New.
Type
Entity: ASA > type Name: ASA > type Address: 192.168.1.1 > select SNMP
V3 > under SNMPv3 > type Security Name: admin > select Security Level:
Auth, Priv > select Auth Protocol: SHA > type password: cisco123 >
select Priv Protocol: AES128 > type password: cisco123 > click OK >
Save.
Select ASA from the drop-down option.
To verify
SNMPv3, expand iso > org > dod > internet > mgmt > mib-2 >
system > sysContact > Get > click Go/Play (green arrow icon).
Notice
the Value of John L.
Task 3:
Configure Management Access AAA on Cisco IOS Software
Configure
ISE for RADIUS.
Add CSRv
in ISE under Administration > Network Resources > Network Devices.
Click Add.
Type a Name: CSRv > optionally type a Description > type IP Address: 192.168.1.140 (default is /32 mask) > select Device Profile: Cisco.
Enable RADIUS > type Shared Secret: cisco
Click Show to display the Shared Secret.
Click Submit (found at the bottom).
You can alternatively click CSRv > Duplicate to add the ASA device and just modify its IP address.
Type Name: ASA > optionally type a Description > type IP Address: 192.168.1.1 > click Submit.
Create a user account in ISE under Administration > Identities.
Click Users (left-hand side) > Add.
Type a Name: john-ise > leave Status: Enabled (default) > optionally type Email > type Passwords: Cisco123 for both the Login and Enable passwords.
Click Submit.
You're required to create a complex password, otherwise the below pop-up message will appear.
Configure
RADIUS server on CSRv.
CSRv(config)#do
ping 192.168.1.120
Type
escape sequence to abort.
Sending
5, 100-byte ICMP Echos to 192.168.1.120, timeout is 2 seconds:
!!!!!
Success
rate is 100 percent (5/5), round-trip min/avg/max = 2/3/6 ms
CSRv(config)#radius
?
filter
Packet filter configuration
server
Server configuration
CSRv(config)#radius
server ?
WORD
Name for the radius server configuration
CSRv(config)#radius
server RADIUS-1
CSRv(config-radius-server)#?
RADIUS
server sub-mode commands:
address Specify the radius server address
automate-tester Configure server automated testing.
backoff Retry backoff pattern(Default is
retransmits with constant delay)
dtls Configure DTLS parameters
exit Exit from RADIUS server
configuration mode
key Per-server encryption key
key-wrap per-server keywrap configuration
no Negate a command or set its
defaults
non-standard Attributes to be parsed that violate
RADIUS standard
pac Protected Access Credential key
retransmit Number of retries to active server
(overrides default)
timeout Time to wait (in seconds) for this
radius server to reply (overrides default)
CSRv(config-radius-server)#address
?
ipv4
IPv4 Address
ipv6
IPv6 Address
CSRv(config-radius-server)#address
ipv4 ?
Hostname or A.B.C.D IPv4 Address of radius server
CSRv(config-radius-server)#address
ipv4 192.168.1.120
CSRv(config-radius-server)#key
?
0
Specifies an UNENCRYPTED key will follow
6
Specifies ENCRYPTED key will follow
7
Specifies HIDDEN key will follow
LINE
The UNCRYPTED (cleartext) shared key
CSRv(config-radius-server)#key
cisco
Configure
AAA (Authentication, Authorization, Accounting) on CSRv.
CSRv(config)#aaa
?
new-model
Enable NEW access control commands and functions.(Disables OLD commands.)
CSRv(config)#aaa
new-model
CSRv(config)#aaa
?
accounting Accounting configurations parameters.
attribute AAA attribute definitions
authentication Authentication configurations parameters.
authorization Authorization configurations parameters.
cache AAA cache definitions
configuration Authorization configuration parameters.
dnis Associate certain AAA parameters
to a specific DNIS number
group AAA group definitions
intercept Enable intercept function
local AAA Local method options
login AAA login enable display
max-sessions Adjust initial hash size for estimated max
sessions
memory AAA memory parameters
nas NAS specific configuration
new-model Enable NEW access control commands and
functions.(Disables OLD commands.)
password Configure password/secret related
settings
pod POD processing
policy AAA policy parameters
route Static route downloading
server Local AAA server
service-profile Service-Profile parameters
session-id AAA Session ID
session-mib AAA session MIB options
traceback Traceback recording
user AAA user definitions
CSRv(config)#aaa
authentication ?
arap Set authentication lists for arap.
attempts Set the maximum number of
authentication attempts
banner Message to use when starting
login/authentication.
dot1x Set authentication lists for IEEE
802.1x.
enable Set authentication list for enable.
eou Set authentication lists for
EAPoUDP
fail-message Message to use for failed
login/authentication.
login Set authentication lists for
logins.
onep Set authentication lists for ONEP
password-prompt Text to use when prompting for a password
ppp Set authentication lists for ppp.
rejected Set blocking action for failed logins
sgbp Set authentication lists for sgbp.
suppress Do not send access request for a
specific type of user.
username-prompt Text to use when prompting for a username
CSRv(config)#aaa
authentication login ?
WORD
Named authentication list (max 31 characters, longer will be rejected).
default
The default authentication list.
CSRv(config)#aaa
authentication login ACCESS-1 ?
cache
Use Cached-group
enable
Use enable password for authentication.
group
Use Server-group
krb5
Use Kerberos 5 authentication.
krb5-telnet
Allow logins only if already authenticated via Kerberos V Telnet.
line
Use line password for authentication.
local
Use local username authentication.
local-case
Use case-sensitive local username authentication.
none
NO authentication.
passwd-expiry
enable the login list to provide password aging support
CSRv(config)#aaa
authentication login ACCESS-1 group ?
WORD
Server-group name
ldap
Use list of all LDAP hosts.
radius
Use list of all Radius hosts.
tacacs+
Use list of all Tacacs+ hosts.
CSRv(config)#aaa
authentication login ACCESS-1 group radius ?
cache
Use Cached-group
enable
Use enable password for authentication.
group
Use Server-group
krb5
Use Kerberos 5 authentication.
line
Use line password for authentication.
local
Use local username authentication.
local-case
Use case-sensitive local username authentication.
none
NO authentication.
<cr>
CSRv(config)#aaa
authentication login ACCESS-1 group radius local
CSRv(config)#aaa
authorization ?
auth-proxy For Authentication Proxy Services
cache For AAA cache configuration
commands For exec (shell) commands.
config-commands For configuration mode commands.
configuration For downloading configurations from AAA
server
console For enabling console
authorization
credential-download For downloading EAP credential from
Local/RADIUS/LDAP
exec For starting an exec (shell).
ipmobile For Mobile IP services.
multicast For downloading Multicast
configurations from an AAA server
network For network services. (PPP, SLIP,
ARAP)
onep For ONEP authorization service
policy-if For diameter policy interface
application.
prepaid For diameter prepaid services.
radius-proxy For proxying radius packets
reverse-access For reverse access connections
subscriber-service For iEdge subscriber services (VPDN etc)
template Enable template authorization
CSRv(config)#aaa
authorization exec ?
WORD
Named authorization list (max 31 characters, longer will be rejected).
default
The default authorization list.
CSRv(config)#aaa
authorization exec ACCESS-1 ?
cache Use Cached-group
group Use server-group.
if-authenticated Succeed if user has authenticated.
krb5-instance Use Kerberos instance privilege maps.
local Use local database.
none No authorization (always
succeeds).
CSRv(config)#aaa
authorization exec ACCESS-1 group ?
WORD
Server-group name
ldap
Use list of all LDAP hosts.
radius
Use list of all Radius hosts.
tacacs+
Use list of all Tacacs+ hosts.
CSRv(config)#aaa
authorization exec ACCESS-1 group radius local
CSRv(config)#aaa
accounting ?
auth-proxy For authentication proxy events.
commands For exec (shell) commands.
connection For outbound connections. (telnet,
rlogin)
delay-start Delay PPP Network start record until
peer IP address is known.
dot1x For dot1x sessions.
exec For starting an exec (shell).
gigawords 64 bit interface counters to support
Radius attributes 52 & 53.
identity For identity sessions
include Include attributes in accounting
records unconditionally
jitter Set jitter parameters for periodic
interval
multicast For multicast accounting.
nested When starting PPP from EXEC,
generate NETWORK records before EXEC-STOP record.
network For network services. (PPP, SLIP,
ARAP)
onep For ONEP events.
redundancy AAA platform redundancy accounting
behavior
resource For resource events.
send Send records to accounting
server.
session-duration Set the preference for calculating session
durations
suppress Do not generate accounting records
for a specific type of user.
system For system events.
update Enable accounting update records.
vrrs For VRRS accounting.
CSRv(config)#aaa
accounting exec ?
WORD
Named Accounting list (max 31 characters, longer will be rejected).
default
The default accounting list.
CSRv(config)#aaa
accounting exec ACCESS-1 ?
none
No accounting.
start-stop
Record start and stop without waiting
stop-only
Record stop when service terminates.
<cr>
CSRv(config)#aaa
accounting exec ACCESS-1 start-stop ?
broadcast
Use Broadcast for Accounting
group
Use Server-group
CSRv(config)#aaa
accounting exec ACCESS-1 start-stop group ?
WORD
Server-group name
radius
Use list of all Radius hosts.
tacacs+
Use list of all Tacacs+ hosts.
CSRv(config)#aaa
accounting exec ACCESS-1 start-stop group radius
Apply AAA
on VTY Lines.
CSRv(config)#line
vty 0 4
CSRv(config-line)#?
Line
configuration commands:
absolute-timeout Set absolute timeout for line
disconnection
access-class Filter connections based on an
IP access list
accounting Accounting parameters
activation-character Define the activation character
arap Appletalk Remote Access
Protocol
authorization Authorization parameters
autobaud Set line to normal autobaud
autocommand Automatically execute an EXEC
command
autocommand-options Autocommand options
autohangup Automatically hangup when
last connection closes
autoselect Set line to autoselect
buffer-length Set DMA buffer length
data-character-bits Size of characters being handled
databits Set number of data bits per
character
default Set a command to its
defaults
disconnect-character Define the disconnect character
dispatch-character Define the dispatch character
dispatch-machine Reference a TCP dispatch state
machine
dispatch-timeout Set the dispatch timer
domain-lookup Enable domain lookups in show
commands
editing Enable command line
editing
escape-character Change the current line's escape
character
exec Configure EXEC
exec-banner Enable the display of the EXEC
banner
exec-character-bits Size of characters to the command exec
exec-timeout Set the EXEC timeout
exit Exit from line
configuration mode
flowcontrol Set the flow control
flush-at-activation Clear input stream at activation
full-help Provide help to unprivileged
user
help Description of the
interactive help system
history Enable and control the
command history function
hold-character Define the hold character
insecure Mark line as 'insecure' for
LAT
international Enable international 8-bit
character support
ip IP options
ipv6 IPv6 options
keymap-type Specify a keymap entry to use
lat DEC Local Area
Transport (LAT) protocol-specific configuration
length Set number of lines on a
screen
location Enter terminal location
description
lockable Allow users to lock a line
logging Modify message logging
facilities
login Enable password checking
logout-warning Set Warning countdown for
absolute timeout of line
modem Configure the Modem
Control Line
monitor Copy debug output to the
current terminal line
motd-banner Enable the display of the MOTD
banner
nasi Netware Asynchronous
Services Interface
no Negate a command or
set its defaults
notify Inform users of output
from concurrent sessions
ntp Configure NTP
padding Set padding for a
specified output character
parity Set terminal parity
password Set a password
prc PRC commands
private Configuration options that
user can set will remain in effect
between terminal sessions
privilege Change privilege level for
line
refuse-message Define a refuse banner
rotary Add line to a rotary
group
rxspeed Set the receive speed
script specify event related
chat scripts to run on the line
session-disconnect-warning Set warning countdown for session-timeout
session-limit Set maximum number of sessions
session-timeout Set interval for closing
connection when there is no input traffic
special-character-bits Size of the escape (and other special)
characters
speed Set the transmit and
receive speeds
start-character Define the start character
stop-character Define the stop character
stopbits Set async line stop bits
telnet Telnet protocol-specific
configuration
terminal-type Set the terminal type
timeout Timeouts for the line
transport Define transport protocols
for line
txspeed Set the transmit speeds
vacant-message Define a vacant banner
width Set width of the display
terminal
x25 X25 protocol-specific
configuration
CSRv(config-line)#login
authentication ?
WORD
Use an authentication list with this name.
default
Use the default authentication list.
CSRv(config-line)#login
authentication ACCESS-1
CSRv(config-line)#authorization
?
arap For Appletalk Remote Access
Protocol
commands For exec (shell) commands
exec For starting an exec (shell)
reverse-access For reverse telnet connections
CSRv(config-line)#authorization
exec ?
WORD
Use an authorization list with this name
default
Use the default authorization list
CSRv(config-line)#authorization
exec ACCESS-1
CSRv(config-line)#accounting
?
arap
For Appletalk Remote Access Protocol
commands
For exec (shell) commands
connection
For connection accounting
exec
For starting an exec (shell)
resource
For resource accounting
CSRv(config-line)#accounting
exec ?
WORD
Use an accounting list with this name
default
Use the default accounting list
CSRv(config-line)#accounting
exec ACCESS-1
SSH to
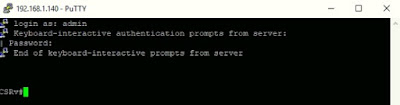
CSRv using ISE account: john-ise created earlier.
You can view RADIUS logs in ISE under Operations > RADIUS Livelog.
You're required to install Adobe Flash. Click on the red block icon to Allow Adobe Flash.
Open a new web browser and re-login to ISE.
Notice under the Home Dashboard > Authentication there's a Passed count of 2.
Go to
Operations > RADIUS Livelog.
Notice a
green check icon or successful login for the ISE RADIUS user john-ise. Click Details to view
more info.
A new web browser will open.
Go to Operations > Reports > ISE Reports > Endpoints and Users > Time Range: Today > Run.
Go to RADIUS Accounting > Time Range: Today > Run.
Click Details to view more info. A new web browser will open.
Go to RADIUS Authentication > Time Range: Today > Run.
Click Details to view more info. A new web browser will open.
Task 4: Configure Management Access AAA on Cisco ASA
Configure an AAA Server Group under Configuration > Device Management > Users/AAA > AAA Server Groups > Add.
Type AAA Server Group Name: RADIUS-1 > select Protocol: RADIUS > leave other settings in default > click OK.
Select RADIUS-1 (AAA Server Group) > under Servers in the Selected Group > click Add.
Select Interface Name: inside > type Server Name or IP Address: 192.168.1.1 > type the Server Secret Key: cisco (should be the same in ISE) > type Common Password: cisco > click OK.
You can verify AAA authentication to ISE by clicking Test > select Authentication > type Username: john-ise > type Password: Cisco123 > click OK.
Apply AAA on the ASA under Configuration > Device Management > Users/AAA > AAA Access.
Under Authentication tab > enable SSH > select Server Group: RADIUS-1 > Use LOCAL when server group fails is enabled by default.
Go to Authorization tab > Under Perform authorization for exec shell access > select Enable > Remote server.
Go to Accounting tab > enable SSH > Server Group: RADIUS-1 (default).
Click Apply. A pop-up message will appear. Click Yes to Continue.
Open PuTTY and SSH to ASA (192.168.1.1) using the john-ise ISE login account.
To view RADIUS logs in ISE, go to Operations > Reports > ISE Reports > RADIUS Accounting > Time Range: Today > Run.
Click Details to view more info. A new web browser will be opened.
Go to Operations > Reports > ISE Reports > RADIUS Authentication > Time Range: Today > Run.
Click Details to view more info. A new web browser will be opened.






















































































No comments:
Post a Comment